Dynamic authentication in secured wireless networks
A pre-configured, wireless device technology, applied in the field of information network security, can solve difficult and complex problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
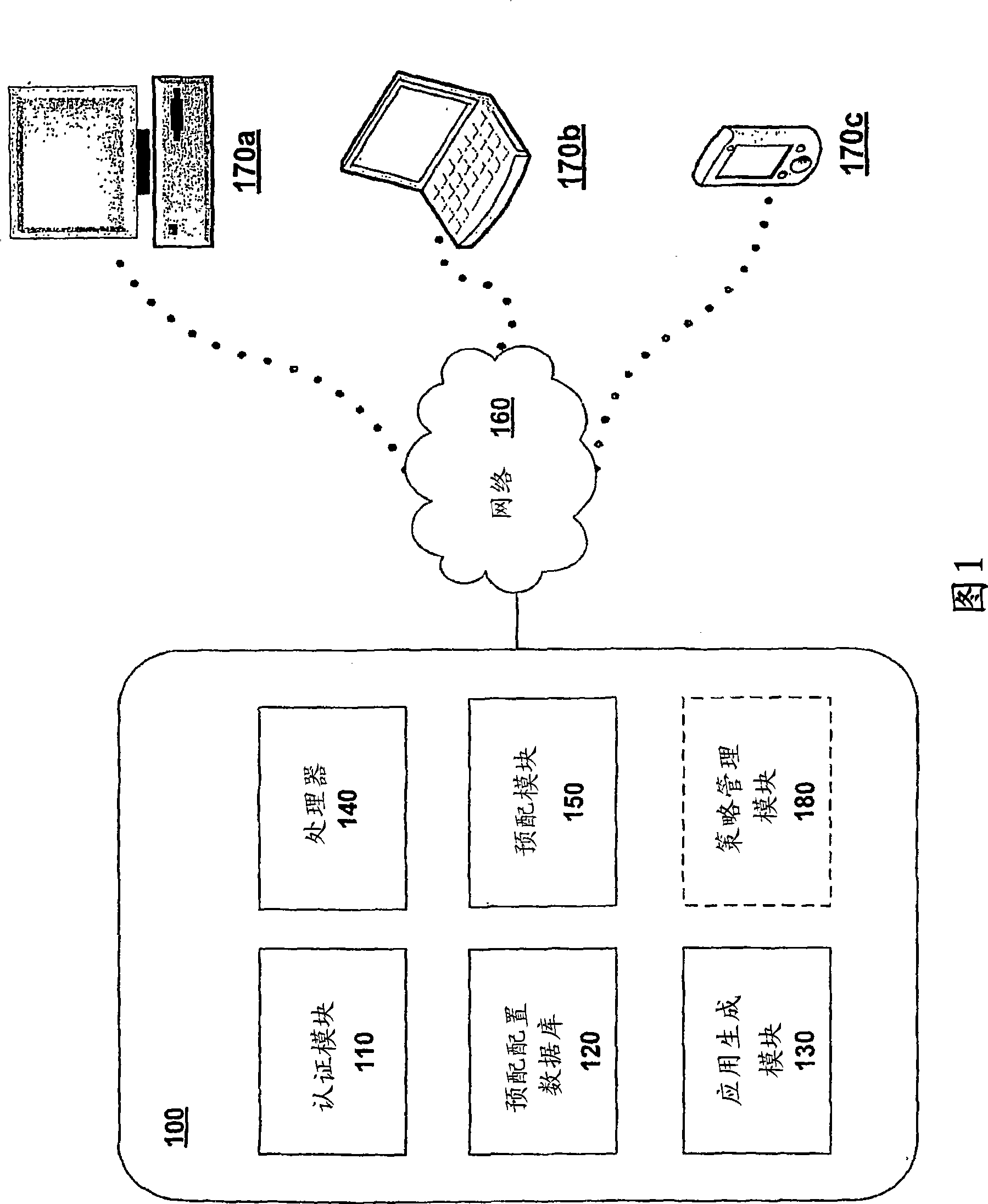
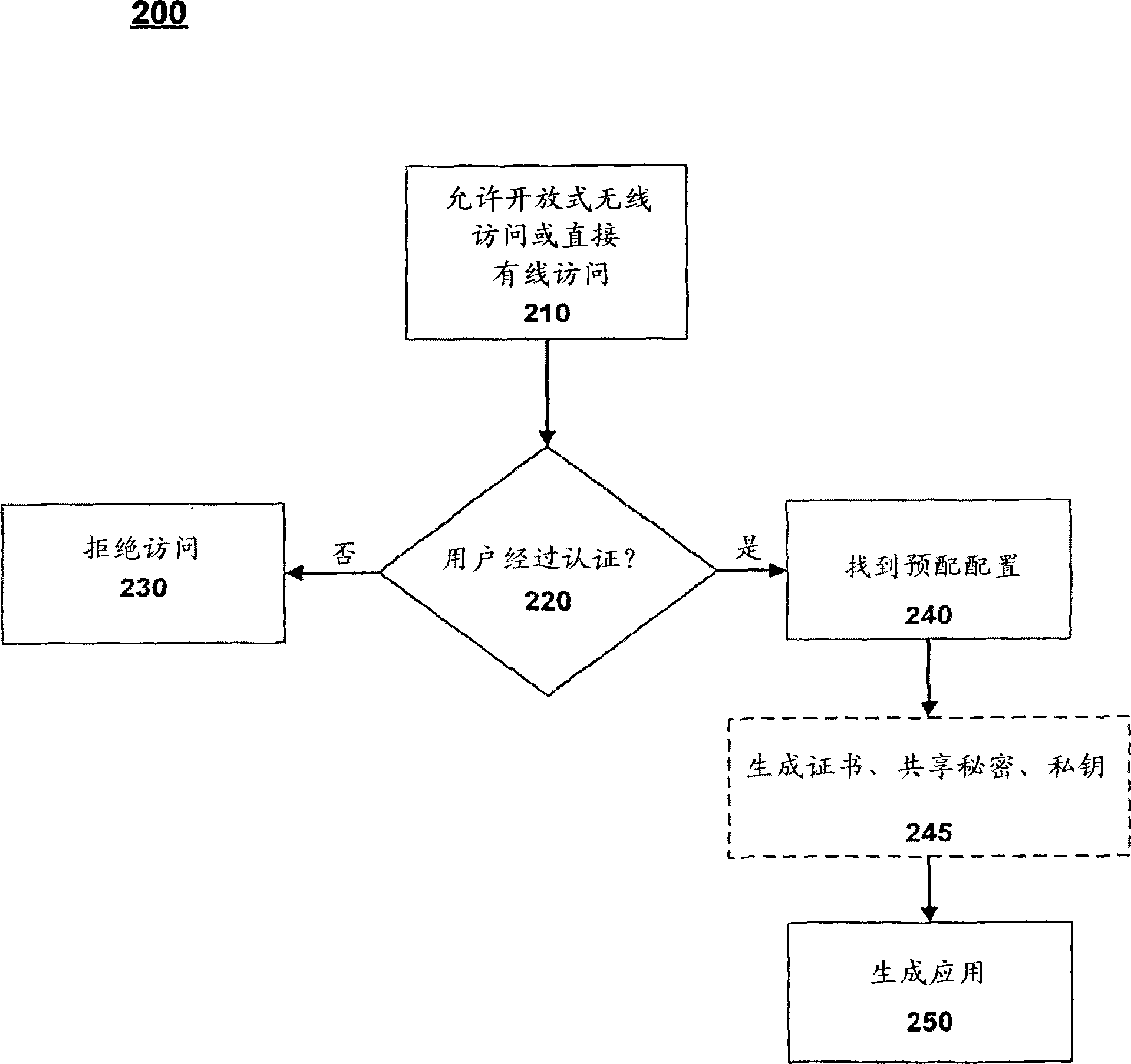
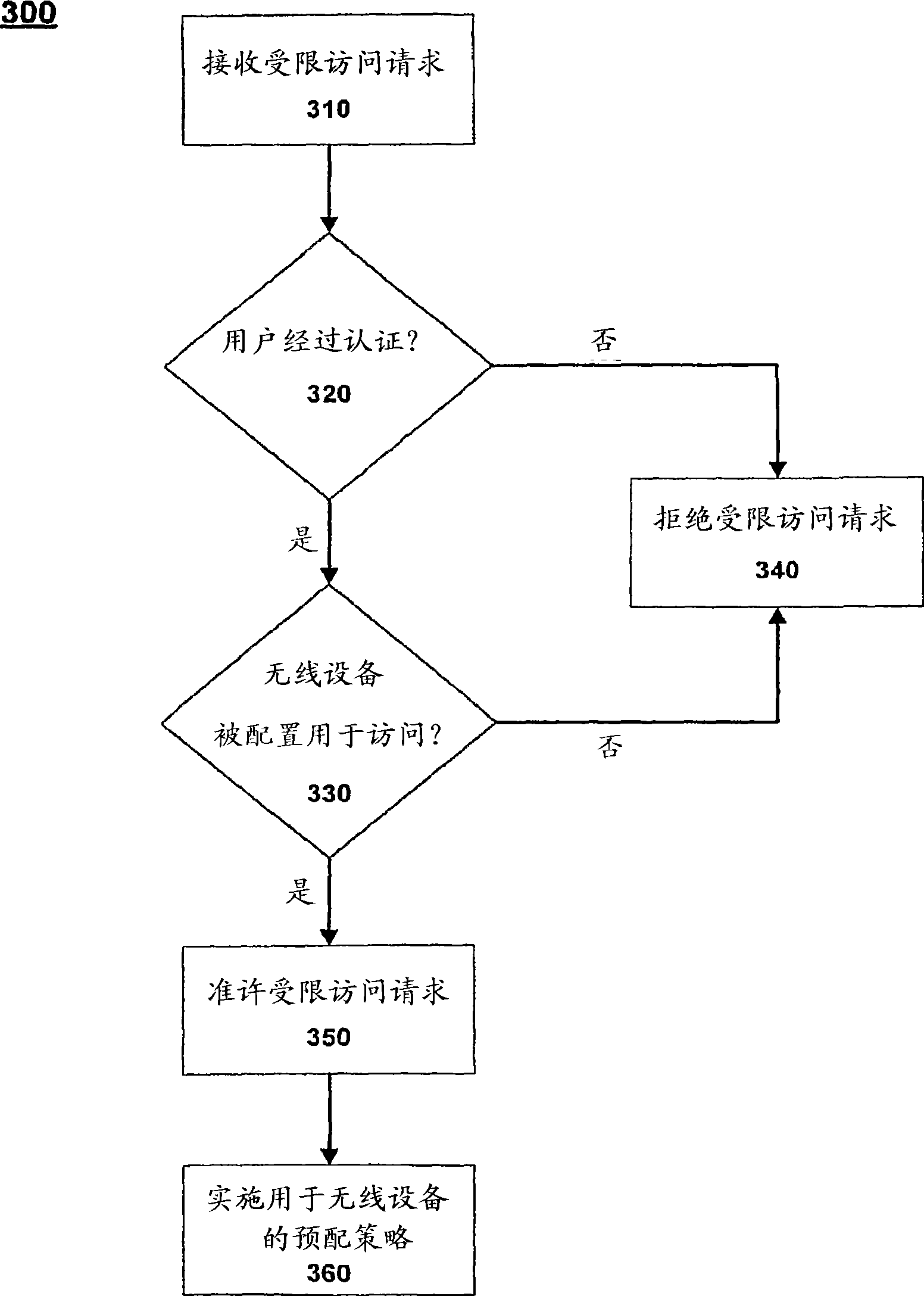
[0016] Embodiments of the invention include systems and methods for user-friendly, low-maintenance configuration of wireless devices to access restricted wireless networks. Users of wireless devices are allowed to connect to open wireless or wired networks. After the user is authenticated, an application can be generated that will allow the wireless device to connect to a protected or restricted wireless network. After the application is transmitted to and executed on the wireless device, the application configures the wireless device to access the restricted wireless network. The configuration, also referred to as a provisioning configuration, may be based on user information, wireless device information, or both. In some embodiments, the application is capable of configuring the wireless device to have access to multiple wireless networks.
[0017] 1 is an illustration of a system for provisioning wireless devices to access a restricted wireless network 160, according to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com