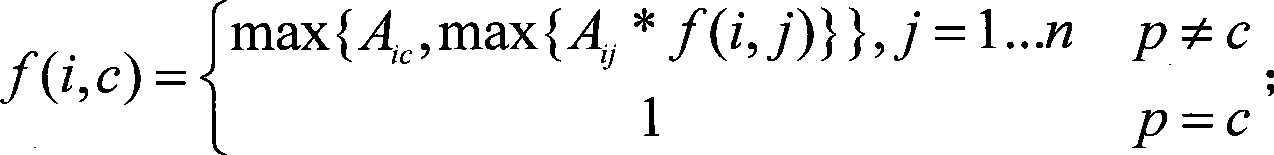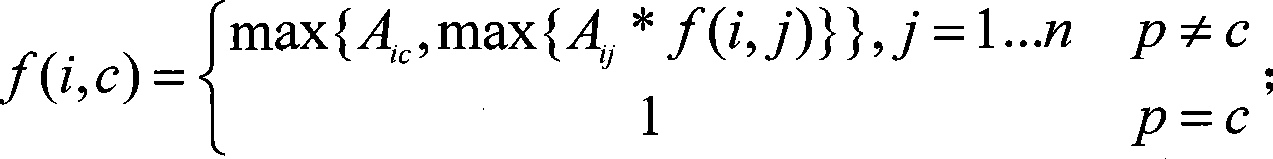System and method for digging related criminal suspect
A criminal suspect and associated technology, applied in the field of public security crime network analysis, can solve problems such as strong randomness, lack of data accumulation, and easy omission, and achieve the effects of strong correlation, good structure, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
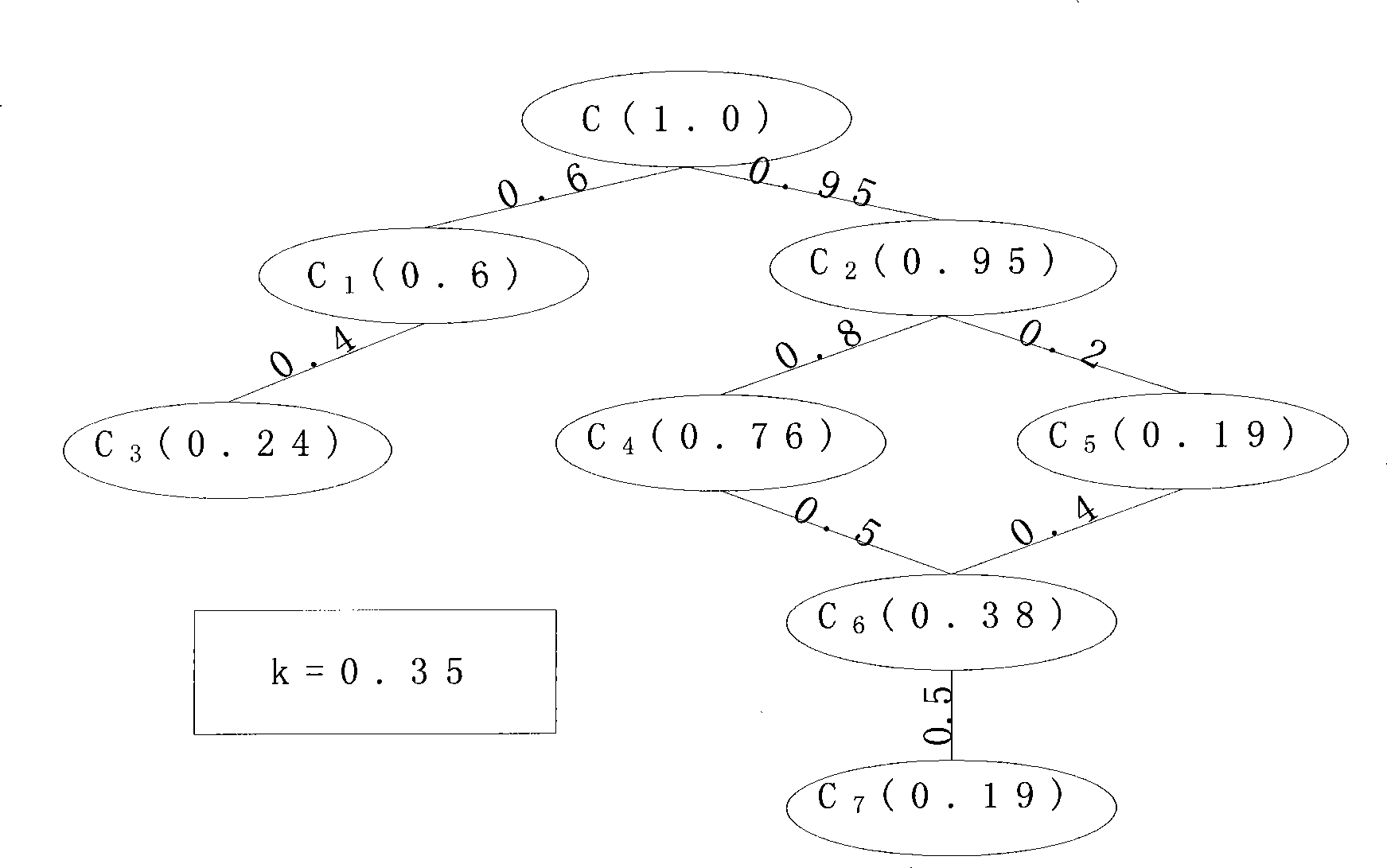
[0035] The system for mining related criminal suspects in the present invention mainly includes a related quantification module, a crime related function module and a node screening module.
[0036] 1. Associated quantization module
[0037] This module is responsible for the determination and quantification of association priorities. First of all, multiple public security business databases are integrated, and social personnel related information and criminals related information are combined to construct a criminal network; various related information between personnel are extracted from the network, such as: accomplices, hotel roommates, phone calls Call association, aircraft peer association, kinship association, colleague association, fellow country association, etc.; use the existing mature technology hierarchy analysis method (AHP) to determine the priority of each association in the network; map the priority to [0 , 1] space completes the quantification process; the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com