Method and equipment for implementing authentication mode smooth transition
An authentication method and a smooth transition technology. Applied in the field of communication, it can solve the problems of disconnection of network links, occupying network bandwidth, and advertising routing information in large quantities, so as to achieve the effect of solving network bandwidth.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
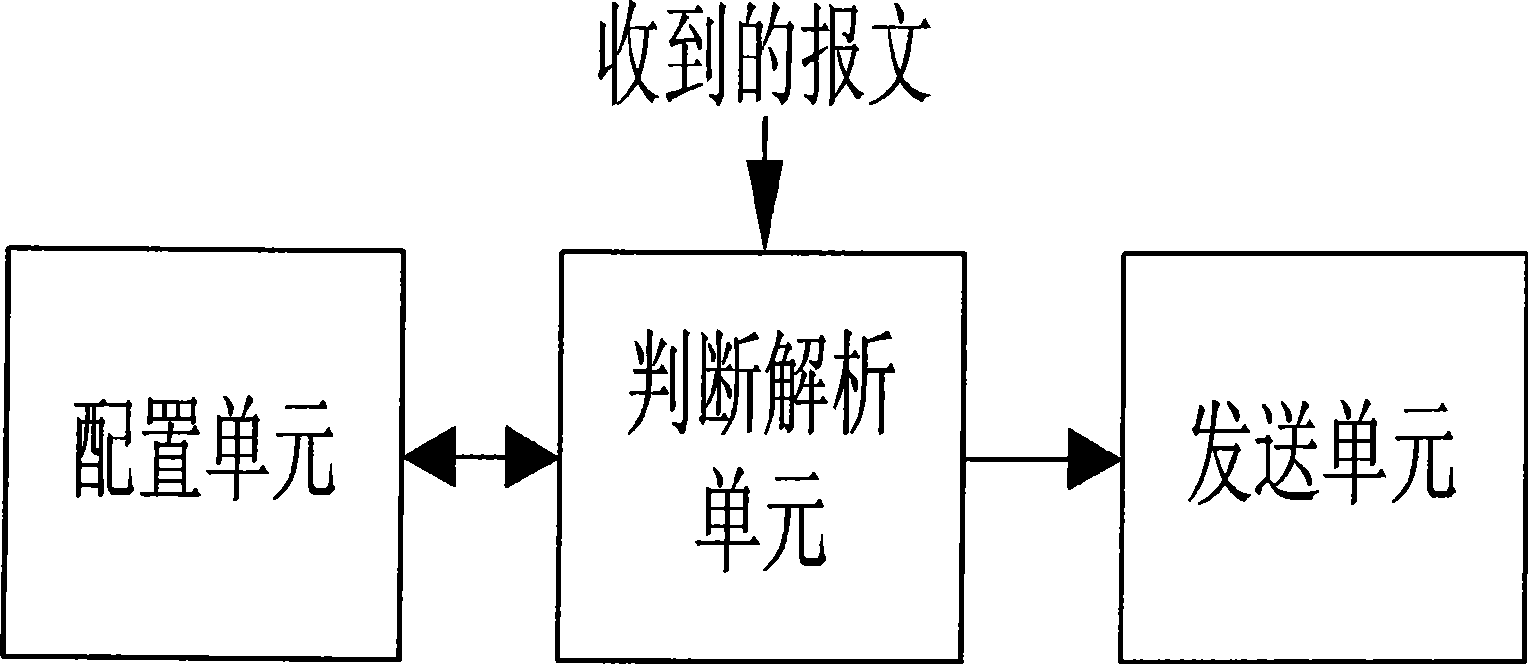
[0033] A device that realizes smooth transition of authentication methods, such as figure 2 As shown, it includes a configuration unit, a judgment analysis unit and a sending unit connected in sequence. The functions of each unit are described in detail below.
[0034] The configuration unit is used to store the first authentication method configured for the device, the second authentication method to be modified and the delay of the second authentication method, wherein the delay is used to determine the effective time of the second authentication method;
[0035] A judging and parsing unit for judging the effective authentication mode in the current device, and sending the effective authentication mode to the sending unit;
[0036] Specifically, the judgment analysis unit reads the delay of the second authentication method in the configuration unit, and judges whether the delay has arrived, and if it arrives, it considers that the authentication method currently in effect ...
Embodiment 2
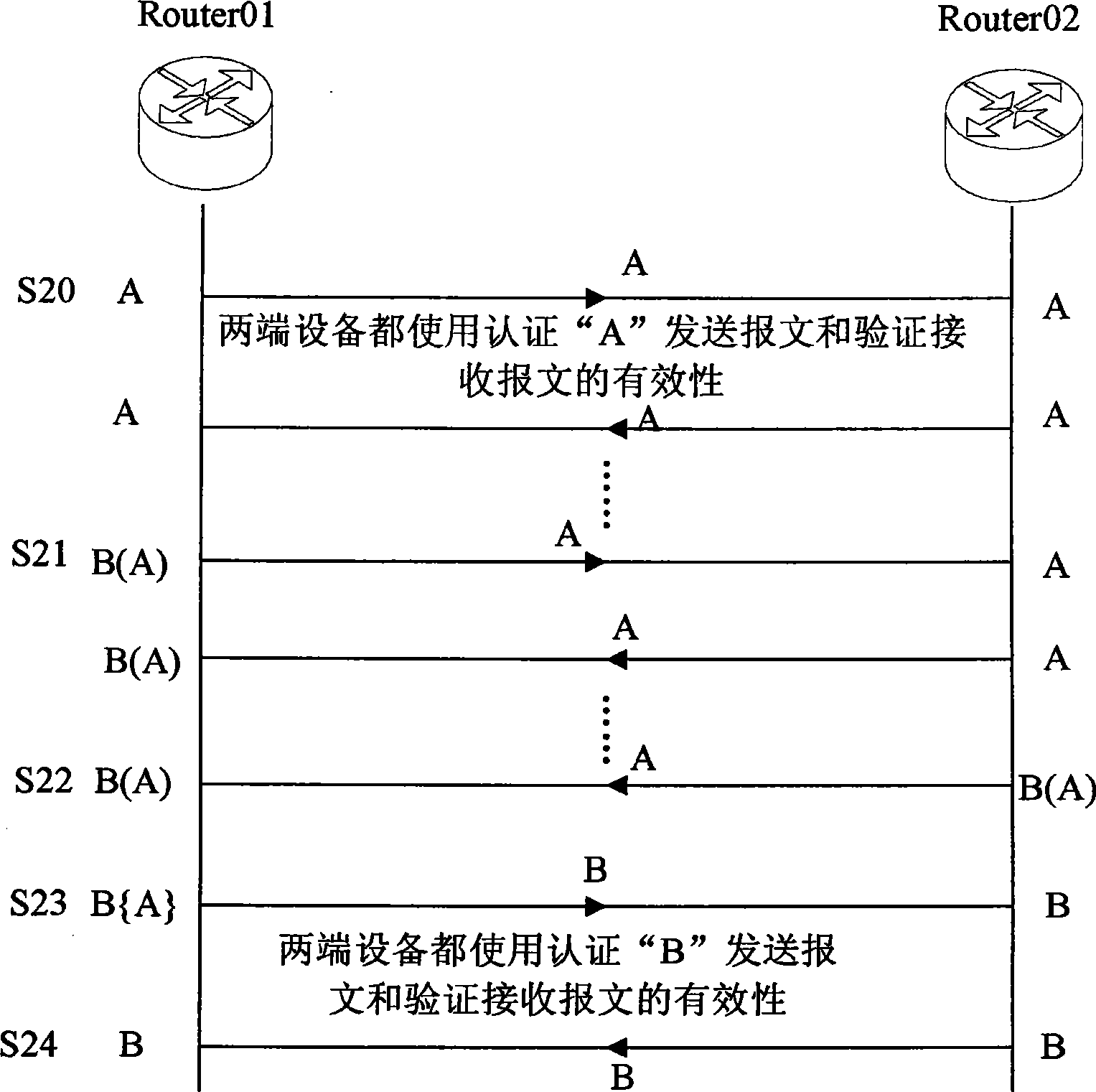
[0040] On the basis of Embodiment 1, it is assumed that there are two first network devices and second network devices establishing a BGP neighbor relationship, wherein authentication mode A is configured between the first network device and the second network device, and the first network device The device has received the newly configured authentication method B, and the delay of authentication method B is 10S. The following two network devices are taken as an example to illustrate the authentication process to achieve a smooth transition between the two network devices. image 3 shown, including the following steps:
[0041] Step 301: At time S20, the authentication mode configured by the first network device and the second network device is both A;
[0042] At this time, since the authentication methods are the same, normal communication between the two network devices can be realized;
[0043]Step 302: At time S21, for some reason, authentication method B is newly config...
Embodiment 3
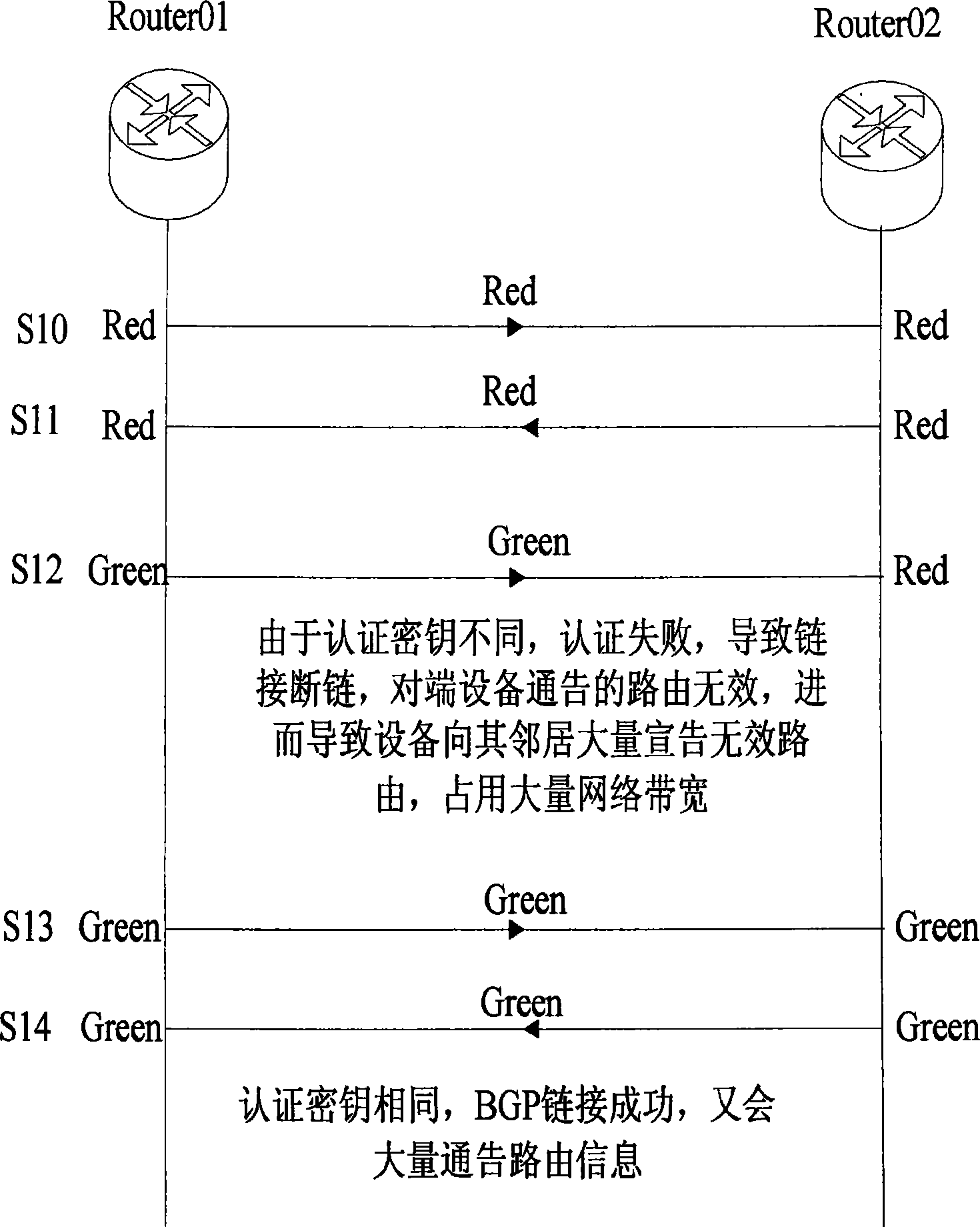
[0053] Introduce two network equipments that set up BGP neighbor again below, these two network equipments have all used MD5 authentication, and authentication key is all " Red ", according to the technical scheme of the present invention, the authentication key of these two network equipments is changed from " Red" to "Red". "Modified to "Green" process, such as Figure 4 shown, including the following steps:
[0054] Step 401: At time S30, when the network device router_01 sends a message to the network device router_02, the message uses the key "Red", and the network device router_02 uses the key "Red" to perform an authentication check after receiving the message, and the authentication is successful ;
[0055] Step 402: At time S31, when the network device router_02 sends a message to the network device router_01, the message uses the key "Red", and the network device router_01 uses the key "Red" to perform an authentication check after receiving the message, and the aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com