Communication method, device and system
A communication method and technology of a communication system, applied to the public key and key distribution of secure communication, can solve problems such as inability to encrypt headers, and achieve the effect of ensuring anonymity and protecting transmission security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
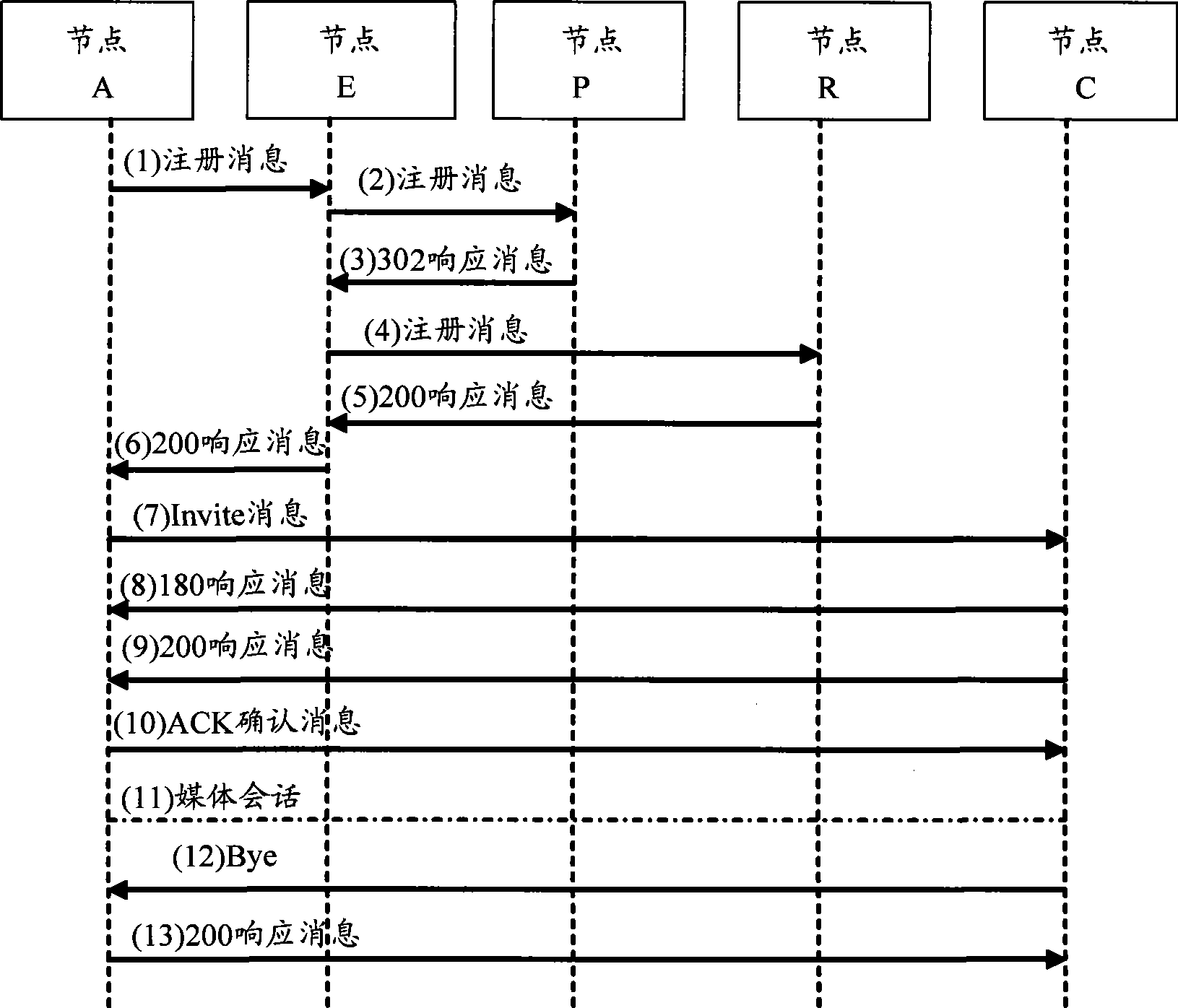
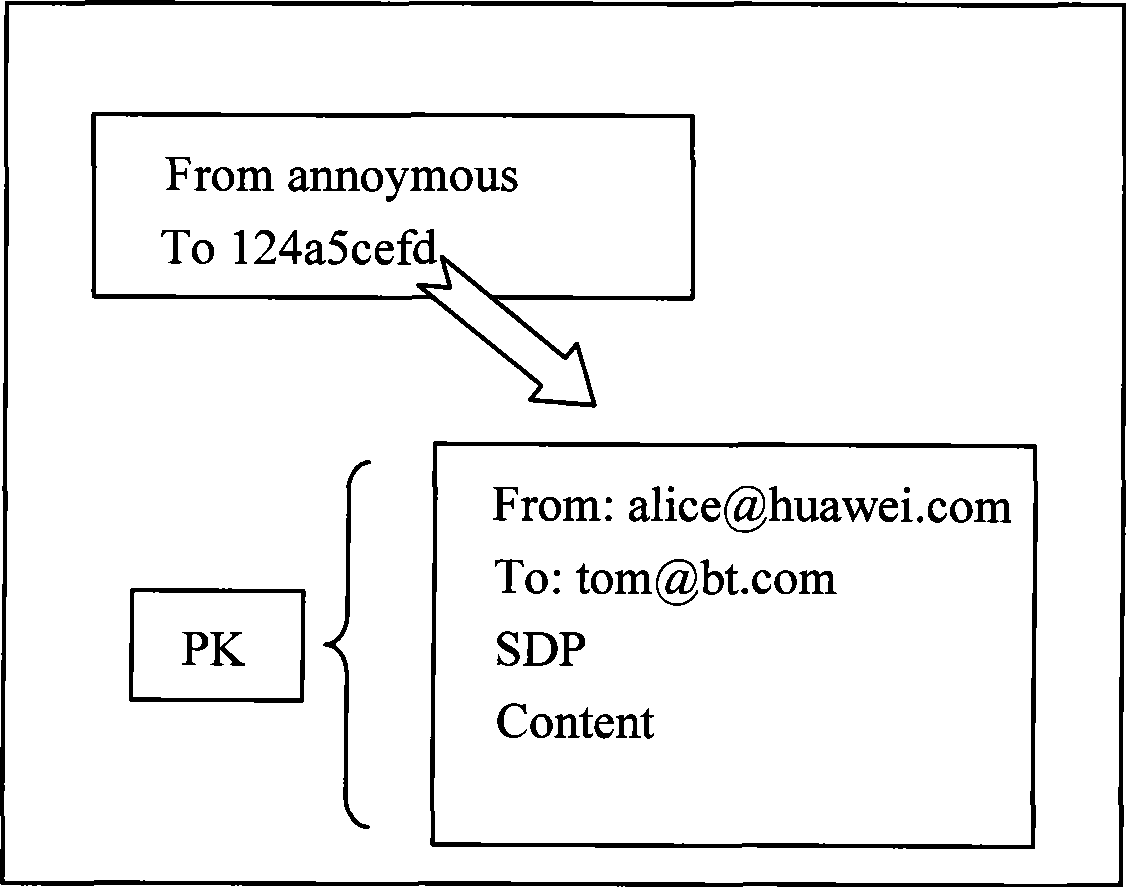
[0025] The embodiment of the present invention provides a communication method that uses the public key of the destination node to encrypt the transmitted data information. Since the transit node does not know the private key of the destination node, the data information cannot be decrypted, and only the destination node can access the data. The information is decrypted using the private key of the destination node, so as to realize the anonymous transmission of the communicating parties to the transit node and ensure the security of communication. The embodiment of the present invention takes communication in a P2P network as an example for description.
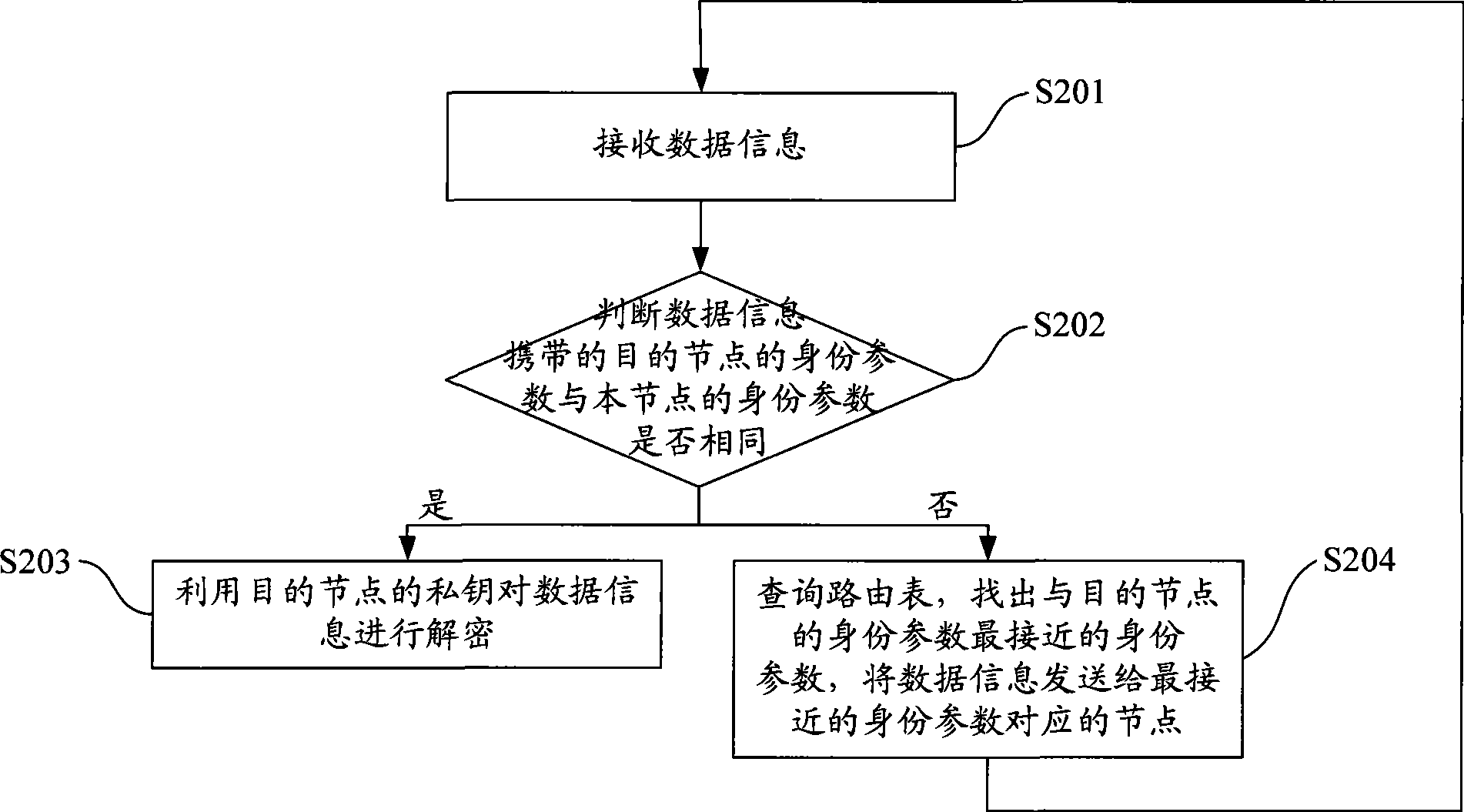
[0026] Such as figure 2 Shown is a flowchart of a communication method according to an embodiment of the present invention, which specifically includes the following steps:
[0027] Step S201: Receive data information, which is information encrypted with the public key of the destination node. When the source node sends data in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com