Security control method and system thereof
A technology of safety control and safety mode control, applied in the field of safety control, method and system thereof, can solve the problem of not having measures to ensure the safety of the startup process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
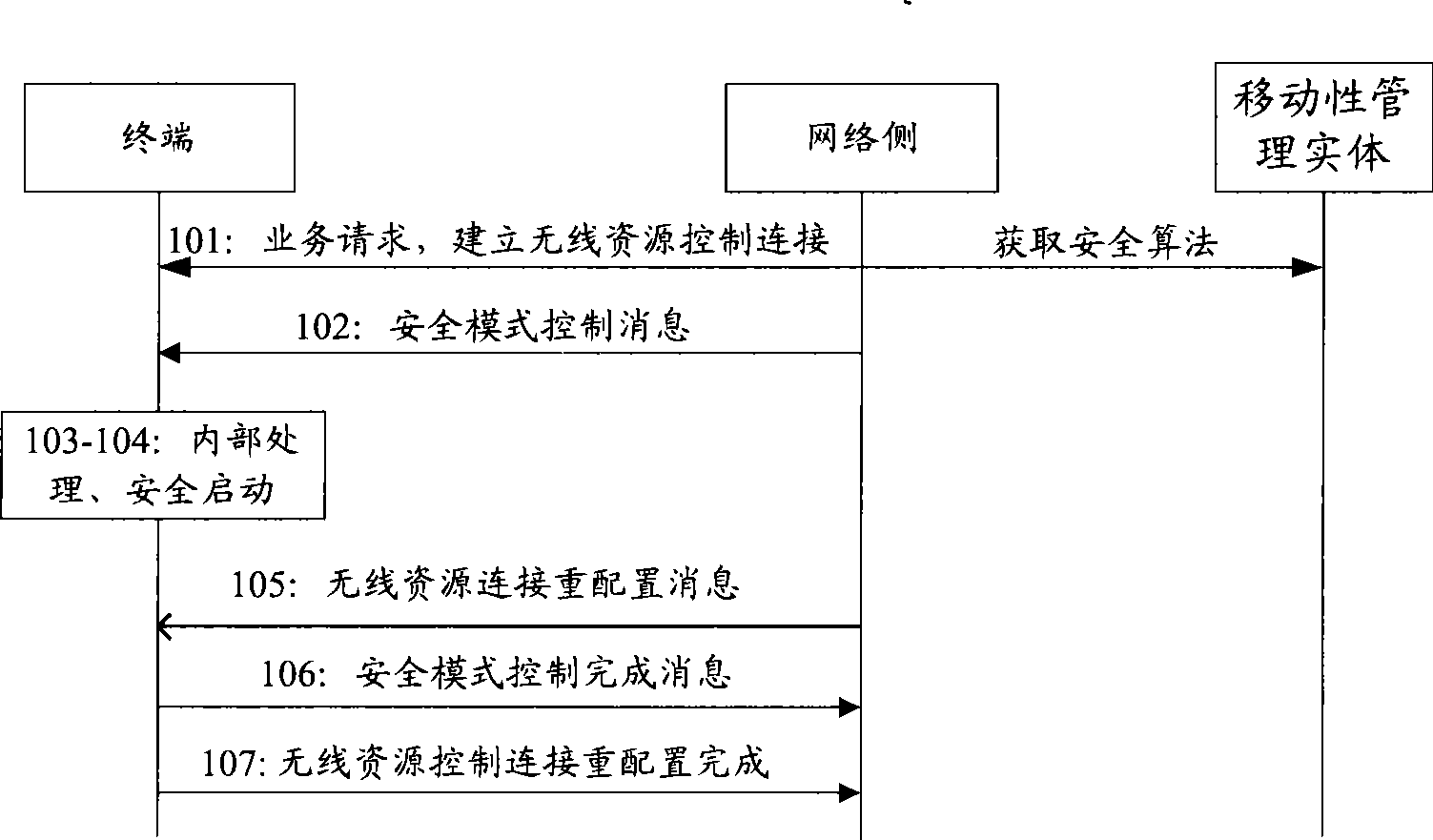
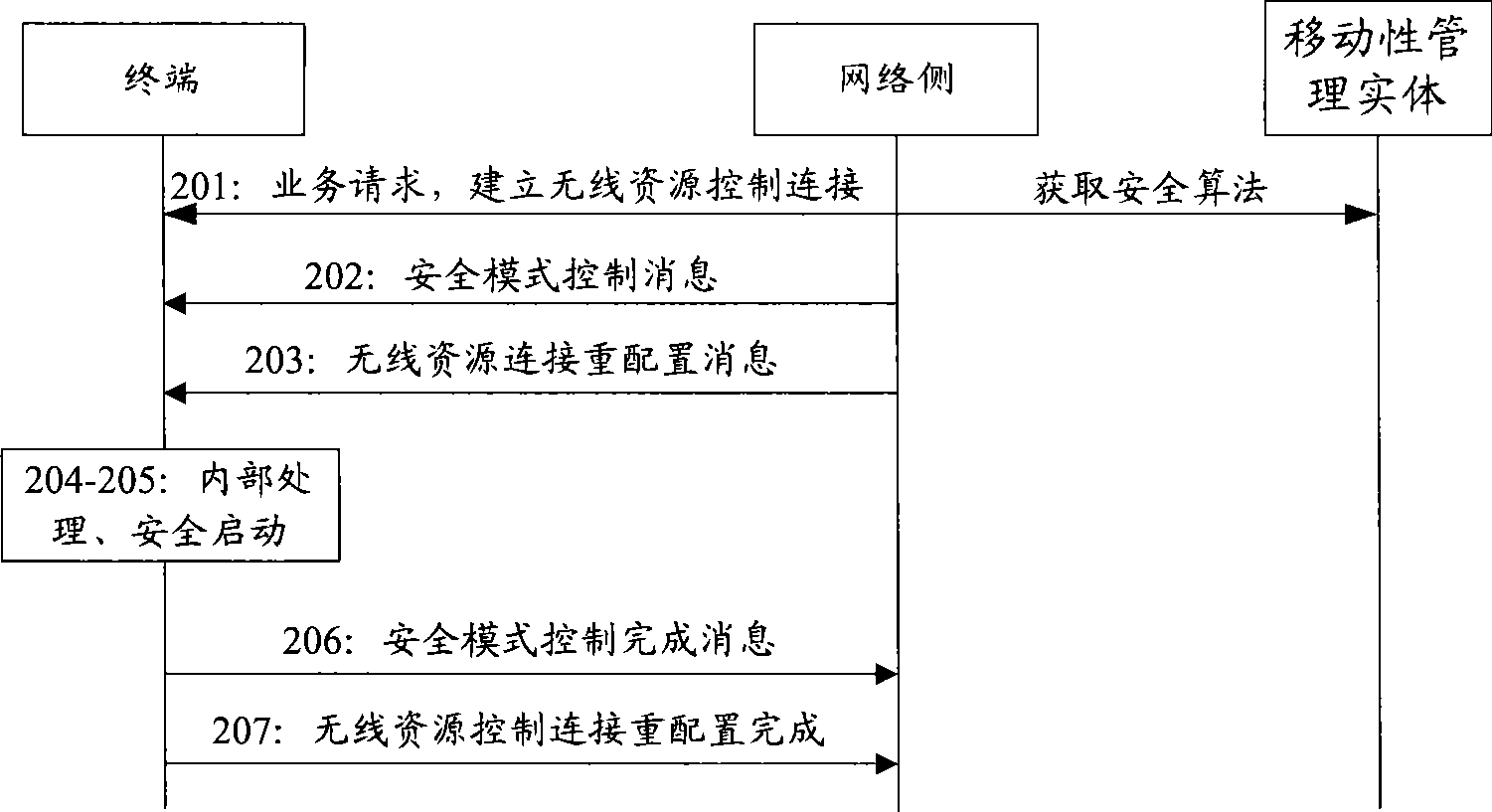
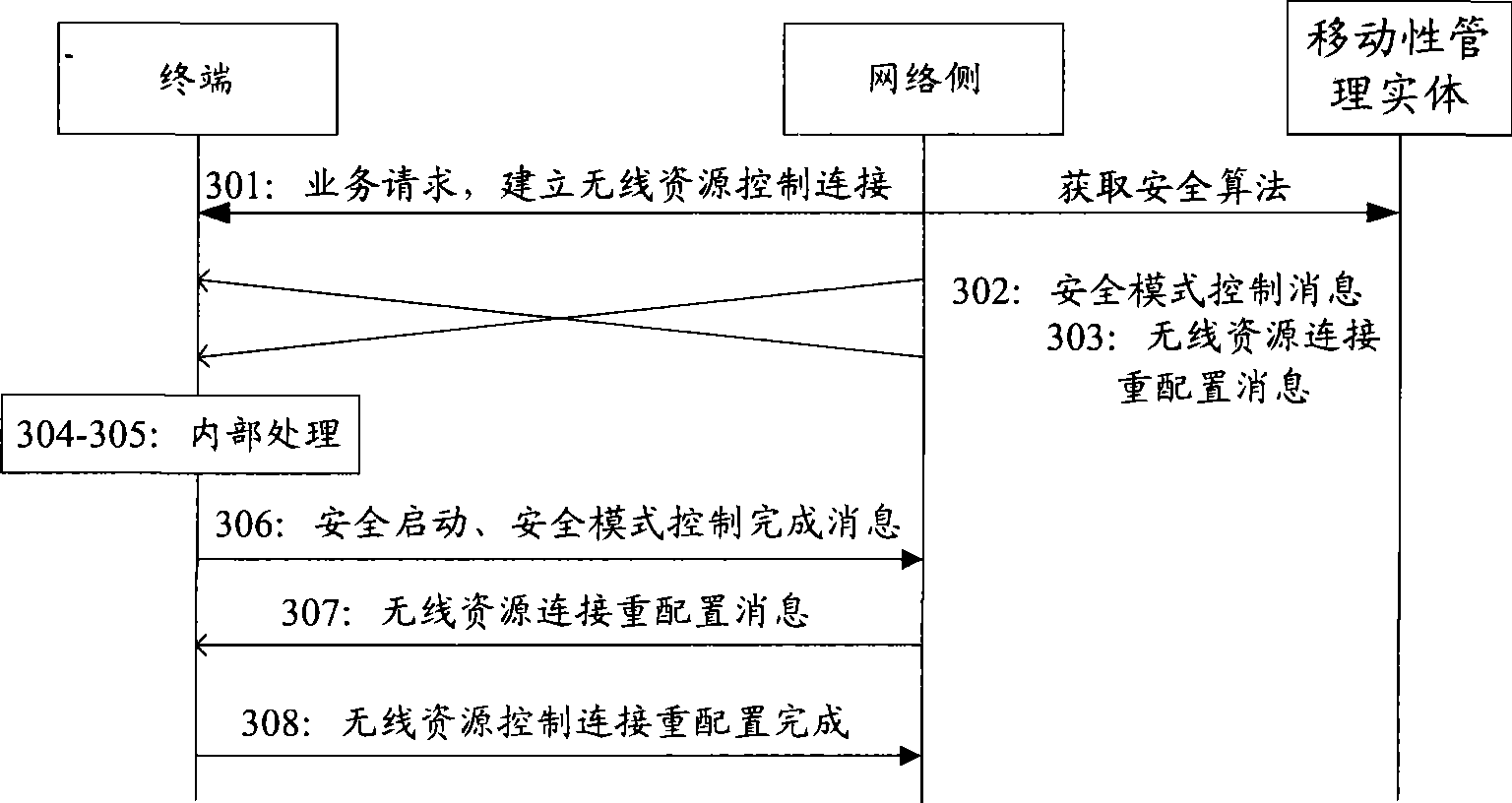
[0084] Example 1, see Figure 5 , a flow chart for selecting a security algorithm for a mobility management entity:
[0085] S501: The terminal sends a radio resource control connection request to the network side.
[0086] S502: The network side sends a radio resource control connection establishment message to the terminal.
[0087] S503: The terminal sends a non-access stratum service request to the network side.
[0088] S504: The network side sends an initial context message or a network-side security capability message to the mobility management entity.
[0089] S505: The mobility management entity selects a security algorithm.
[0090] S506: The mobility management entity returns an initial context response message to the network side, and the message carries security algorithm information. Steps 504 to 506 may also be that the network side obtains relevant security algorithm information through a dedicated security capability information transmission message. Includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com