Use case diagram detection method based on attack mode
A detection method and a technology of use case diagrams, which are applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as hidden safety hazards, and achieve the effect of reducing development costs, improving reliability and development efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
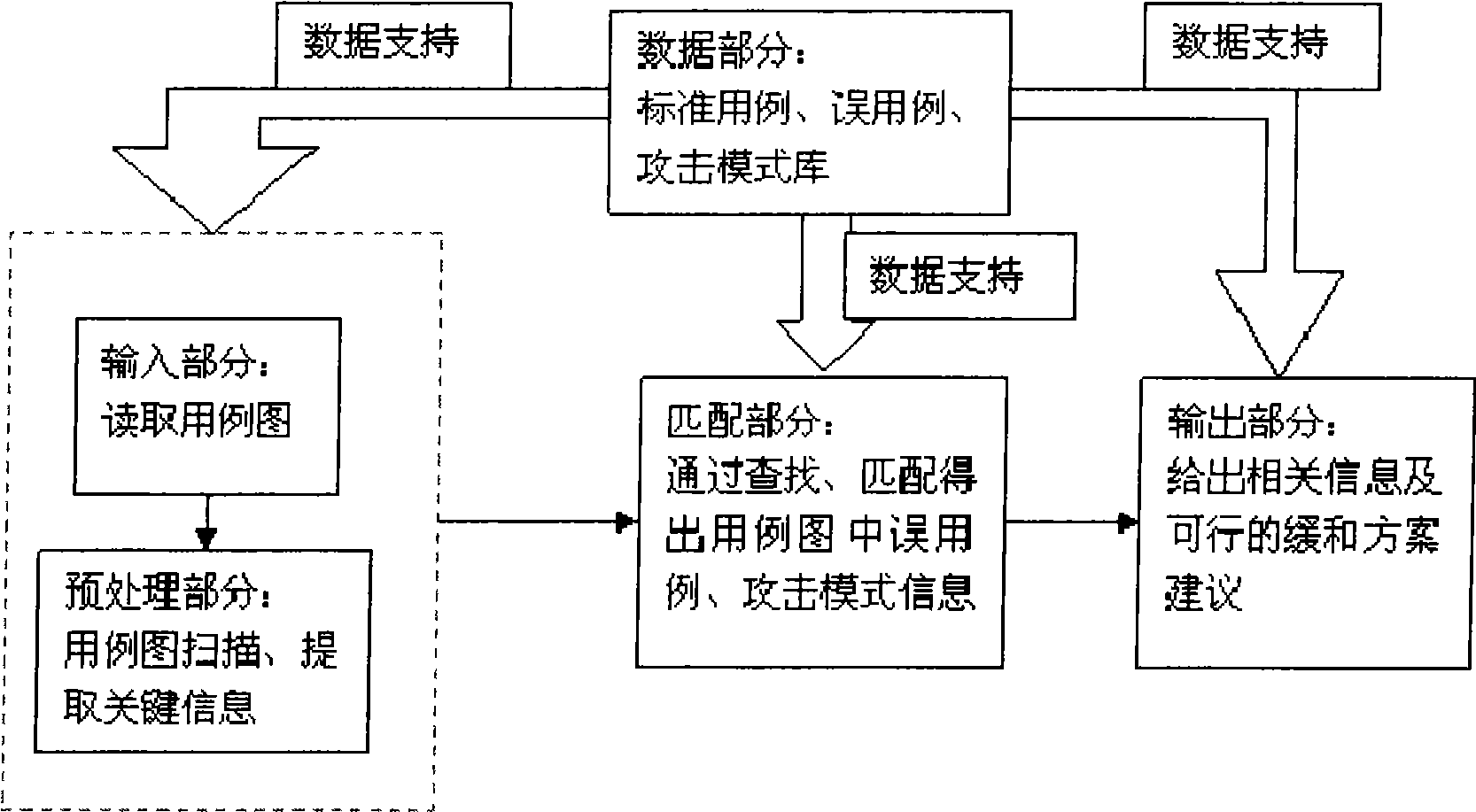
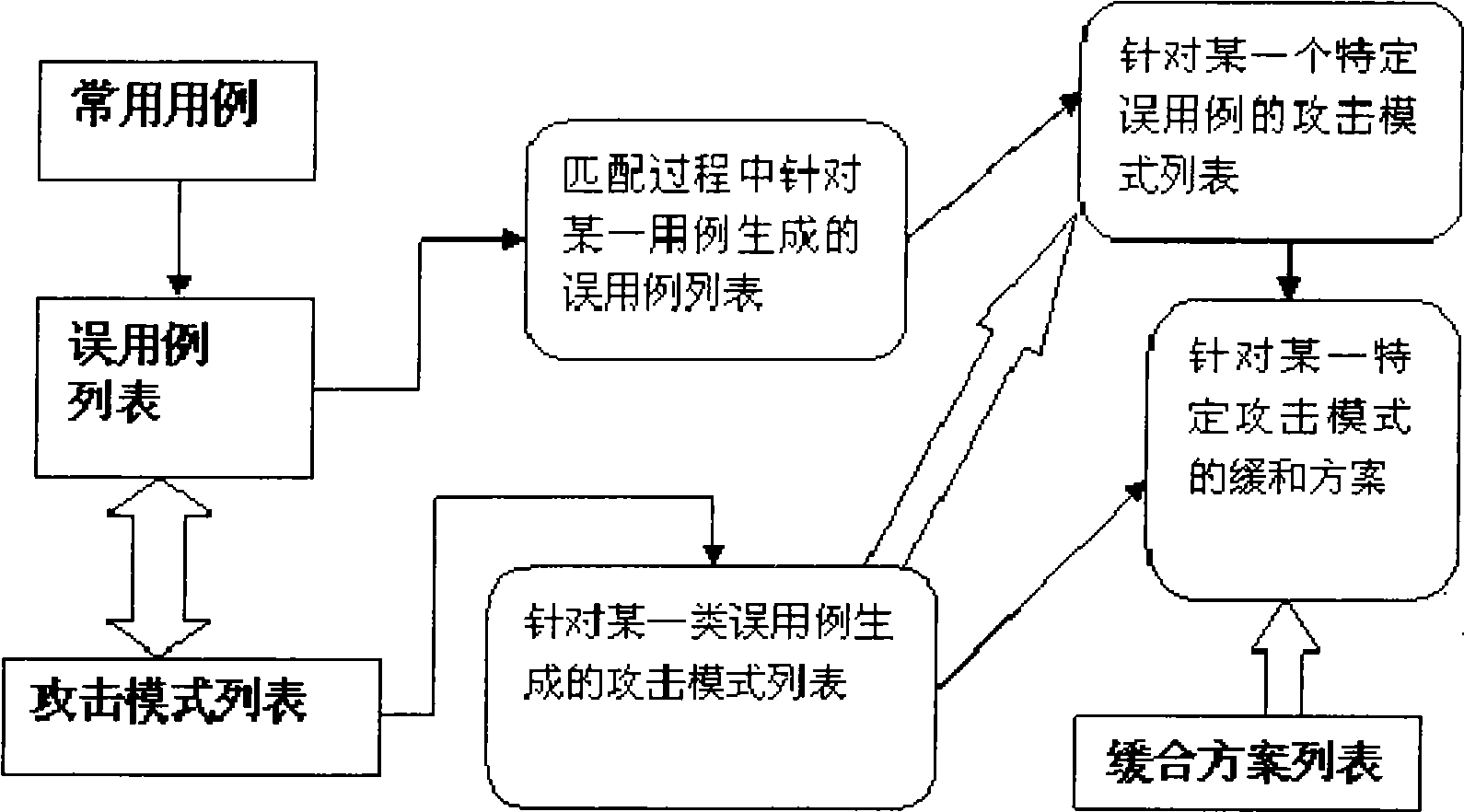
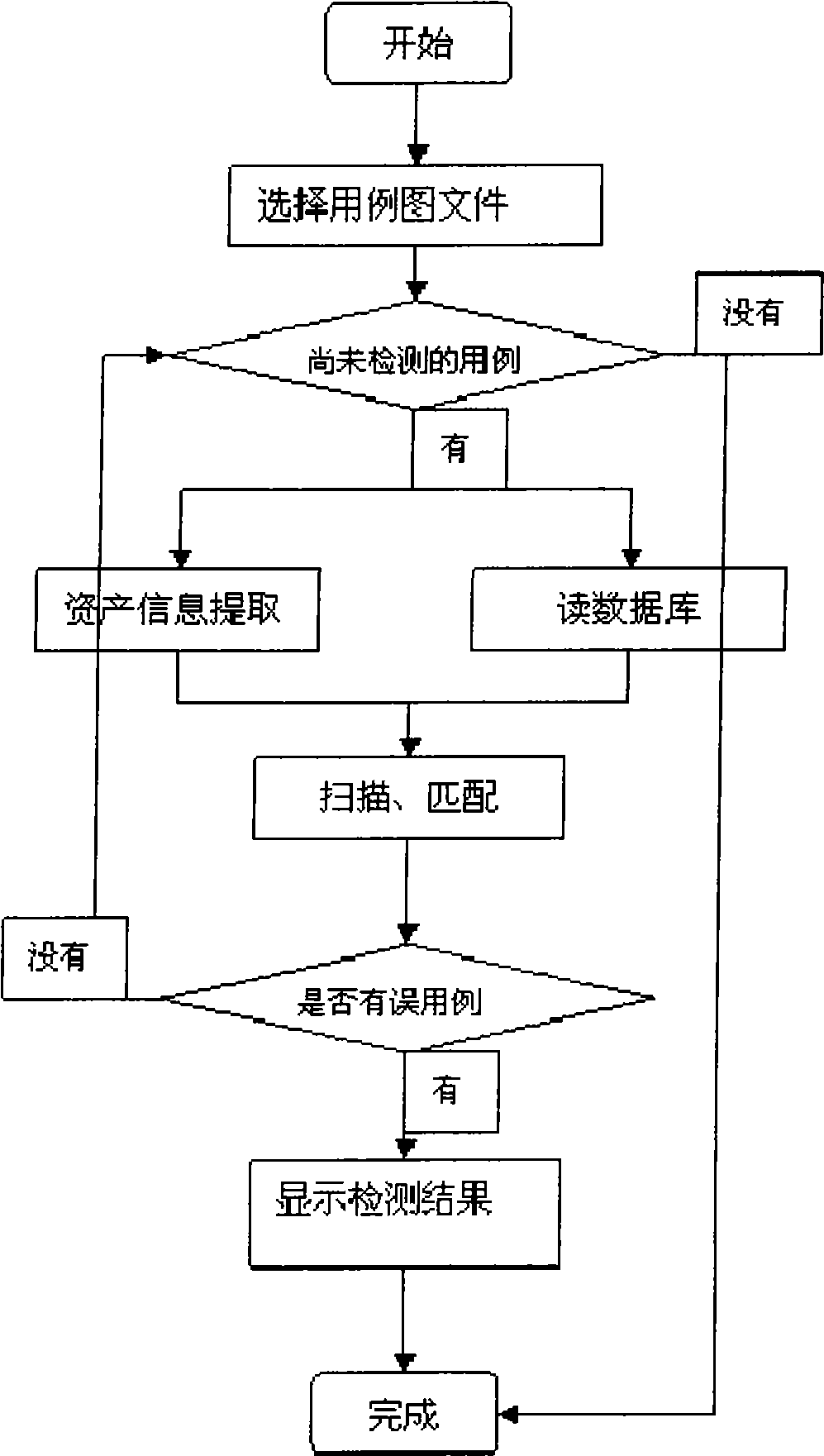
[0019] What the present invention needs to do is to classify existing common use cases, misuse cases, attack modes and mitigation schemes, and establish corresponding associations among them. On this basis, a method is proposed to obtain the implicit misuse cases and attack modes in the software system by analyzing the use case diagram, and further proposes an optional mitigation scheme to improve the software design.
[0020] Specifically, it includes the following aspects:
[0021] 1. Build an effective attack pattern library: the library briefly lists the names, descriptions, corresponding misuse cases, and optional mitigation solutions of existing attack patterns. More importantly, include the necessary mappings.
[0022] 2. Asset information extraction: extract relevant asset information from the use case diagram provided by the user (software designer, especially the requirement analyst). The selection of the extraction target should match the name and summary descript...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com