Method for preventing empty integrity protection algorithm from being used in normal communication and system thereof
A technology for integrity protection and normal communication, which is applied in the field of access security mechanisms in mobile communication systems, and can solve problems such as deception and communication without security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
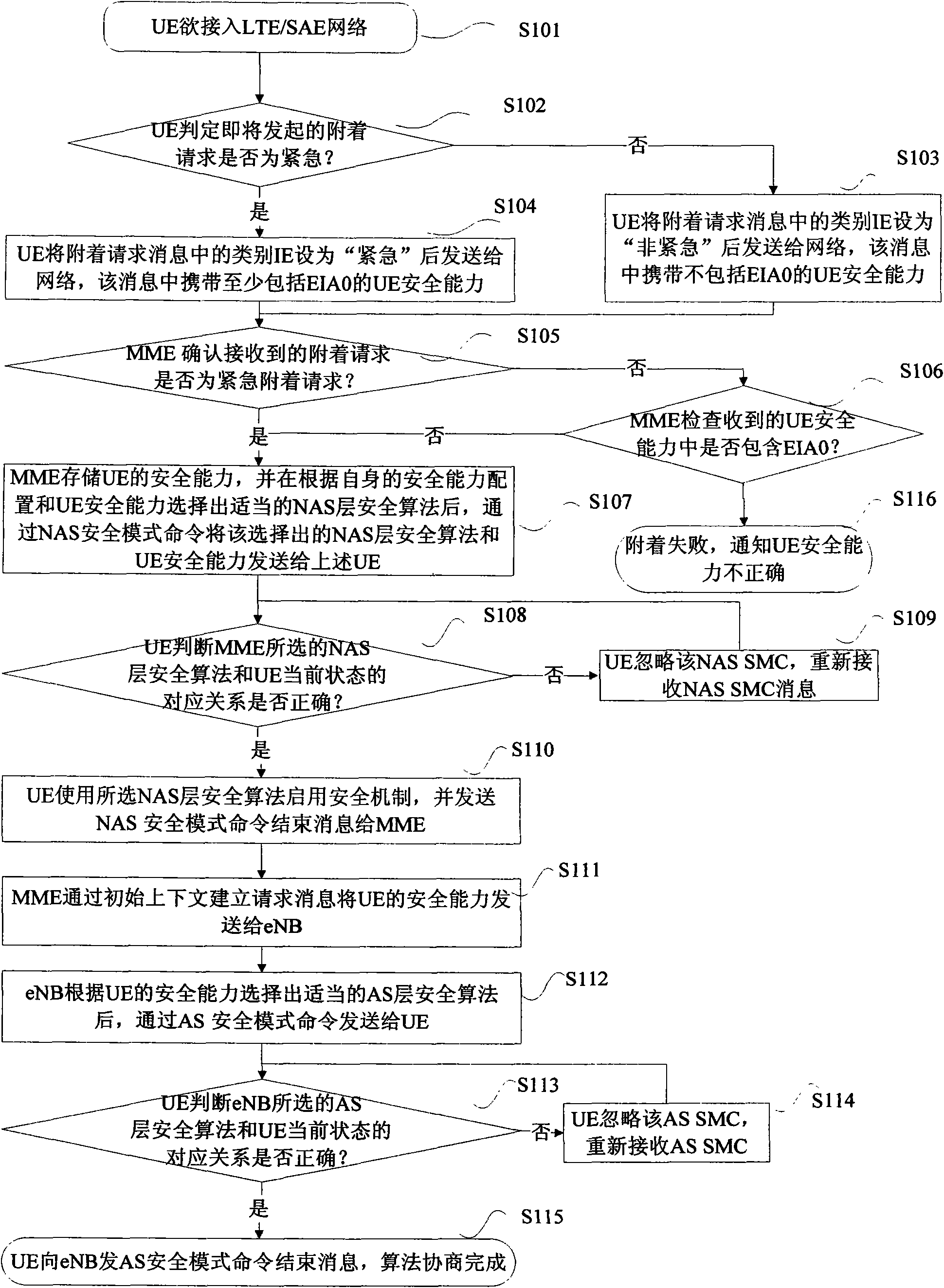
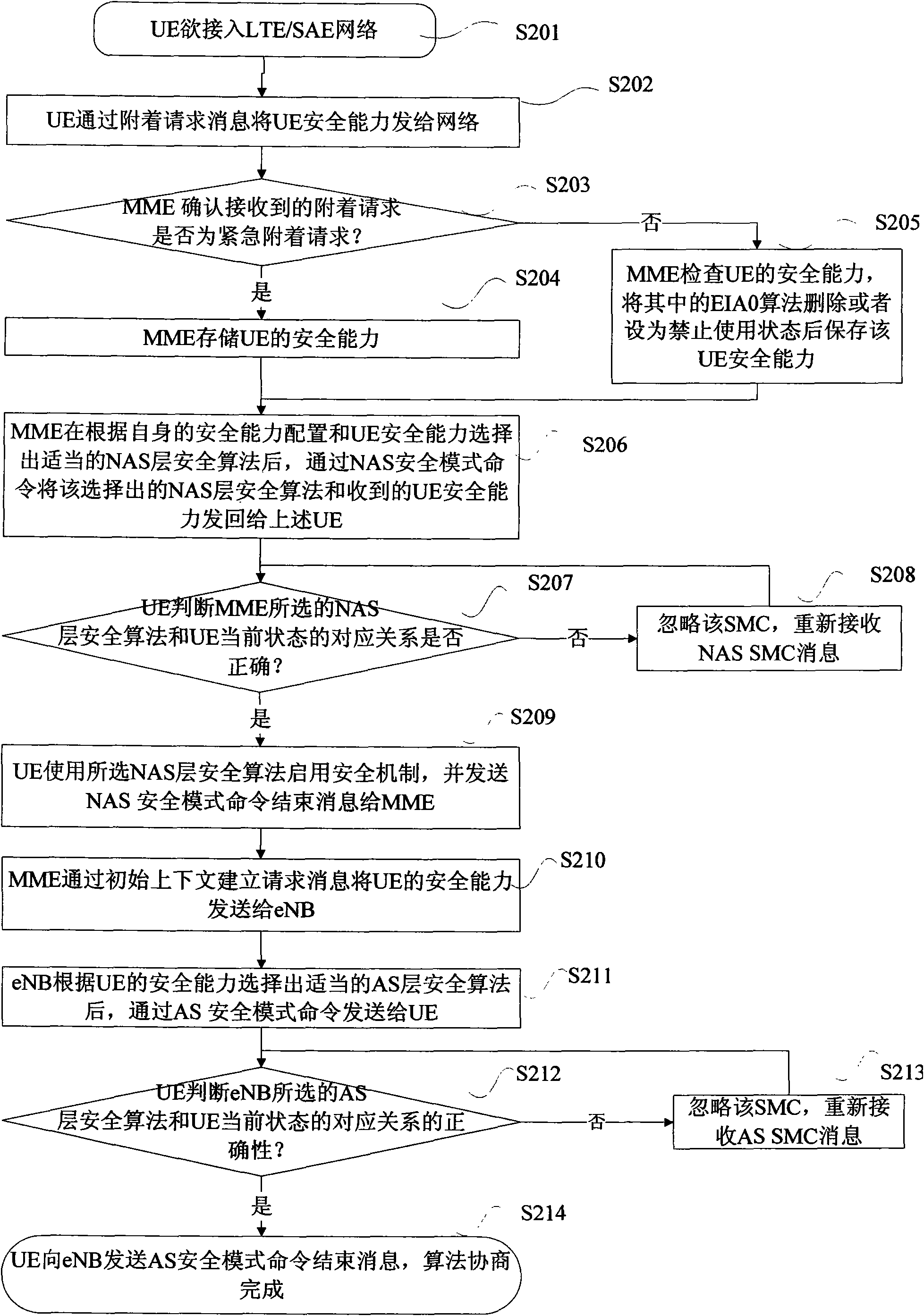
[0062] figure 1 It shows the implementation flow chart of the first embodiment of the UE security capability negotiation when the UE accesses the LTE / SAE network, including the following steps:
[0063] Step S101, the UE intends to access the LTE / SAE network;
[0064] Step S102, the UE judges whether the attach request to be initiated is an emergency attach request or a normal attach request. The judgment method is: if the UE is in an unauthenticated service-restricted state, and the number dialed by the user is an emergency number, the attach request to be initiated is considered If the request is an emergency attachment request, execute step S103; otherwise, consider the upcoming attachment request as a normal (or non-emergency) attachment request, and execute step S104;
[0065] Step S103, the UE sets the type information element (Information Element for short: IE) in the attach request message to "emergency" and sends it to the network. The message carries the UE security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com