Method and system for distributing service secret keys
A service key and service technology, which is applied to key distribution, can solve the problems of prolonging the delay of users waiting for service keys, increasing the burden on the server, and the huge amount of service keys. Effects of performance requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
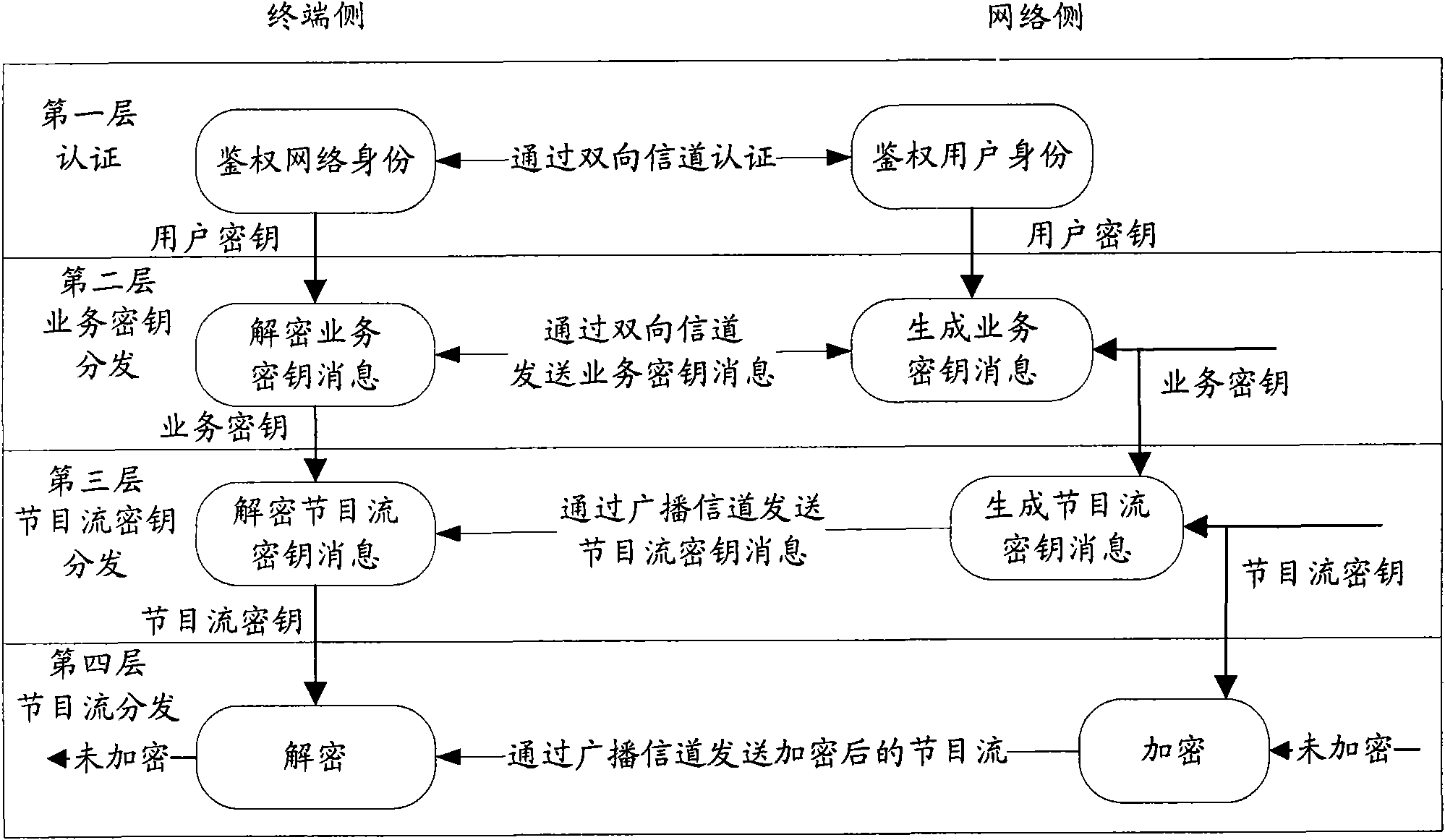
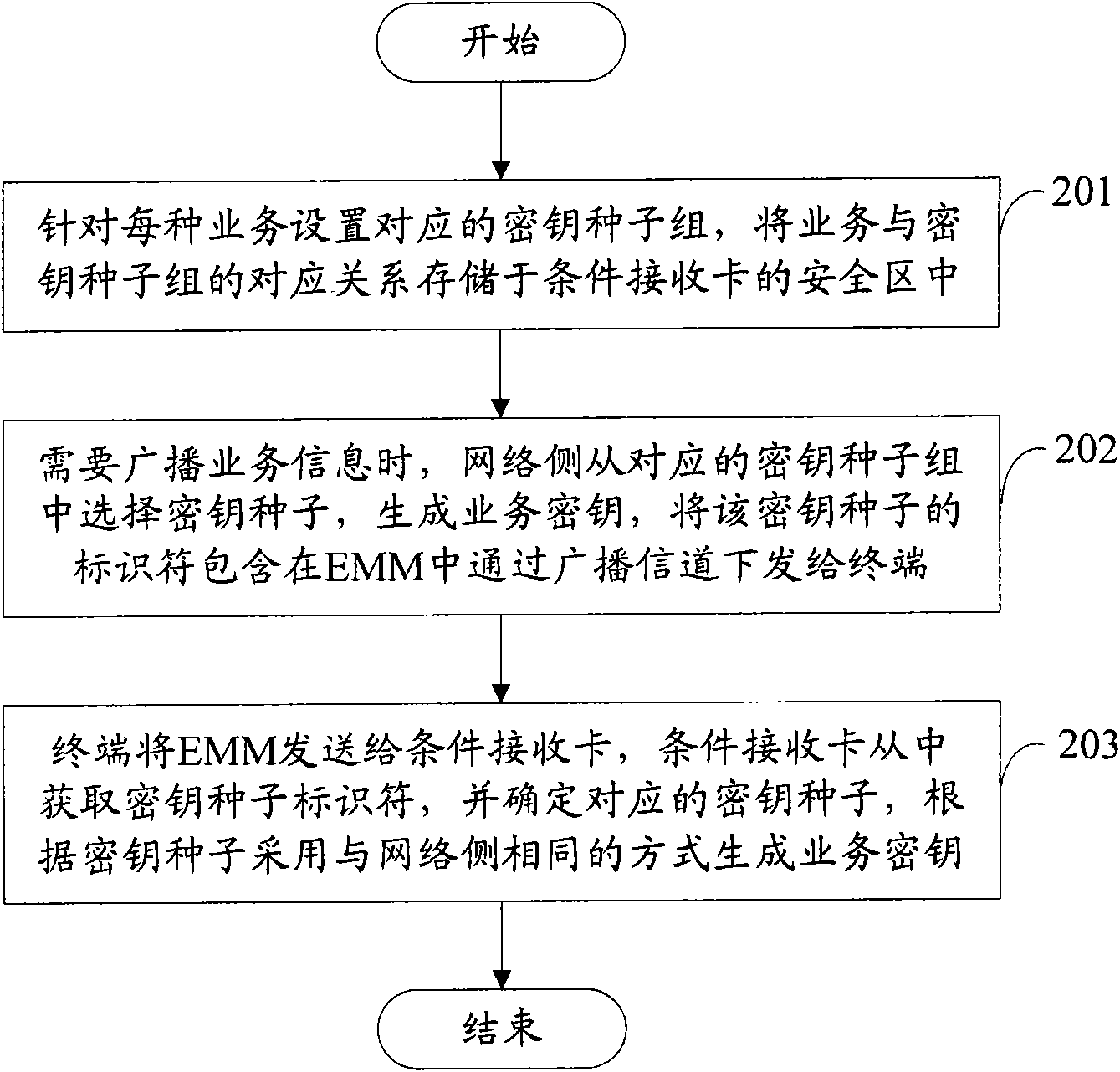
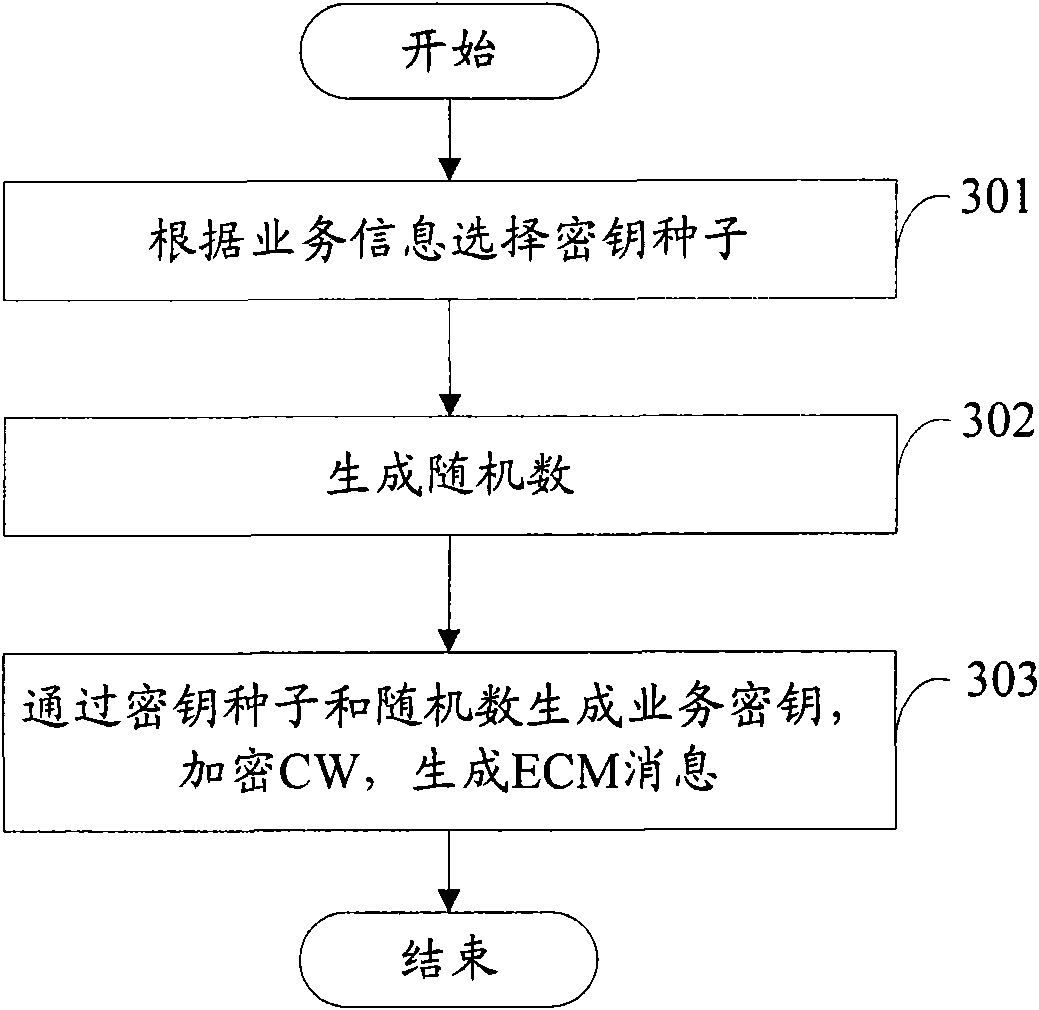
[0057] The main idea of the present invention is: set the key seed group corresponding to each service in advance, and store the corresponding relationship between the service and the key seed group in the security area of the conditional access card; Randomly select a key seed from the corresponding key seed group when keying, and include the identifier of the selected key seed in the EMM and send it to the terminal. The terminal sends the EMM to the conditional access card, and the conditional access card The corresponding relationship between the stored service and the key seed group, and the identifier of the key seed selected when the network side generates the service key determine which key seed is used to generate the service key, so that the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com