Method and system for automatically controlling flow of peer-to-peer networking service
A technology of flow control and flow control strategy, applied in the direction of transmission system, digital transmission system, data exchange network, etc., can solve the problems of waste of network resources, interference, single restriction method, etc., achieve good implementation flexibility and applicability, avoid wasteful effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to solve the disadvantages of the traditional technical solutions, the present invention further elaborates a P2P automatic flow control method and system of the present invention through the following specific examples. The specific implementation is described in detail below, but it is not intended to limit the present invention.
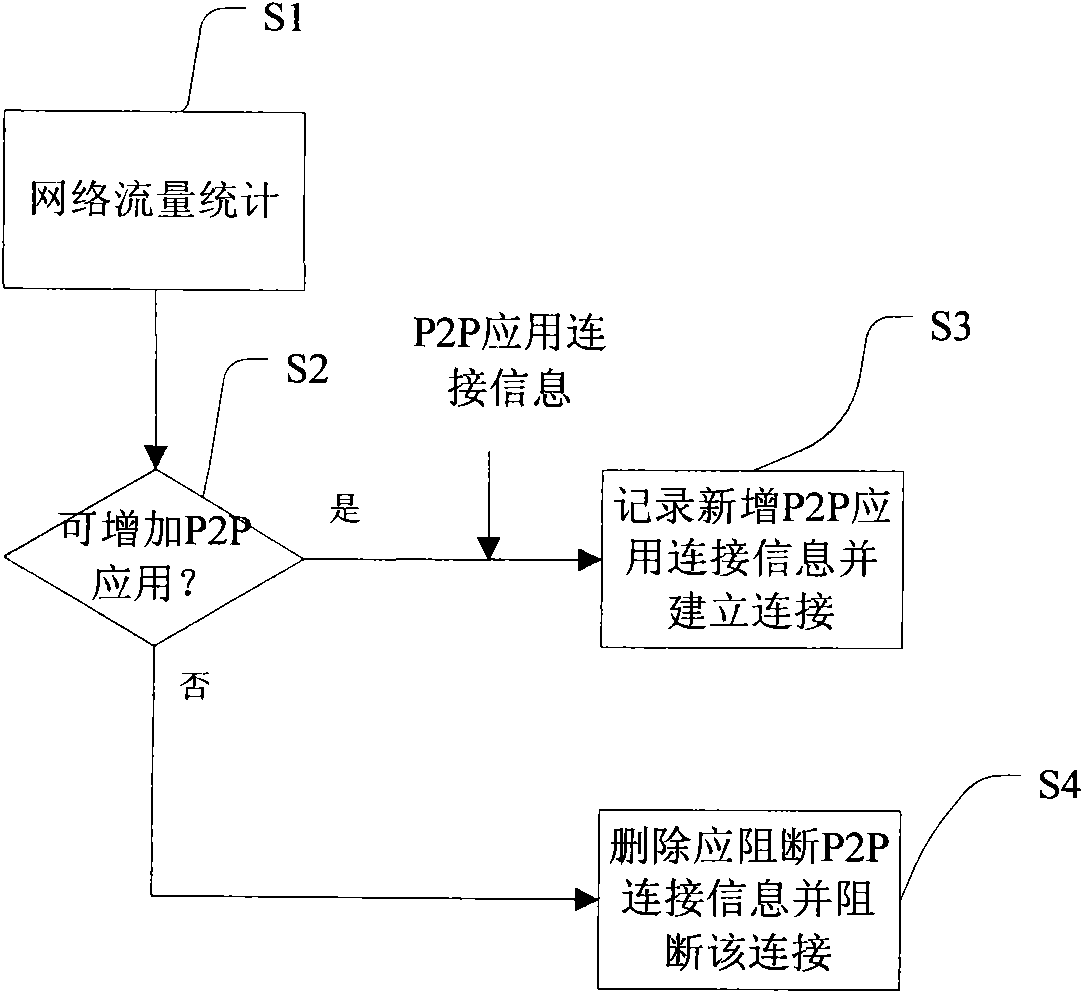
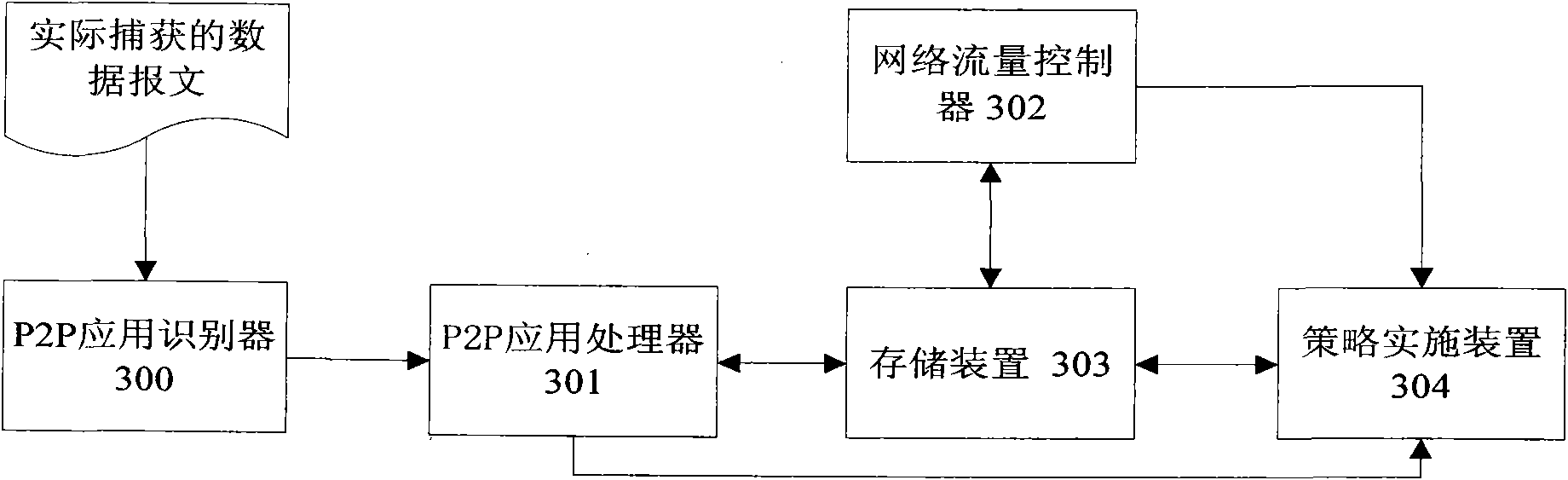
[0029] Hereinafter, traffic control and P2P service identification and processing are two independent processes triggered by different events. The flow control process invokes the results in the P2P service identification and processing process when needed.
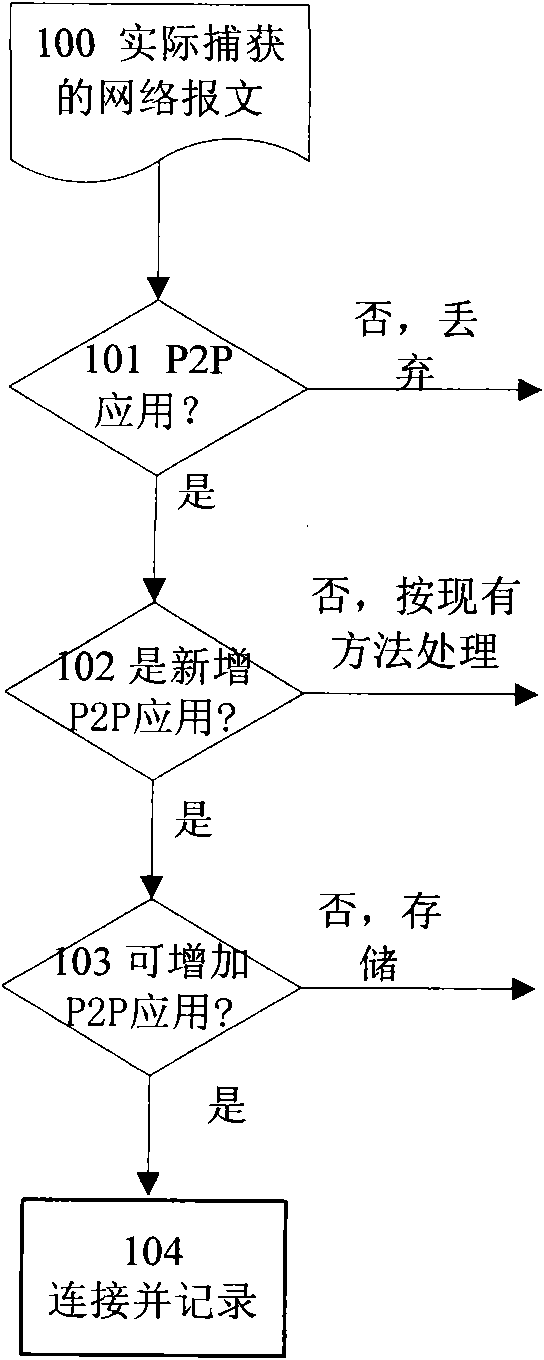
[0030] This embodiment takes the actually captured network message as a sample, analyzes the data message according to the protocol format used in various P2P application processes, and relies on the message characteristics or behaviors in the data message transmitted during the communication process of the P2P application. Identify P2P applications.
[0031] Such as figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com