Multi-identity network social intercourse system and implementation method
A technology for social networking and implementation methods, applied in transmission systems, digital transmission systems, data exchange networks, etc., to achieve the effects of protecting privacy, simple structure, and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] Embodiment 1: (the present invention is described in further detail below according to accompanying drawing:
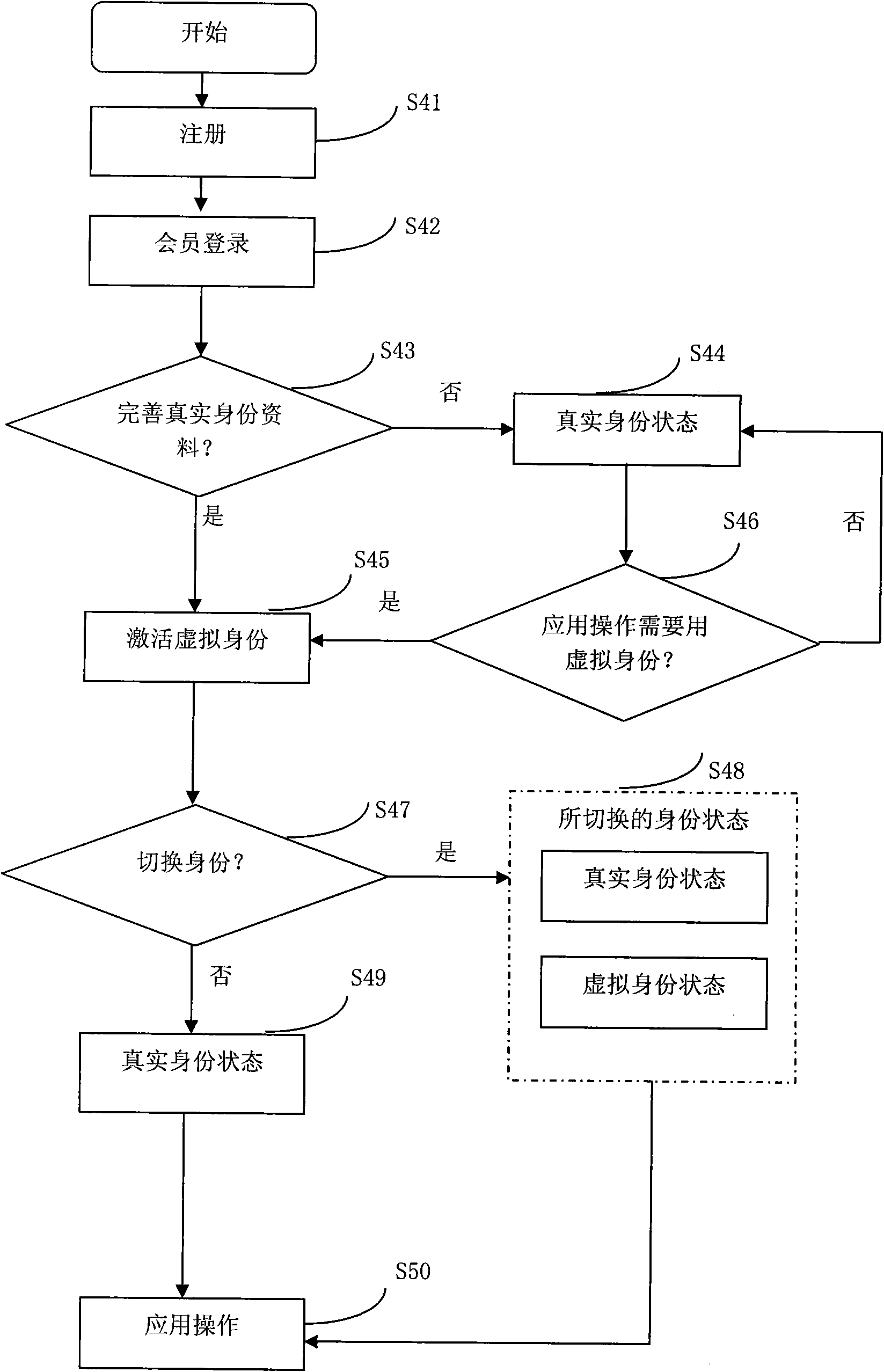
[0041] like figure 2 Shown is a flow chart of a method for implementing a dual-identity example of a multi-identity network social networking system in the present invention. It specifically includes the following steps:
[0042] Step S41: register as a member, the user registers as a member of the social network system according to the registration information.
[0043] Step S42: log in with the registered user name in step S41, and complete the personal information and avatar of the real identity
[0044] Step S43: If the data is complete, execute step S45; if the data is not complete, execute step S44.
[0045] Step S44: Log in as a real identity status, the content viewed and operated by the member is the content and operation under the real identity, go to step S46.
[0046] Step S45: Activating the virtual identity, including filling in the name and ...
Embodiment 2
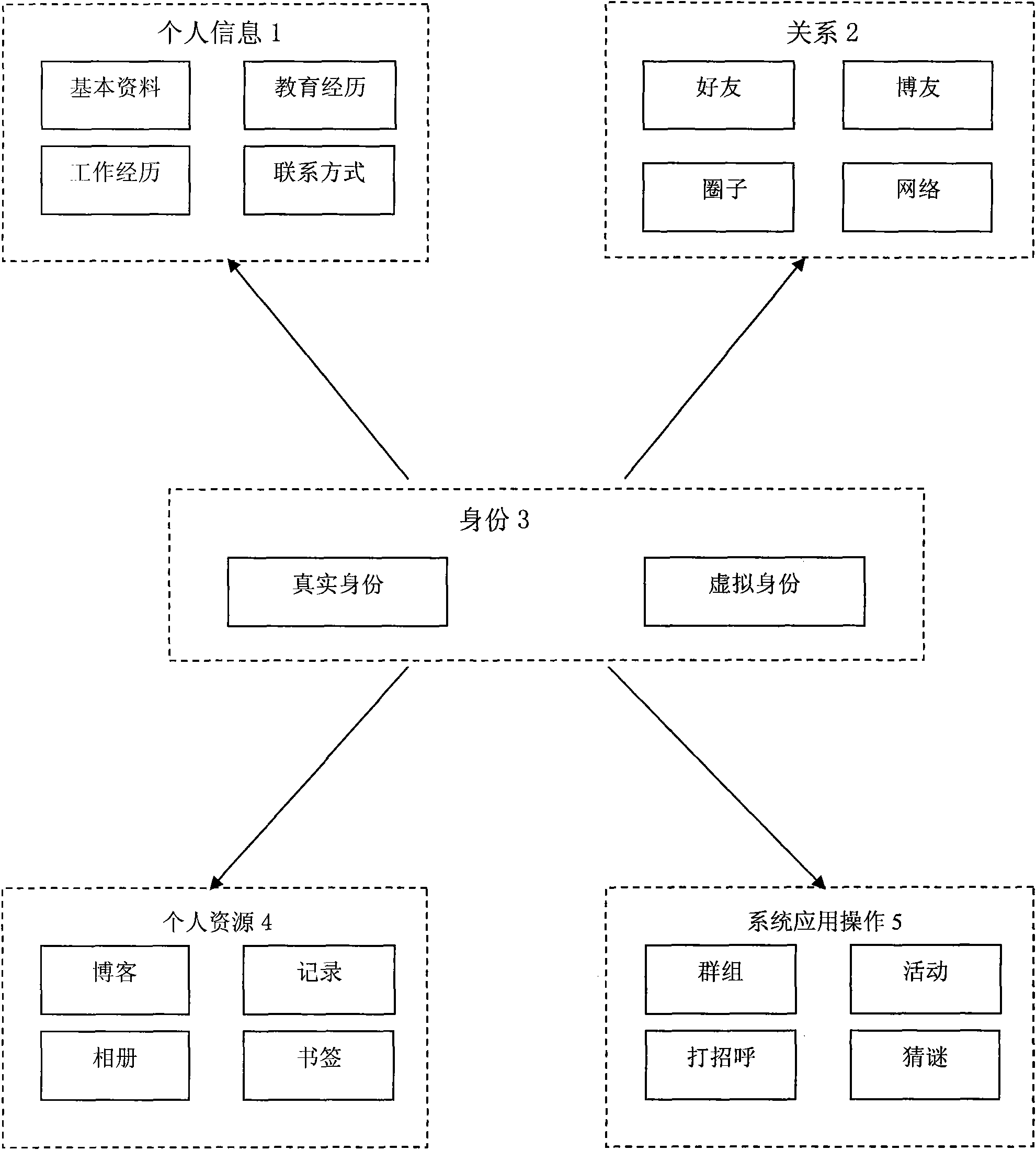
[0057] according to figure 1 It can be seen that figure 1 A schematic diagram of the dual-identity network social network system structure of a multi-identity network social system is given. The system is composed of personal information 1, relationship 2, identity 3, resource 4, and application 5. It is characterized in that: identity 3 and personal information 1 is connected. Different identities correspond to different personal information. After obtaining the identity, the personal information can be modified and controlled. Personal information can supplement the identity. Identity 3 is connected with relationship 2. Different identities have independent relationships. To protect user privacy, protect the independence of identities and prevent identities from being exposed at the moment of relationship interaction, identity 3 is connected to resource 4, and the emphases of identities are different, fully showing different identities The key points are different, the iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com