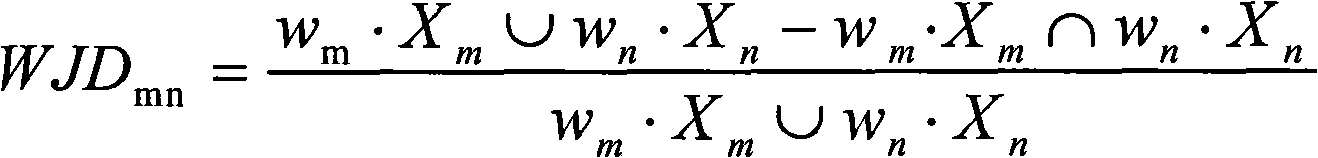Classification system and classification method of computer rogue programs based on file instruction sequence
A technology of instruction sequences and malicious programs, applied in computer security devices, calculations, special data processing applications, etc., can solve problems such as no unified standard for naming rules and unsatisfactory classification effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
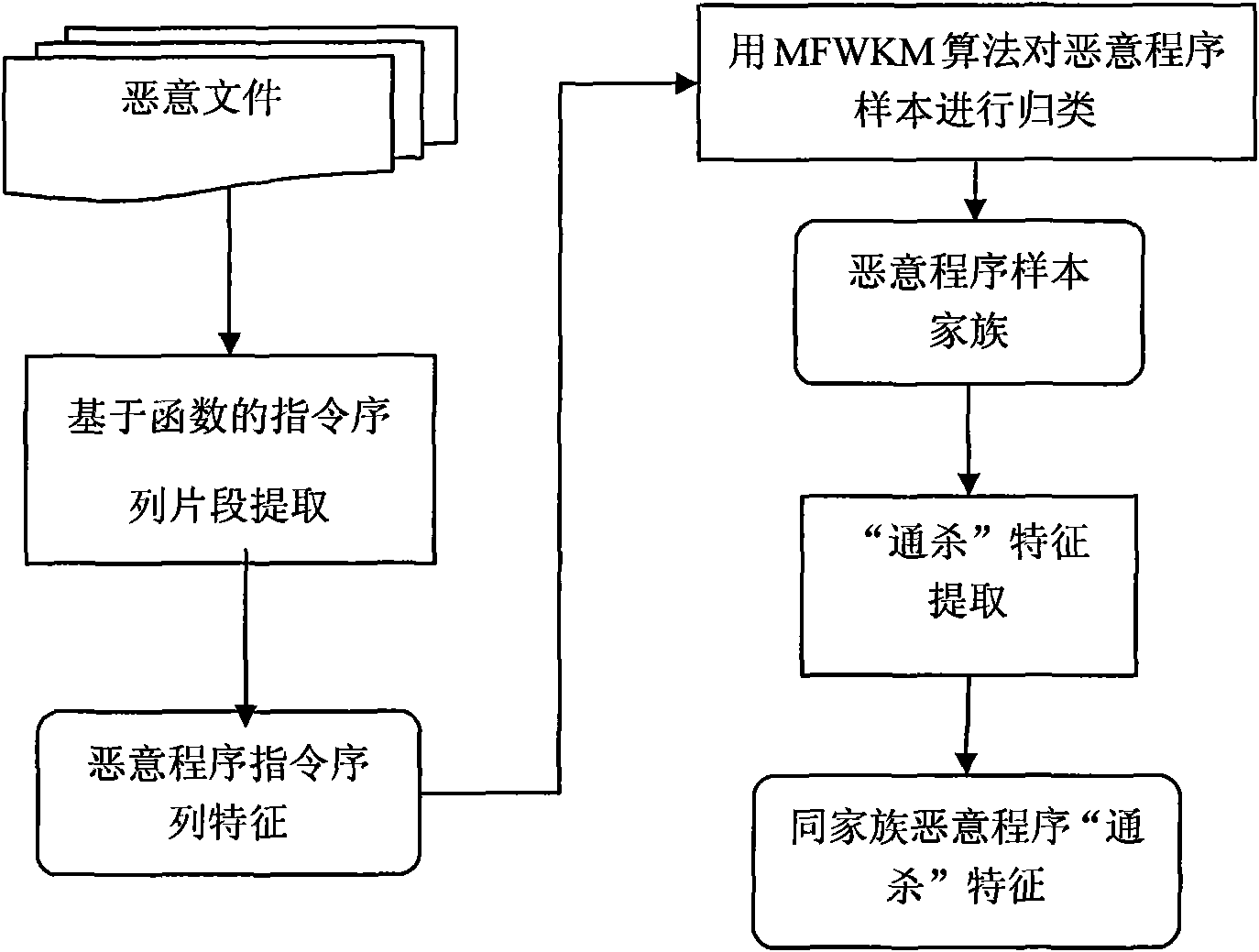
[0042] The computer malicious program classification system based on file instruction sequence of the present invention comprises:
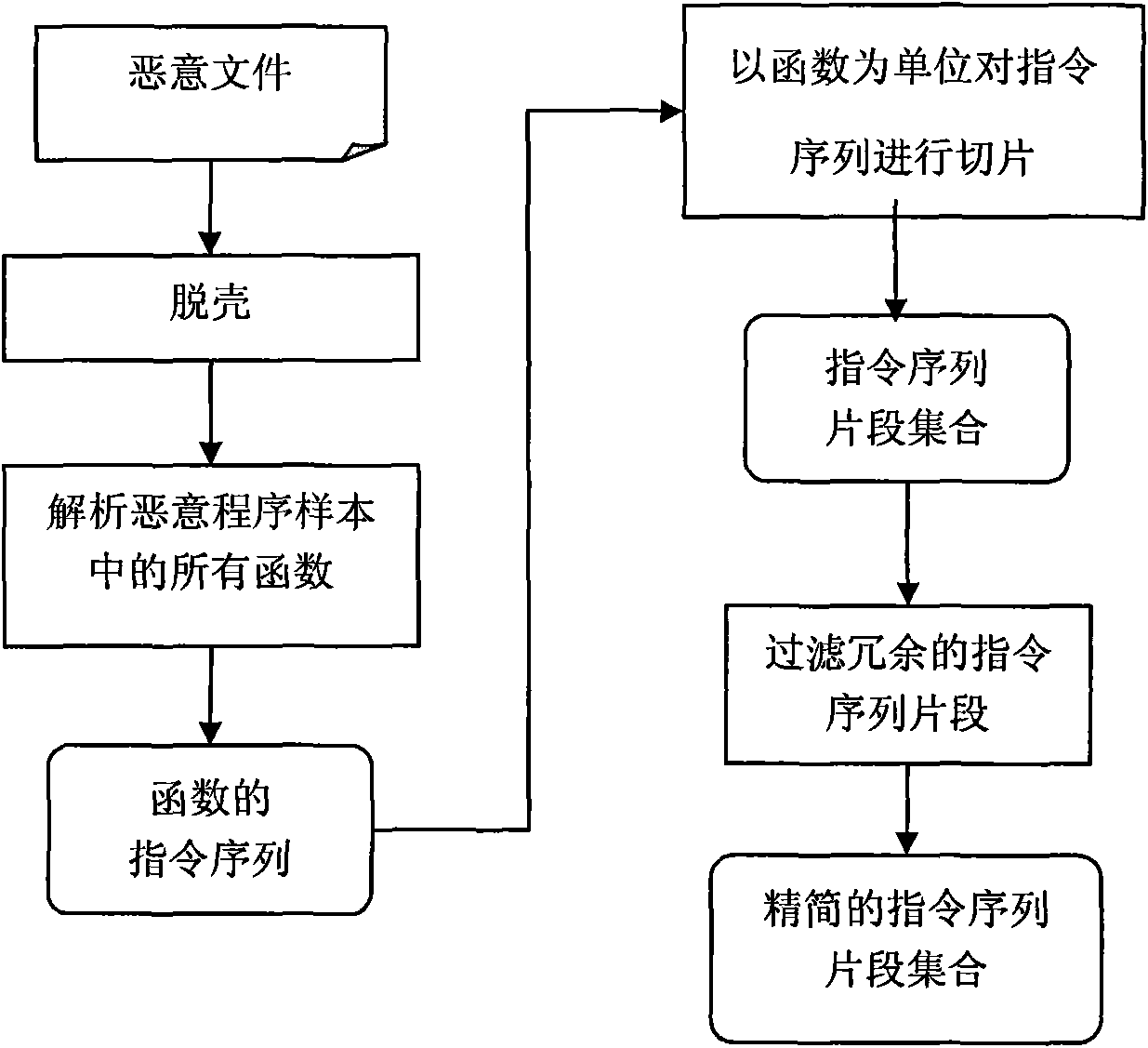
[0043] Instruction sequence feature extraction module, which first unpacks the sample file, extracts all the functions contained in the sample file, and removes the operands in the function, only retains the assembly instruction, and then uses the function as a unit to extract the instruction sequence of each function Slicing with the specified slice length at the specified step length, counting the instruction fragments appearing in each sample file, and generating a set of instruction fragments as the feature representation of the sample file;
[0044] A sample file difference degree calculation module, which calculates the difference degree between two malicious program sample files, and its calculation formula is:
[0045] WJD mn = w m ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com