Method for hierarchichal onion rings routing
A routing and onion technology, applied in the field of network security, can solve the problem of large computing load of the gateway
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
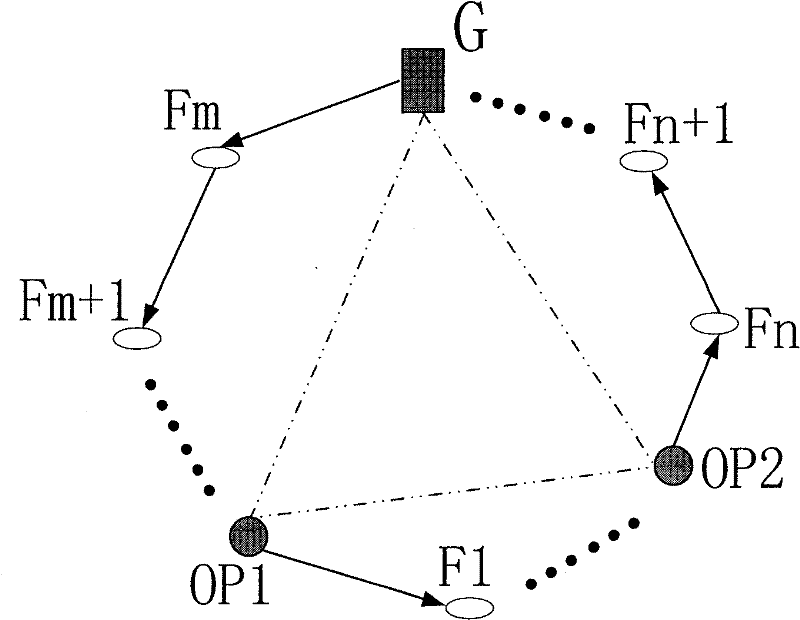
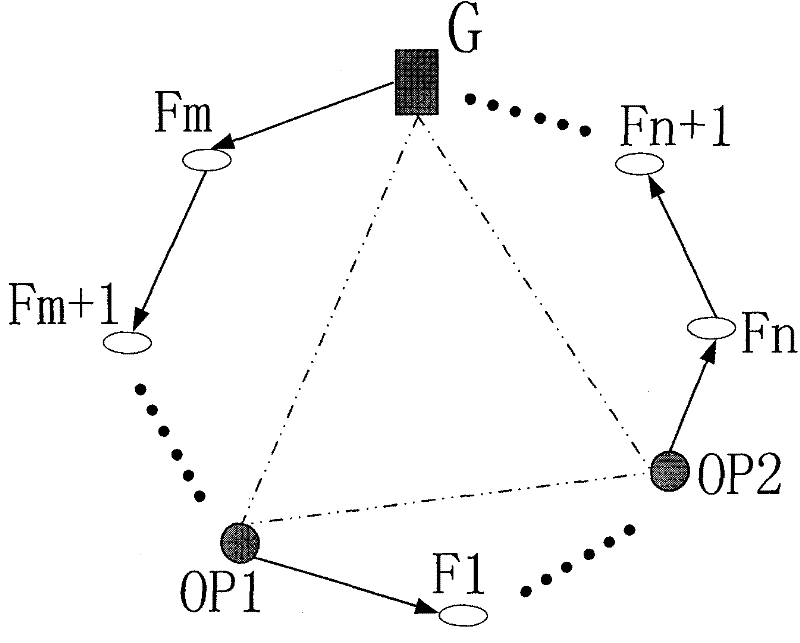
[0083] Layered onion rings of the present invention such as Figure 1Show. When the network is built, the gateway G records the trusted nodes in the network (OP nodes in the network). like Figure 1 imaginary As shown by the line, the gateway G and OP form a circular path.
[0084] like Figure 1 As shown, the OP1 node is the initial node, which chooses the anonymous set {OP1, OP2, G}, which is called the first layer of routing. When the onion packet starts to transmit, since the next node pointed out in the packet is the OP2 node, and the OP2 node and the OP1 node are not adjacent nodes, the OP1 node establishes a new connection, assuming {OP1, F 1 ,..., OP2}, this route is called the second layer route, which is equivalent to the next layer route. When the onion packet is transmitted to the OP2 node, the second-layer routing terminates and returns to the upper-layer routing, that is, re-enters the first-layer routing.
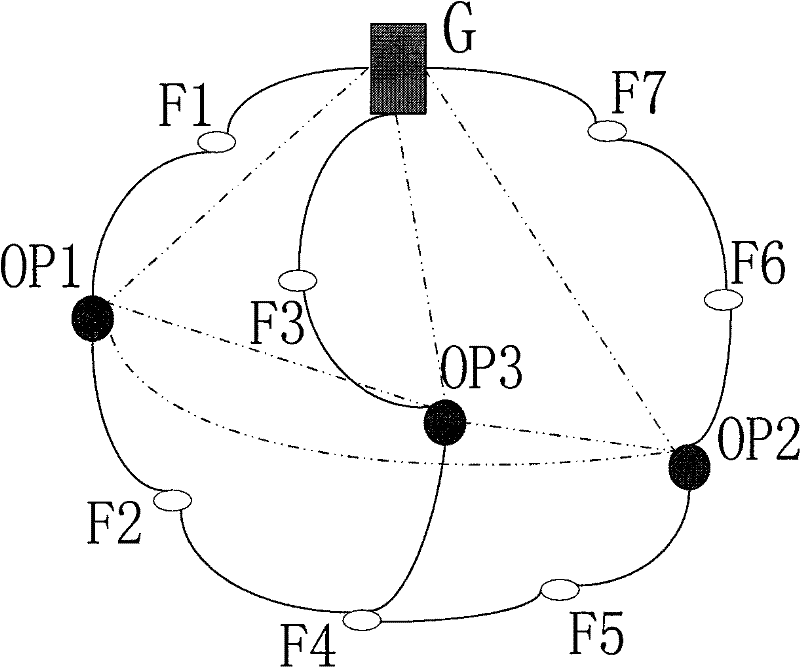
[0085] Attached below Figure 2 The preferred em...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com