Key distribution method and device, mobile terminal, communication equipment and storage medium
A mobile terminal and terminal equipment technology, applied in the field of communication, can solve problems such as low communication security and inability to obtain authentication keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
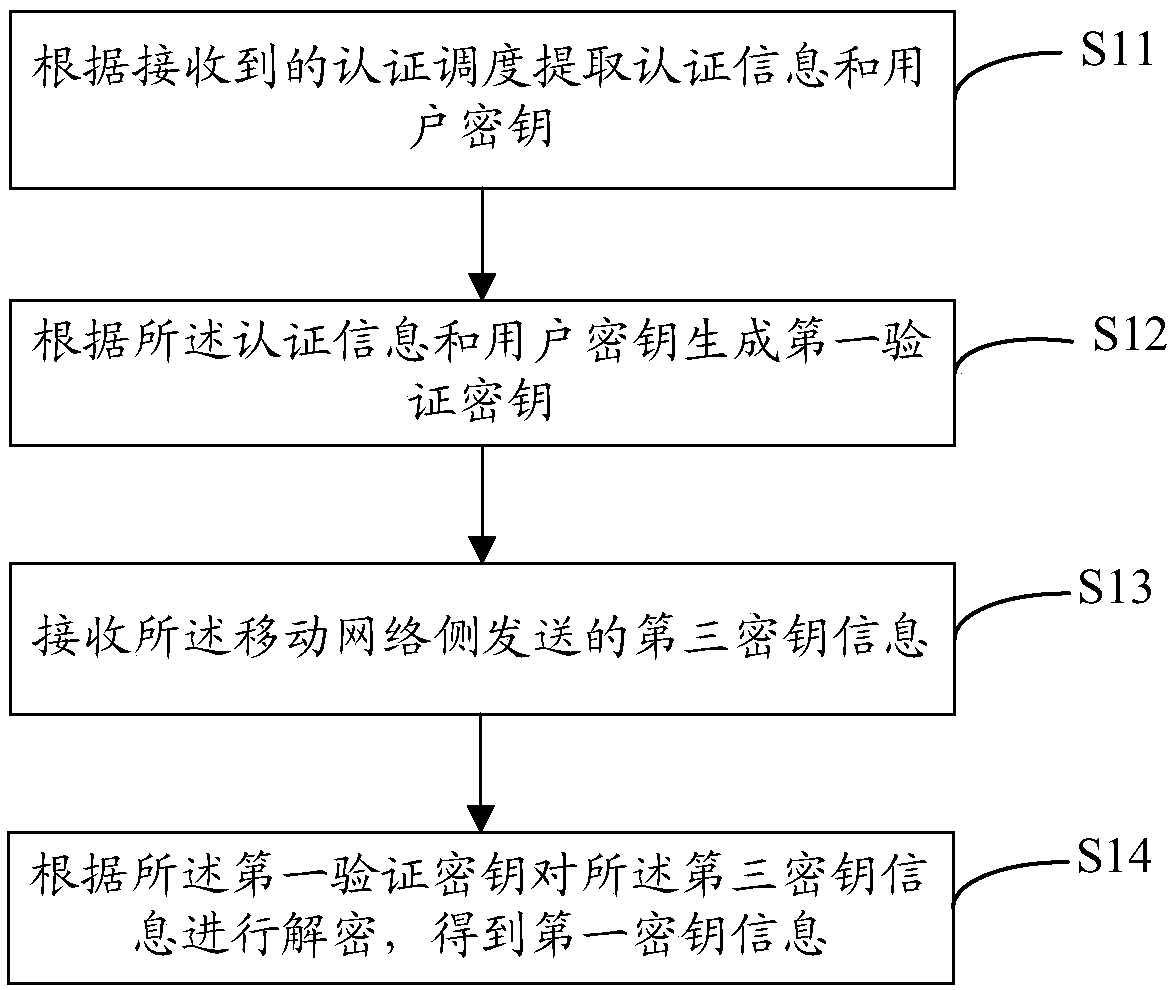
[0077] See figure 1 , the key distribution method provided by this embodiment, this method is mainly applied on the mobile terminal, and the specific implementation steps are as follows:
[0078] S11. Extract authentication information and a user key according to the received authentication schedule.
[0079] In practical applications, the authentication information includes at least one of a random character string RAND, an authentication parameter AUTN, a challenge response RES, and a session key, and may even be a secret key directly generated by the mobile terminal. The user key is simultaneously stored in the mobile terminal, the base station and the mobile network.
[0080] S12. Generate a first verification key according to the authentication information and the user key.
[0081] In this step, a certain algorithm needs to be combined to obtain the calculation. The preferred algorithm can be some key calculation algorithm, or some encryption algorithm. Specifically, t...
Embodiment 2
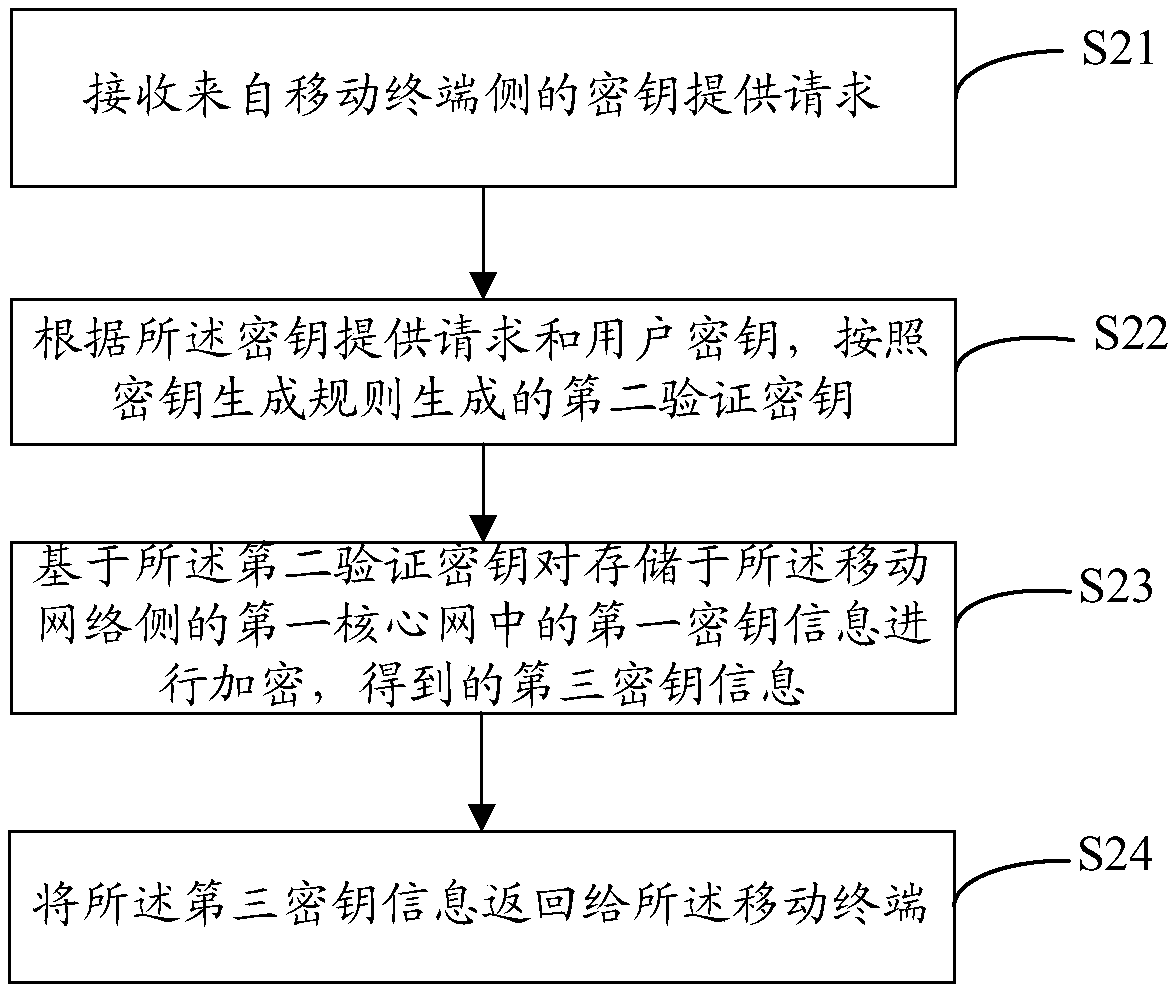
[0153] See figure 2 , the method for issuing keys provided in this embodiment, the method is mainly applied on one end of the mobile network, the mobile network side includes the first core network and the second core network, and the specific implementation steps are as follows:
[0154] S21. Receive a key provision request from the mobile terminal side.
[0155] S22. Generate a second verification key according to the key generation rule according to the key provision request and the user key.
[0156] S23. Encrypt the first key information stored in the first core network on the mobile network side based on the second verification key to obtain third key information.
[0157] S24. Return the third key information to the mobile terminal.
[0158] In this embodiment, the authentication information for generating the second verification key can be obtained in two ways, one is generated by the mobile terminal, and then sent to the device on the mobile network side; the other...
Embodiment 3
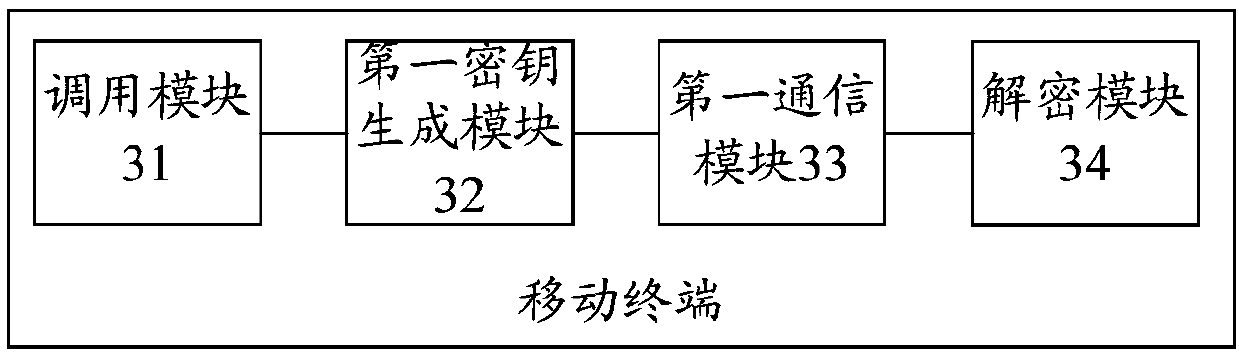
[0204] This embodiment provides a mobile terminal, see image 3 As shown, the mobile terminal includes a call module 31, a first key generation module 32, a first communication module 33 and a decryption module 34, wherein
[0205] Call module 31, for extracting authentication information and user key according to the received authentication schedule;
[0206] The first key generation layer module 32 is configured to generate a first verification key according to the key generation rules according to the authentication information and the user key;
[0207] The first communication module 33 is configured to return an authentication response message to the mobile network side; and receive third key information sent by the mobile network side, where the third key information is provided by the mobile network side according to the Key information obtained after the authentication response message and the second verification key generated by the key generation rule encrypt the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com