Secure communication method based on switch
A secure communication and switch technology, applied to secure communication devices and key distribution, can solve the problem of illegal interceptors being unable to steal and intercept data, and achieve the effects of increasing the risk of confidentiality, ensuring real-time updates, and strong confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
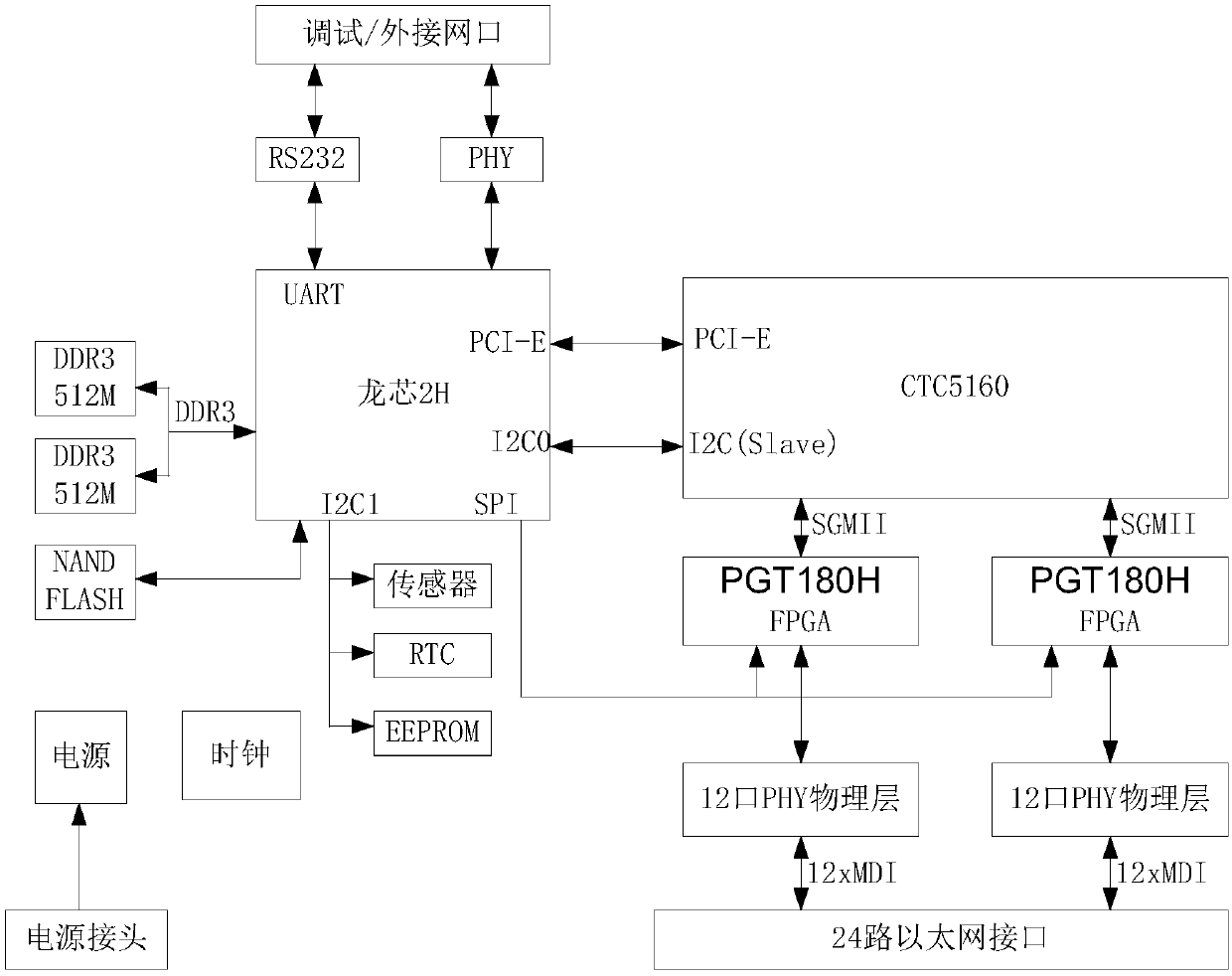
[0034] like figure 1 Shown is the hardware structural diagram of the present invention.
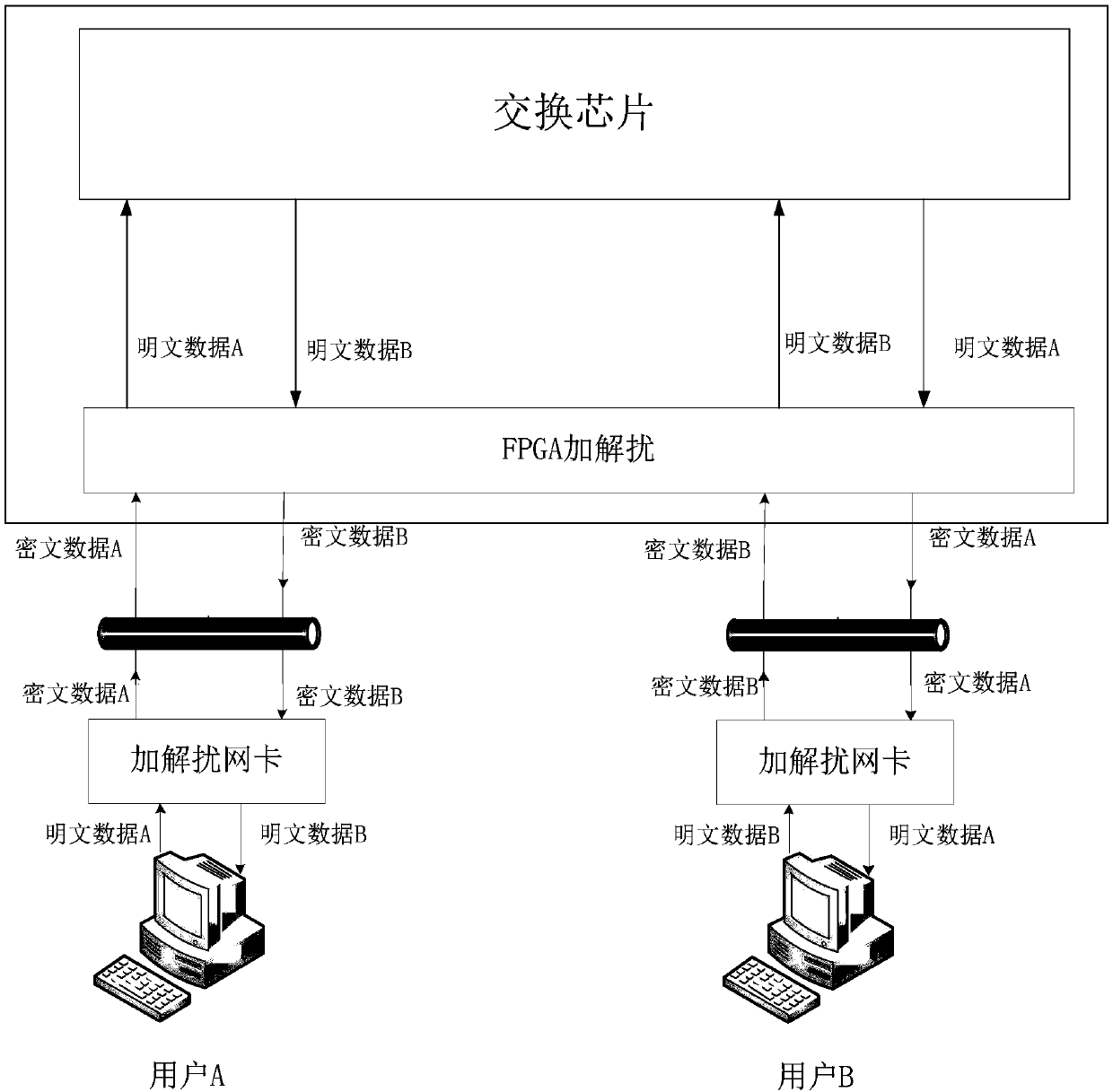
[0035] The security switch system based on the encryption algorithm includes the connection between the CPU and the switching chip; the switching chip and the FPGA are connected through the Serdes interface; after the FPGA performs encryption and decryption work, the encrypted message is sent to the network card of the user-side computer through the PHY chip. After the network card is decrypted, it forms a normal message and uploads it to the computer. like Image 6 shown.
[0036] FPGA implementation is mainly composed of RGMII interface MAC, SGMII interface MAC, scrambling unit, descrambling unit and MDIO control unit, such as Figure 5 shown.
[0037] After the ciphertext data is processed by the PHY module, it is transmitted to the FPGA in RGMII ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com