Method, node and system of network access
A network access and node technology, applied in the field of communications, can solve the problems of complex authentication process and inability to provide operator control information, and achieve the effect of simple authentication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
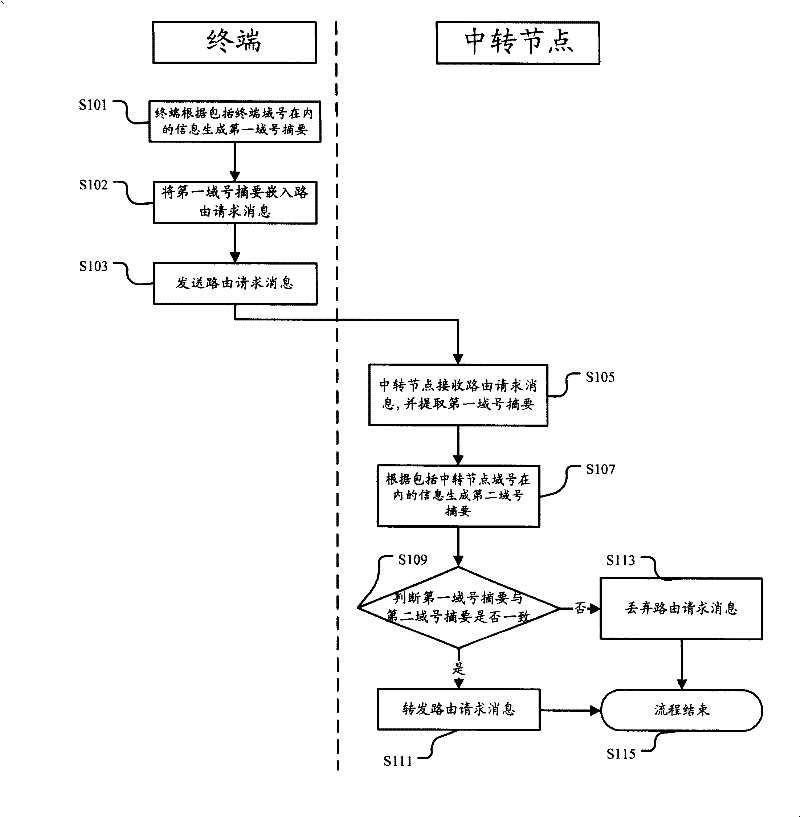
[0038] figure 2 It is a flow chart of Embodiment 1 of the network access method of the present invention. Such as figure 2 As shown, this embodiment includes:
[0039] Step S101: the terminal generates a first domain number summary according to the information including the terminal domain number;
[0040] Step S102: Embedding the first domain number abstract into the routing request message;
[0041] Step S103: sending a routing request message;
[0042] Step S105: the transit node receives the routing request message, and extracts the first domain number abstract;
[0043] Step S107: Generate a second domain number summary according to the information including the domain number of the transit node;
[0044] Step S109: Determine whether the first domain number digest is consistent with the second domain number digest, if they are consistent, execute step S111, otherwise, execute step S113;
[0045] Step S111: forward the routing request message, and execute step S115; ...
Embodiment 2
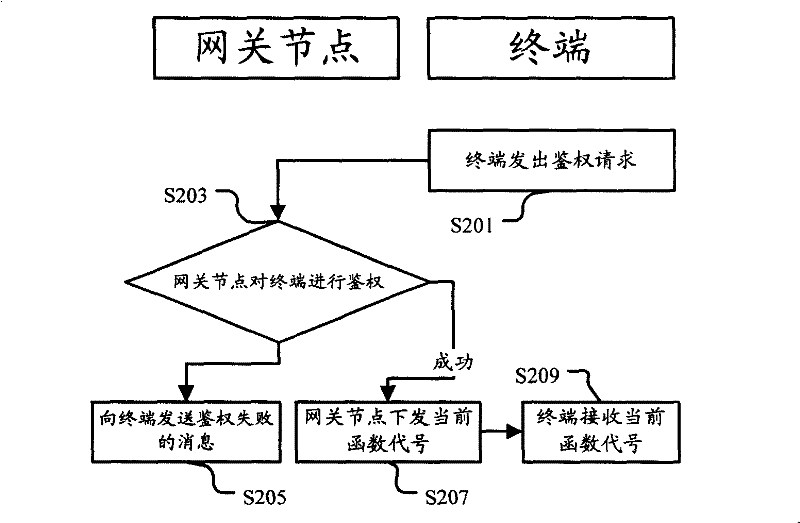
[0052] Figure 4 It is a flow chart of Embodiment 2 of the network access method of the present invention. This implementation is similar to Embodiment 1, but further includes: setting a function pool including multiple hash functions in advance on the terminal. Such as Figure 4 As shown, this embodiment also includes:
[0053] Step S201: the terminal sends an authentication request;
[0054] Step S203: the gateway node authenticates the terminal, if the authentication is successful, go to step S207, otherwise, go to step S205;
[0055] Step S205: Send a message of authentication failure to the terminal, and the process ends;
[0056] Step S207: the gateway node issues the current function code;
[0057] Step S209: the terminal receives the current function code.
[0058] After step S209, the terminal selects a hash function from the function pool according to the current function code, and executes the subsequent generation of the first information digest from the sele...
Embodiment 3
[0063] In this embodiment, the transit node is a user authenticated by the gateway node, and the terminal may be a user of the Ad hoc network, and the terminal has obtained the domain number and the current function code. In addition, terminal and transit nodes are preset with function pools containing multiple hash (Hash) functions.
[0064] Figure 5 It is a flow chart of Embodiment 3 of the network access method of the present invention. Such as Figure 5 As shown, this embodiment includes:
[0065] Step S301: the terminal selects a function from the Hash function pool according to the current function code in itself, and generates a first domain number summary according to the domain number and the identification information of the terminal;
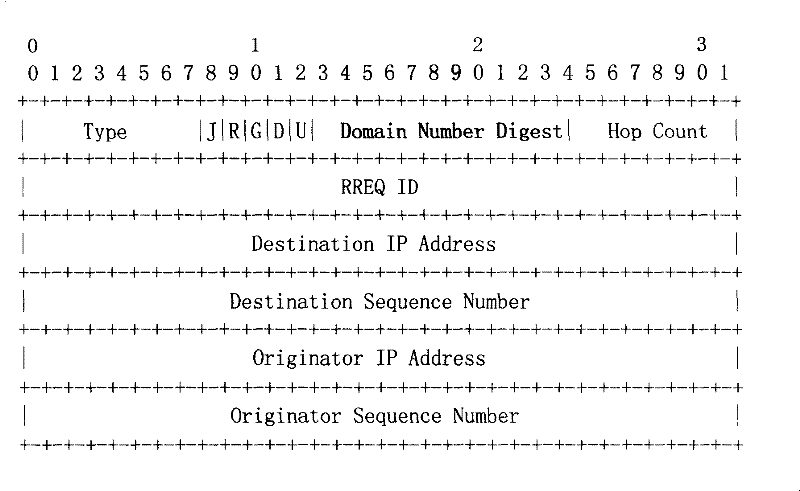
[0066] Step S303: Embedding the first domain number abstract into the reserved bit of the routing request message;
[0067] Step S305: sending a routing request message;
[0068] Step S307: the transit node receives the routing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com