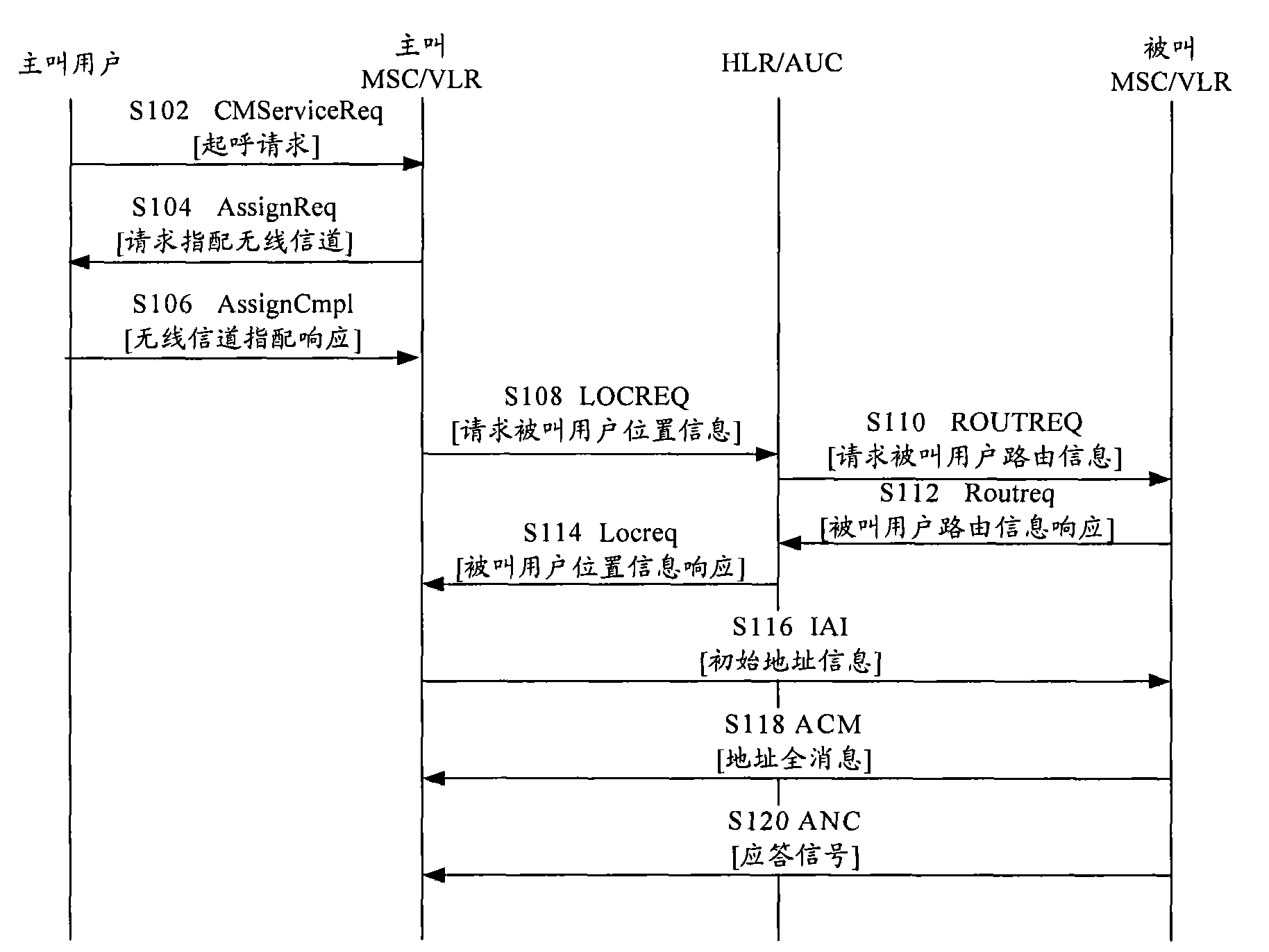
User authentication method and user authentication device
An authentication and user technology, applied in the field of communication, can solve the problems of illegal access to the network, inability to detect cloned terminals, etc., and achieve the effect of avoiding illegal theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
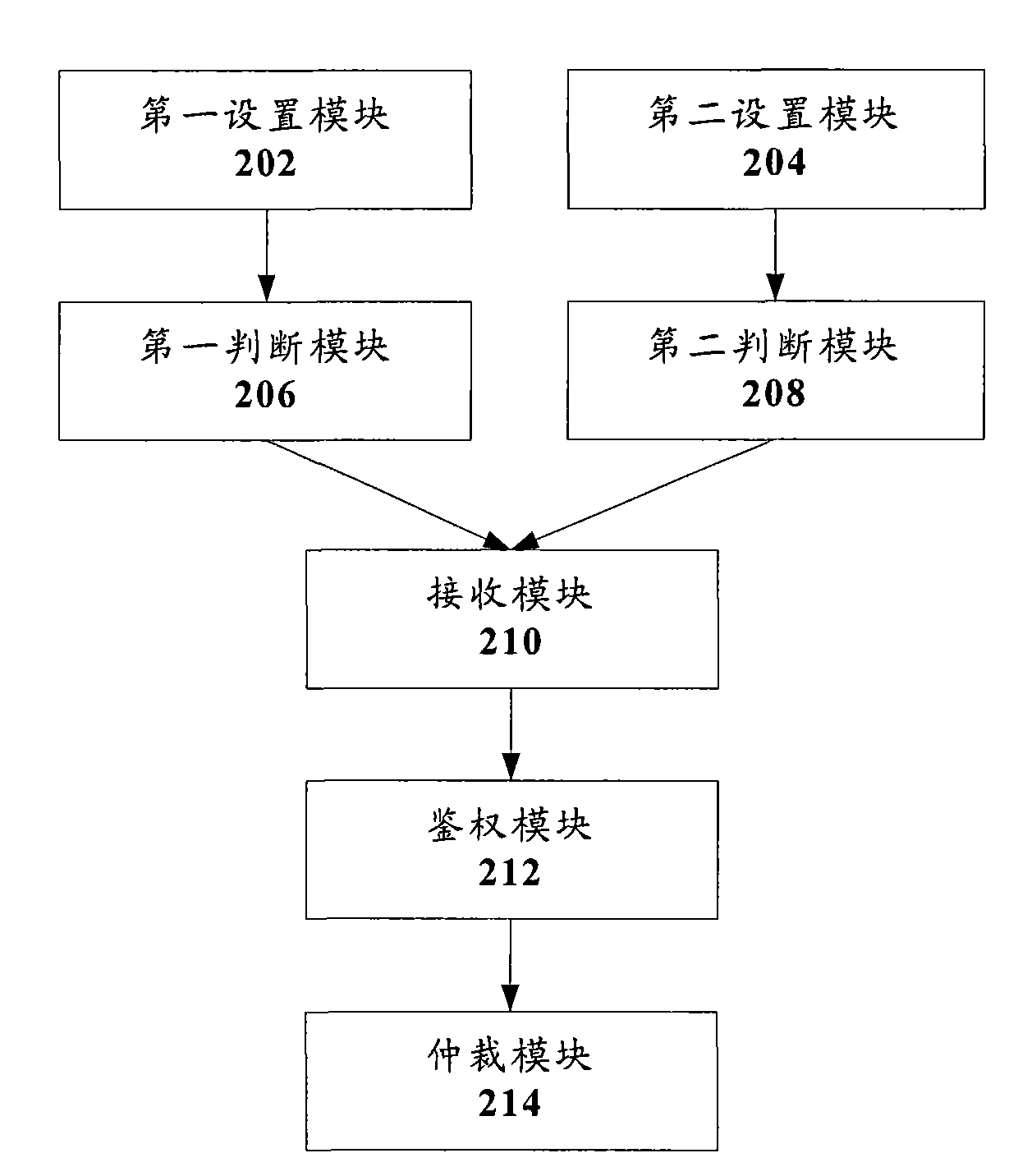
[0048] According to an embodiment of the present invention, a user authentication device is provided. figure 2 is a structural block diagram of a user authentication device according to an embodiment of the present invention, such as figure 2 As shown, the device includes: a first setting module 202, a second setting module 204, a first judging module 206, a second judging module 208, a receiving module 210, an authentication module 212, and an arbitration module 214. The above-mentioned structure is carried out below A detailed description.
[0049] The first setting module 202 is used for setting the SSD automatic update period of the calling user in advance.
[0050] The second setting module 204 is configured to set the calling user to cancel the SSD sharing after the last update time of the calling user's SSD exceeds the update period.
[0051] The first judging module 206 is connected to the first setting module 202, and is used for judging whether the last update ti...
Embodiment 2
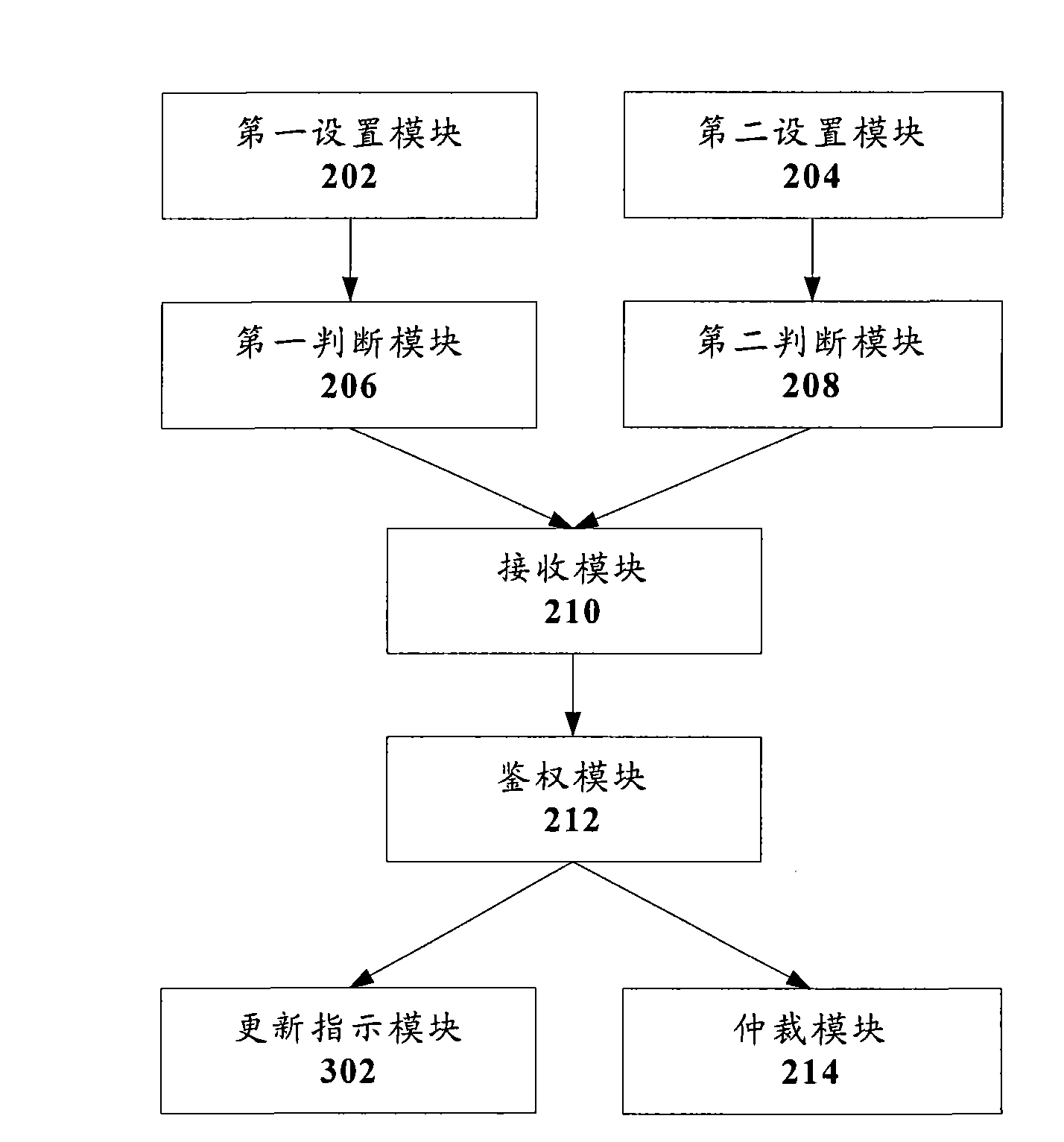
[0064] According to an embodiment of the present invention, an HLR / AUC is also provided. Figure 4 is a structural block diagram of HLR / AUC according to an embodiment of the present invention, such as Figure 4 As shown, the HLR / AUC includes: a first setting module 402, a second setting module 404, a first judging module 406, a second judging module 408, a receiving module 410, an authentication module 412, an update instruction module 414, and an arbitration module 416 , the above structure will be described in detail below.
[0065] The first setting module 402 is used to preset the SSD automatic update period of the calling user;
[0066] The second setting module 404 is used to set the calling user to cancel SSD sharing after the last update time of the SSD of the calling user exceeds the update cycle;
[0067] The first judging module 406 is connected to the first setting module 402, and is used to judge whether the last update time of the calling user's SSD exceeds the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com