Security incident correlation method and device as well as network server
A security event and correlation analysis technology, applied in the network field, can solve problems such as affecting the speed of matching, unable to achieve real-time matching, unable to identify false positives of normal behavior, etc., to achieve the effect of fast processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solutions of the embodiments of the present invention will be described in further detail below with reference to the drawings and embodiments.
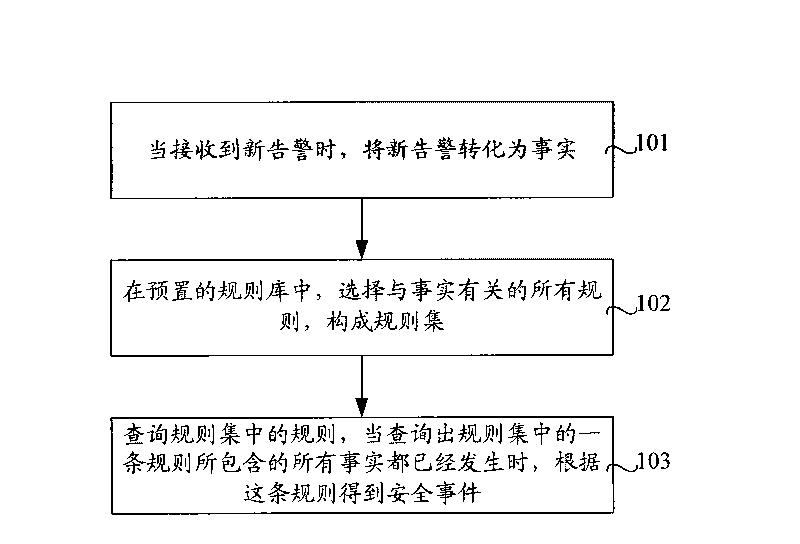
[0022] figure 1 It is a flowchart of a security event correlation method according to an embodiment of the present invention. Such as figure 1 As shown, this embodiment specifically includes the following steps:
[0023] Step 101, when a new warning is received, convert the new warning into a fact;
[0024] Step 102, in the preset rule base, select all the rules related to the facts to form a rule set;
[0025] Step 103, query the rules in the rule set, and when it is found that all the facts contained in a rule in the rule set have occurred, obtain the security event according to this rule.
[0026] Specifically, the rules in the query rule set can be queried in a set order.
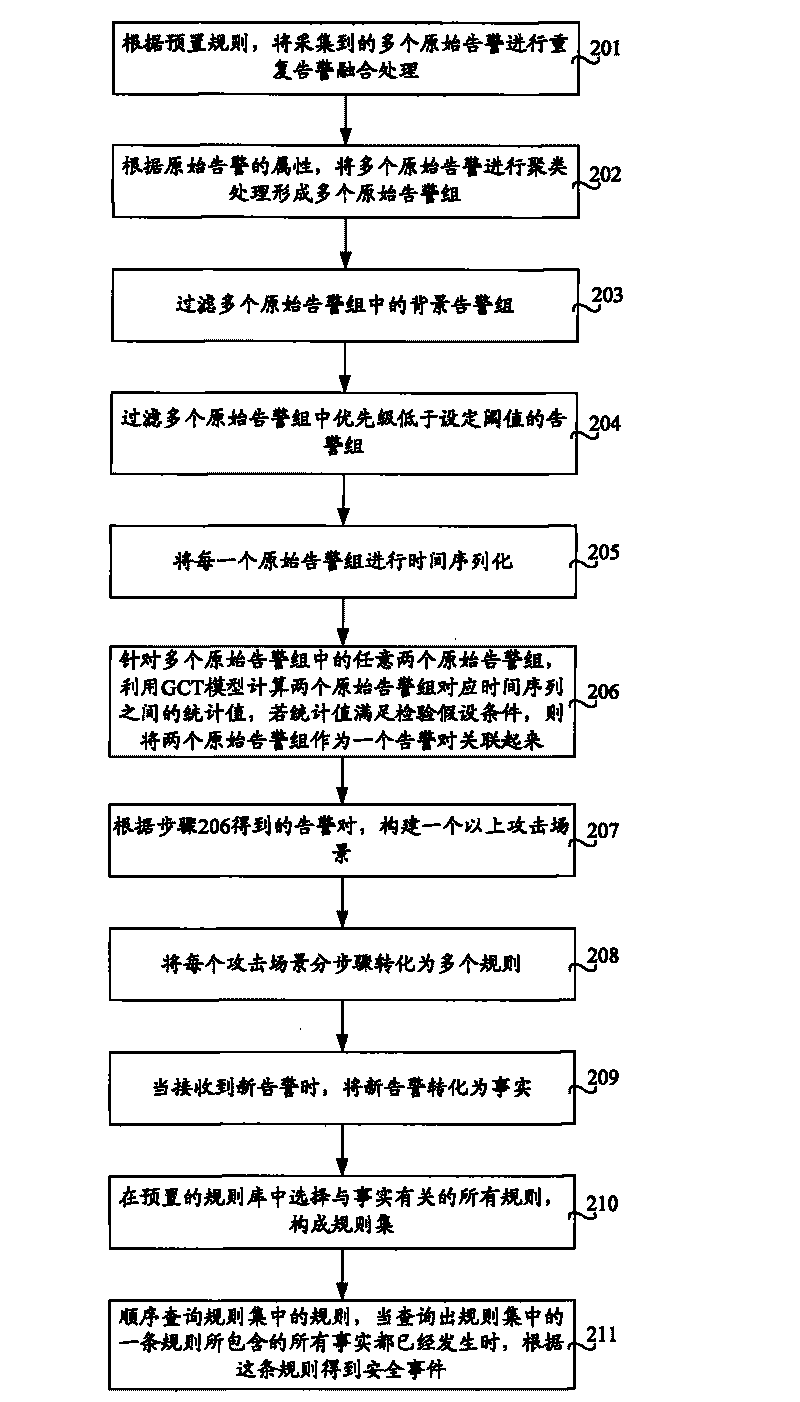
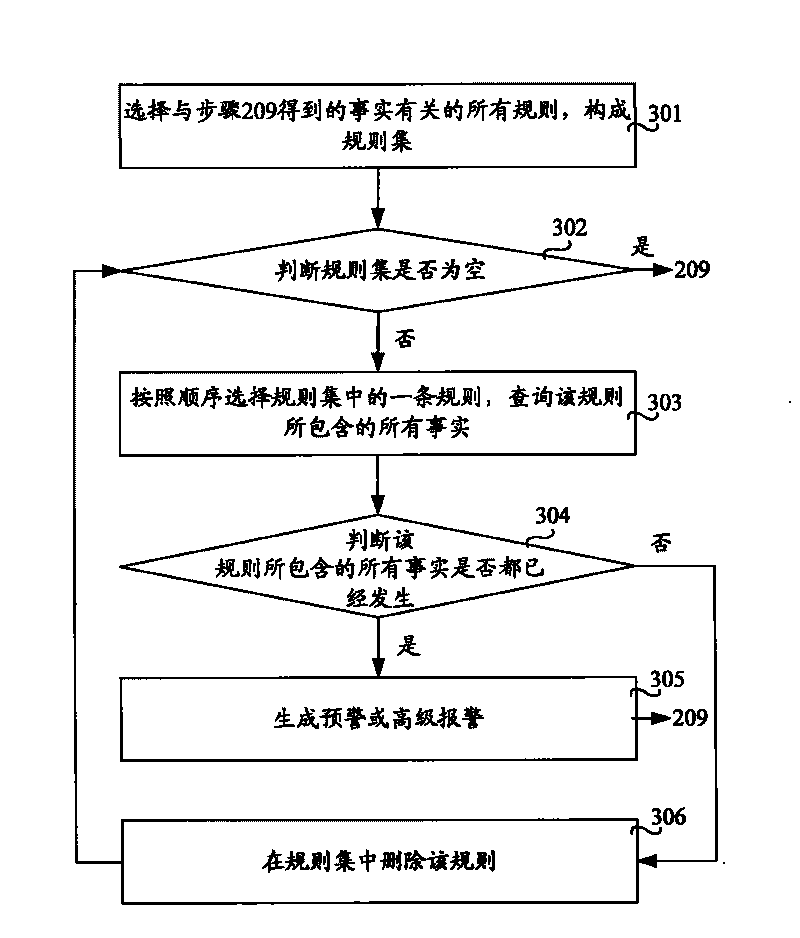
[0027] The above steps are performed in an online mode, wherein the preset rule base is configured in an offline or online mode, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com