Supervisory method and supervisory entity of authorization service of identify providing entity
An entity and identity technology, applied in electrical components, wireless communication, security devices, etc., can solve problems beyond service qualification and scope, and achieve the effect of meeting privacy requirements, ensuring security, and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
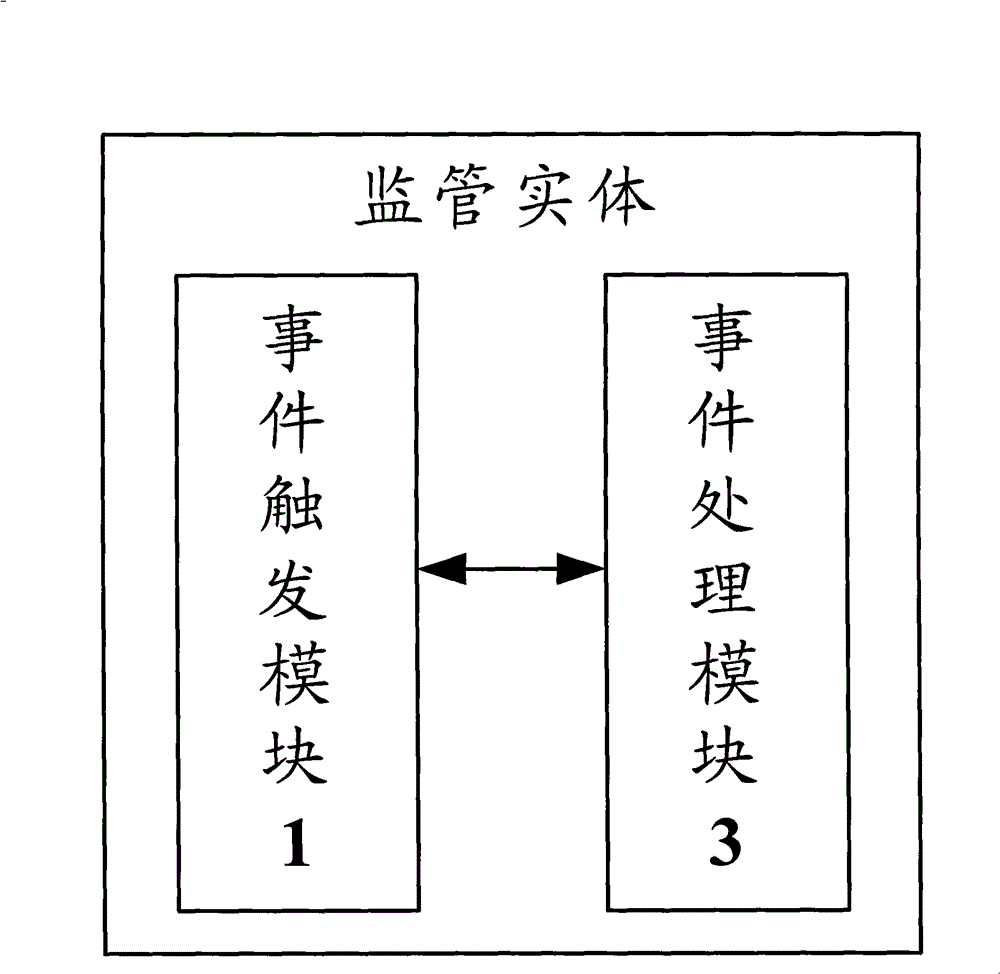
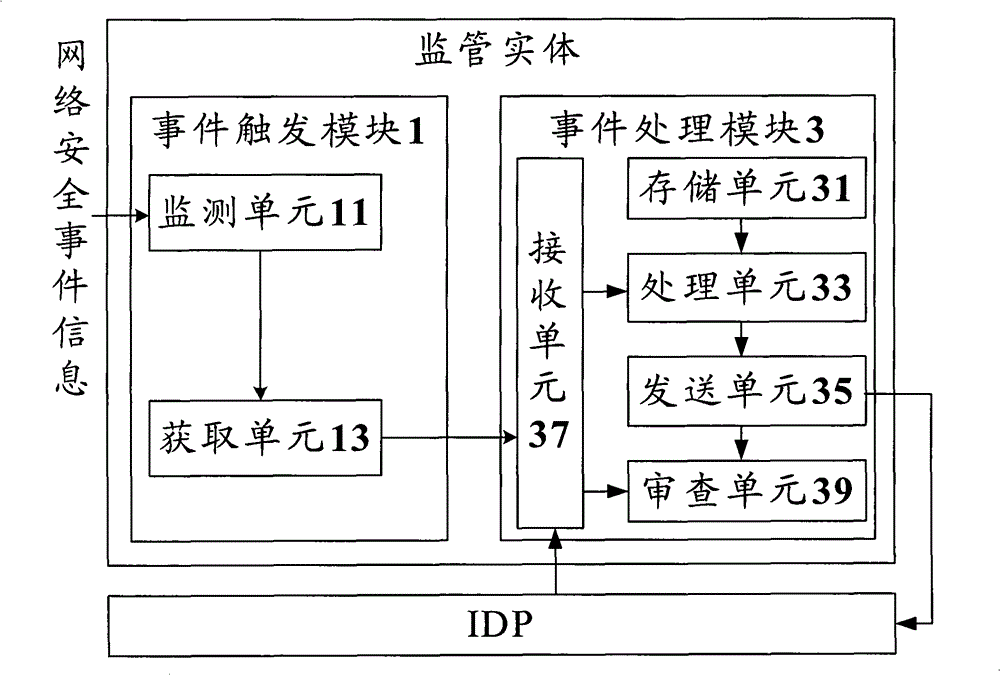
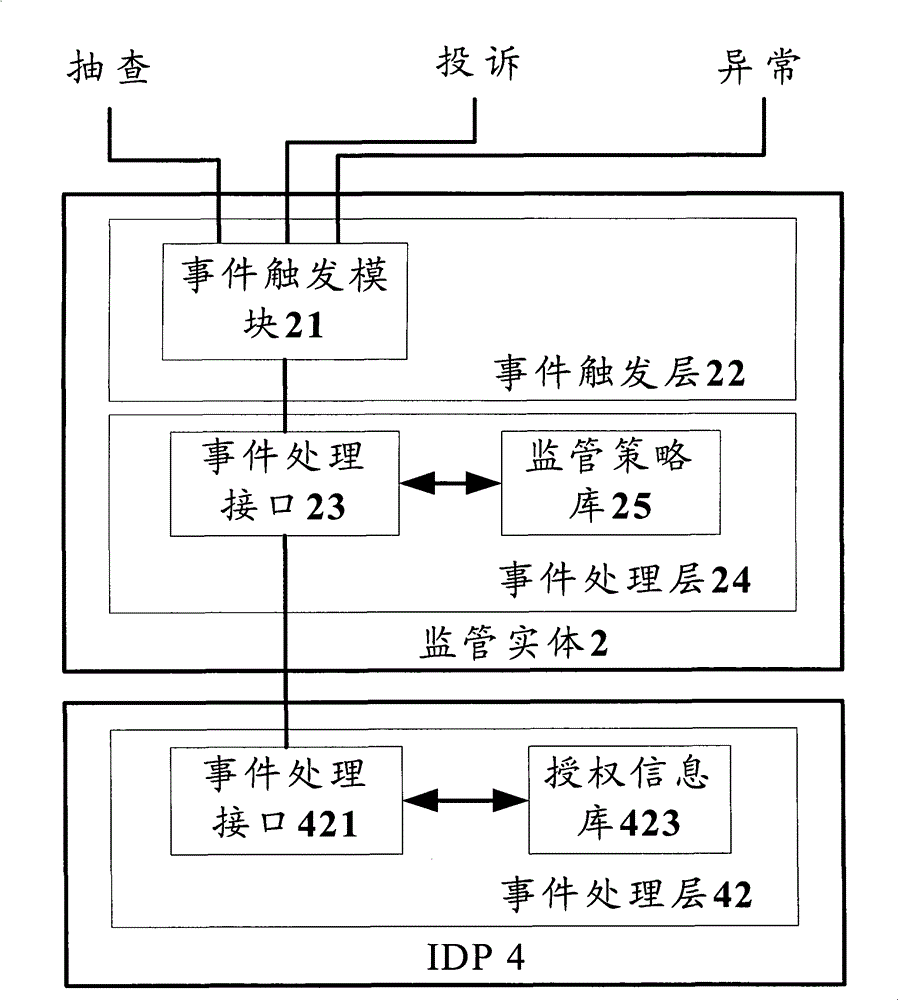
[0019] Functional Overview
[0020] Whether it is in policy design or in actual application, it is necessary to reflect the supervision of IDP authorization services. In order to meet the needs of users and network security, the embodiment of the present invention provides an online supervision measure to ensure the orderly operation of the network. In the embodiment of the present invention, after the network security event information is monitored or received, the information of the network security event is converted into supervision policy parameters according to the preset conversion policy, and then the supervision policy parameters are processed according to the supervision policy to generate Corresponding regulatory instructions are sent to the IDP, instructing the IDP to return the corresponding authorization information. After receiving the authorization information returned by the IDP, according to the authorization information and the monitoring strategy, it is judg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com