Method, network equipment, user equipment and communication system for ensuring forward security
A user equipment, forward security technology, applied in the field of communication, can solve problems such as forward insecurity, and achieve the effect of simplifying the process and solving the problem of forward insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
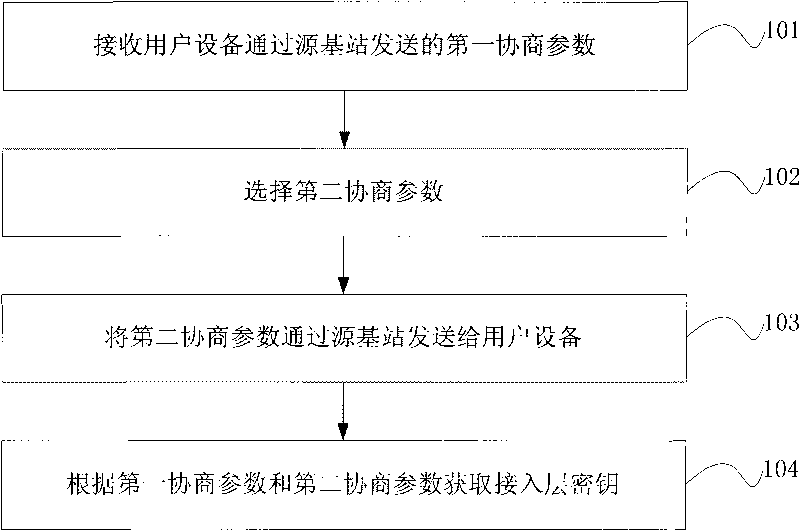
[0040] see figure 1 , the embodiment of the present invention provides a method for ensuring forward security, the method may include:
[0041] 101: Receive the first negotiation parameter sent by the user equipment through the source base station;
[0042] The execution subject of this step may be the target base station.
[0043] 102: Select a second negotiation parameter;
[0044] The execution subject of this step may be the target base station.
[0045] 103: Send the second negotiation parameter to the user equipment through the source base station; the second negotiation parameter can be used by the user equipment to derive the access layer key by using the first negotiation parameter and the second negotiation parameter after receiving the second negotiation parameter;
[0046] The execution subject of this step may be the target base station.
[0047] 104: Acquire an access layer key according to the first negotiation parameter and the second negotiation parameter,...
Embodiment 2
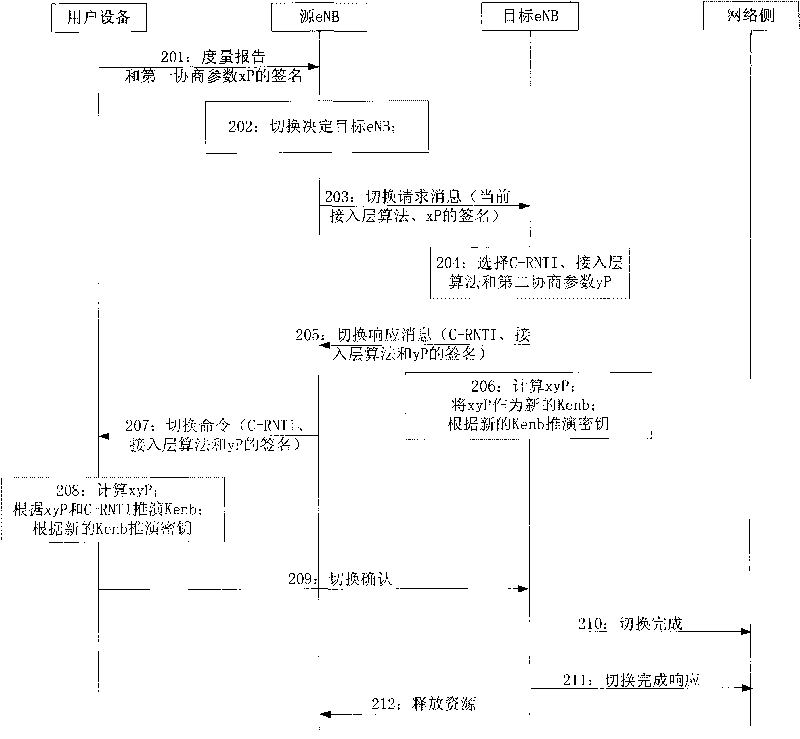
[0060] An embodiment of the present invention provides a method for ensuring forward security. The applicable scenario of the method may be: the user equipment UE and the eNB support ECC (Ellipse Curve Cryptosystems, elliptic curve cryptosystem), such as figure 2 As shown, the method may specifically include:
[0061] 201: After the UE receives the message that the eNB is to be switched, the UE sends a Measurement report (measurement report) and a signature of the first negotiation parameter xP to the source eNB.
[0062] 202: The source eNB receives the measurement report and xP signature sent by the UE, and determines the target eNB for handover according to the current state of the UE carried in the measurement report and the strength of the service signal of each eNB detected by the UE.
[0063] 203: The source eNB sends a handover request message to the target eNB;
[0064] The current RRC (Radio Resource Control, radio resource control) / UP (User Plane, user plane) algo...
Embodiment 3
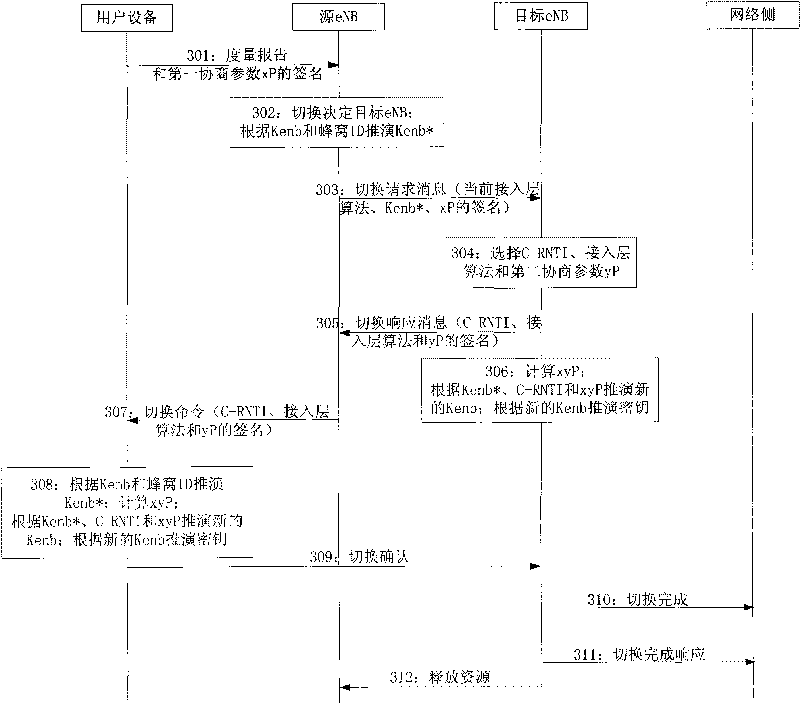
[0081] see image 3 , the embodiment of the present invention provides a method for ensuring forward security, the applicable scenario of the method may be: UE and eNB support ECC, the method may specifically include:
[0082] 301: After the UE receives the message that the eNB is to be switched, the UE sends a Measurement report and a signature of the first negotiation parameter xP to the source eNB.
[0083] 302: The source eNB receives the measurement report and the xP signature sent by the UE, and determines the target eNB for UE handover according to the current state of the UE carried in the measurement report and the strength of the service signal of each eNB detected by the UE;
[0084] And, the source eNB according to the key K currently used by the UE and the source eNB eNB and the Cell ID (cell ID) of the target cell, use KDF deduction to calculate K eNB * ;
[0085] 303: The source eNB sends a handover request message to the target eNB;
[0086] Carry K in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com