Method and system for identity authentication and key agreement
A technology for key negotiation and identity authentication, applied in the field of identity authentication and key negotiation methods and systems, can solve problems such as increased transmission delay, denial of service attacks, and increased message transmission processes, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] Functional Overview
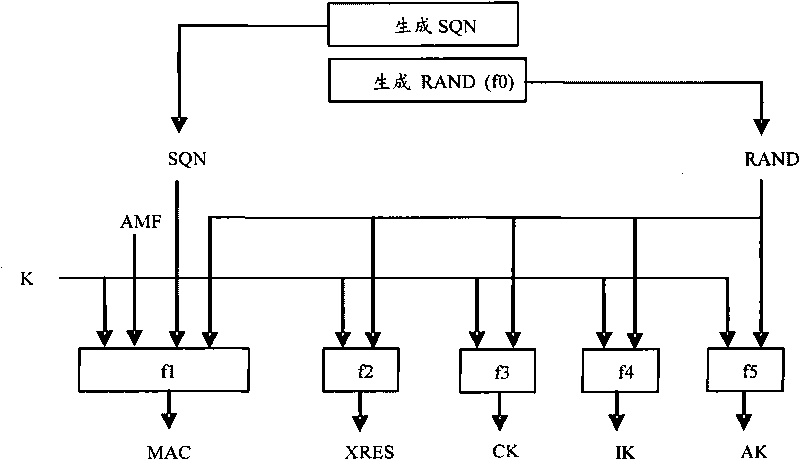
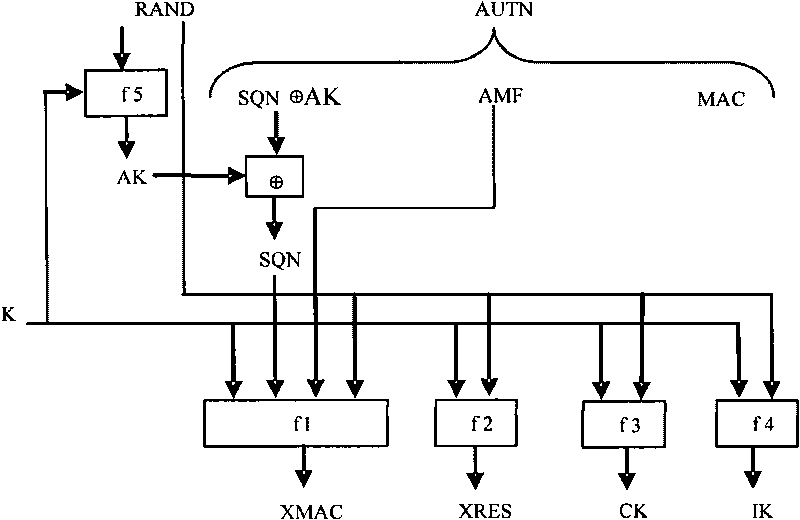
[0065] The present invention considers the problem of poor confidentiality of IMSI and key transmission in the related art. The present invention adopts the Public Key Broadcast Protocol (Public Key Broadcast Protocol-PKBP), and introduces a credible Certificate Authority (Certificate Authority, CA) into the network. Generate private keys and issue public keys to VLR and HLR, and use the self-verifying public key identity authentication scheme to effectively improve the confidentiality of IMSI and key transmission.
[0066] method embodiment
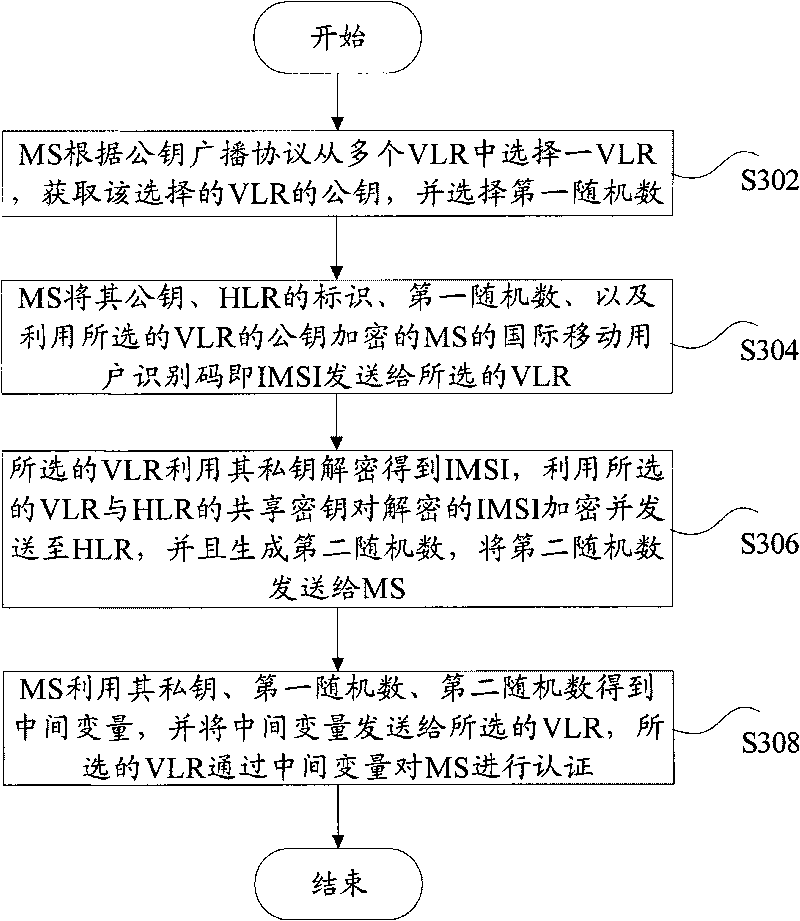
[0067] In this embodiment, an identity authentication and key agreement method is provided, which is applied to a system including a CA, an HLR, multiple VLRs, and an MS affiliated to the HLR, where the CA can be the HLR, multiple VLRs, and MS issues public and private keys.
[0068] Such as image 3 As shown, the identity authentication and key agreement method according to this embodiment includes:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com