Access method of opportunistic cognitive multi-carrier link layer protocol
A link layer protocol and access method technology, applied in the access field of opportunistic cognitive multi-carrier link layer protocol, can solve the problem of relatively large fluctuations in the probability of successful channel access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
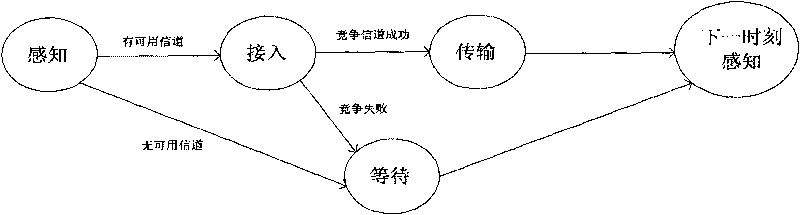
[0052] Such as figure 1 As shown, each unauthorized node has three states, perception, access and transmission, and the three states have fixed time overhead, respectively T s ,T a ,T t . The node first perceives the available channel information, enters the access state after sensing the available channel, and starts to transmit and send data after successfully competing for the channel, otherwise it waits for the next sensing time slot.
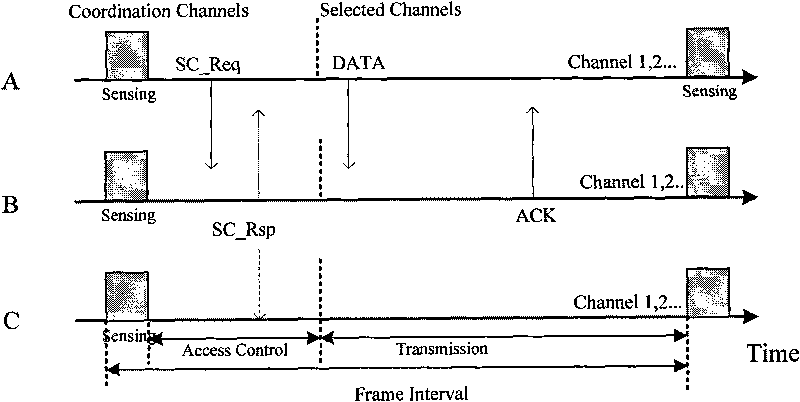
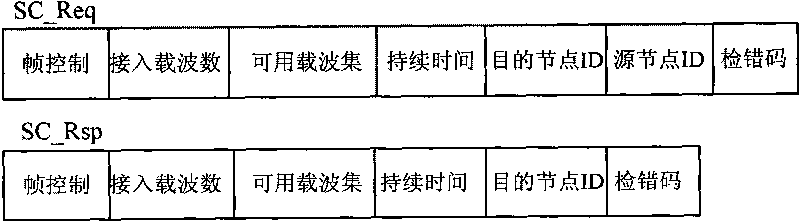
[0053] Such as figure 2 As shown, in the process of link negotiation, A and B are a pair of transmitting and receiving nodes, and C is an adjacent node of B. At the perception time T s Within, nodes A and B perceive multiple available idle subcarriers; when node A needs to send data to node B, node A obtains the number of subcarriers that compete for access according to the proportion of business demand is n t . Subsequently, node A selects the largest n according to the Access Probability List (APL) table t Each access subcarrier ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com