Context-aware real-time computer-protection systems and methods
A computer and environment technology, applied in computer security devices, computing, instruments, etc., can solve problems such as validity and reliability limitations, inability to identify malicious files, user annoyance, etc., to achieve the effect of minimizing performance impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
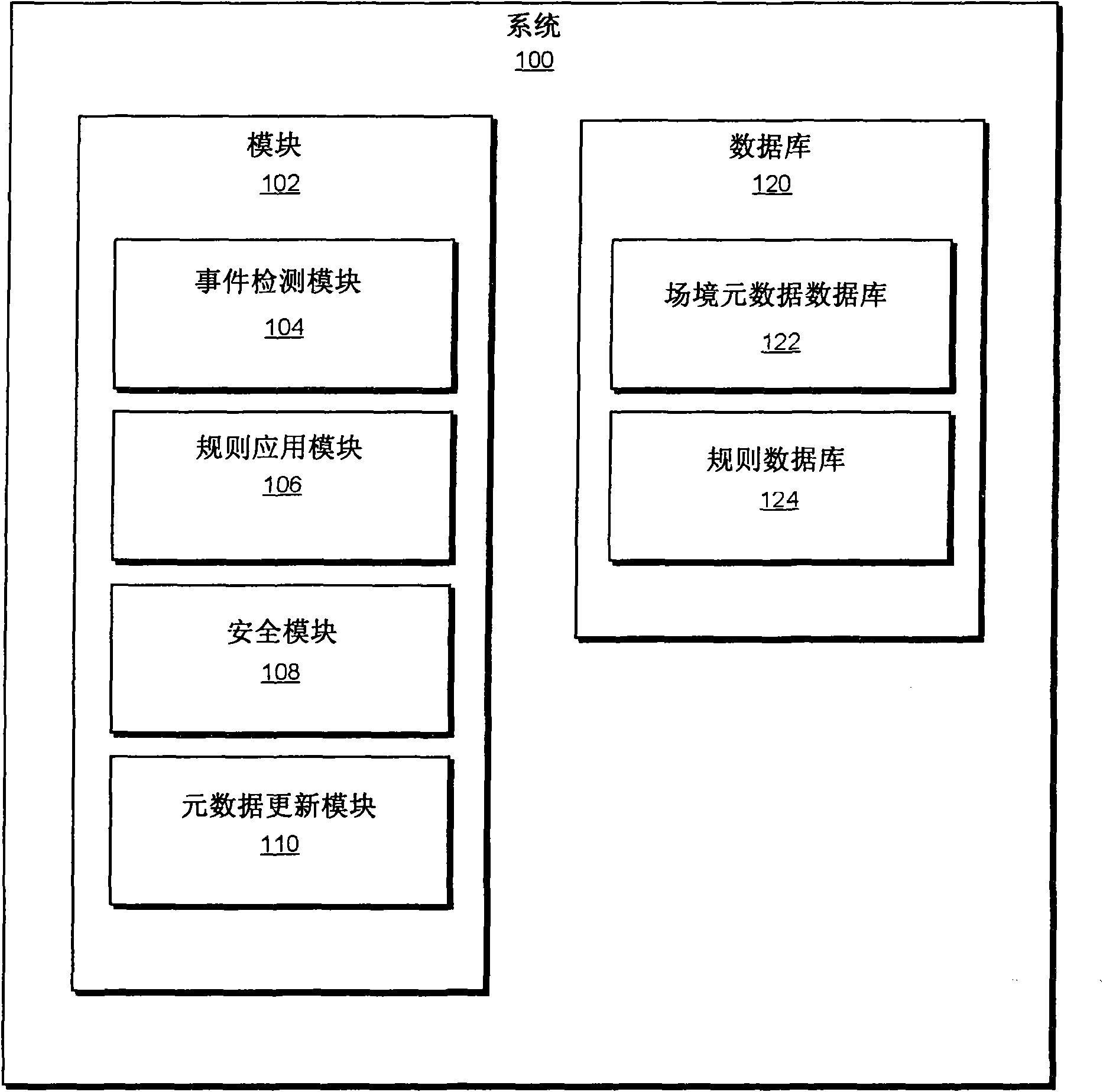
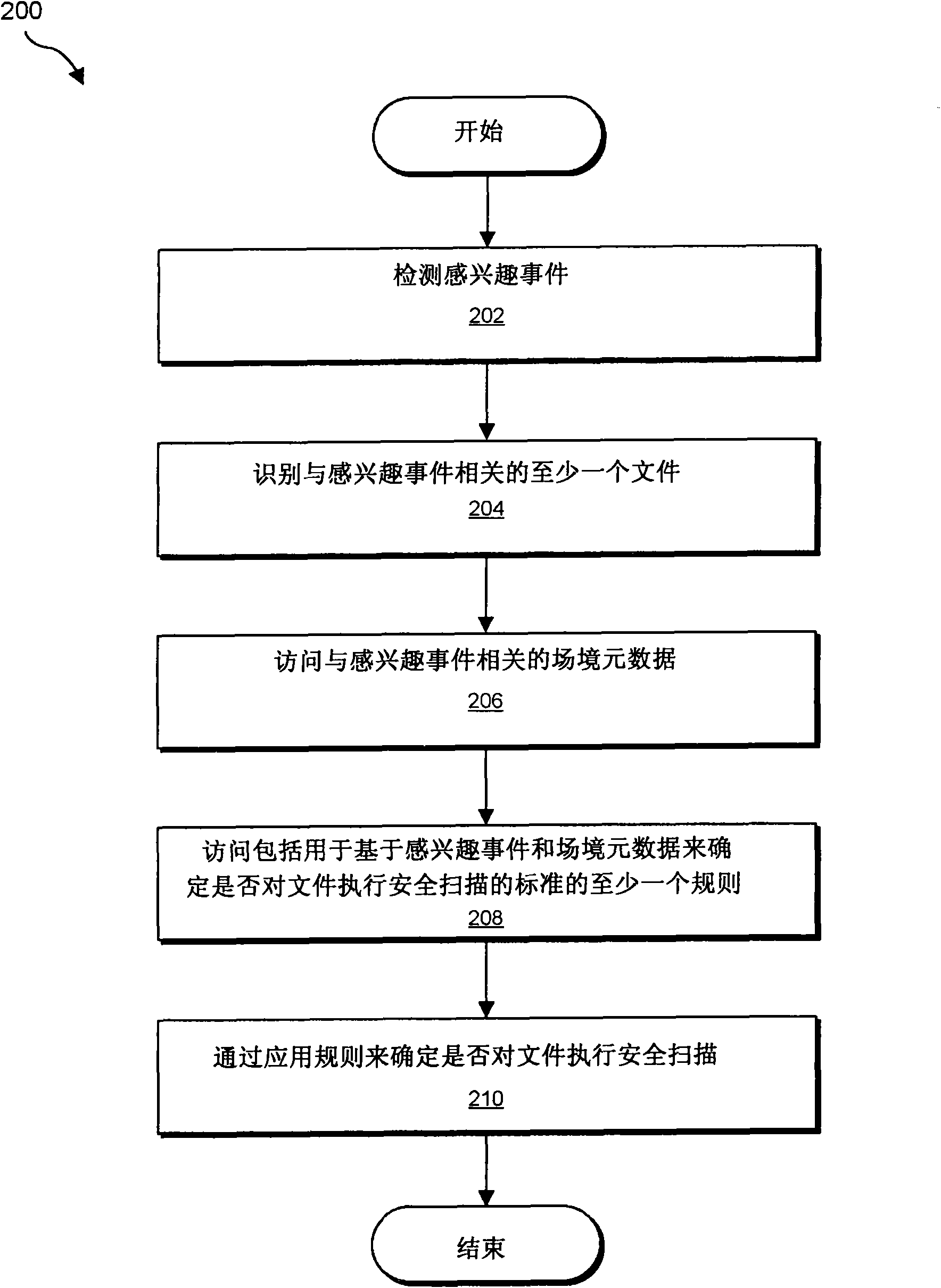
[0013] As described in more detail below, the present disclosure generally relates to systems and methods for determining whether to perform real-time file scanning in response to an event of interest by examining the full context of the event of interest. Information describing or identifying the larger context in which the event of interest occurred (hereinafter referred to as "context metadata") may include, but is not limited to, information about the files involved (such as file name, file creation date, the number of times it has been read or modified, the applications that have read or modified the file, typical usage behavior for the file, the results of previous security scans performed on the file, etc.) Information about applications related to files (such as whether the file program is a portal, whether the application generates network activity, whether the application contains known vulnerabilities, etc.).
[0014] The following will refer to figure 1 A detailed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com