Software protection method based on network, client side and server
A software protection, client-side technology, applied in the field of computer networks, can solve the problems of low effectiveness, inability to detect software tampering, low accuracy of client software, etc., to achieve the effect of accurate detection methods and improved effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
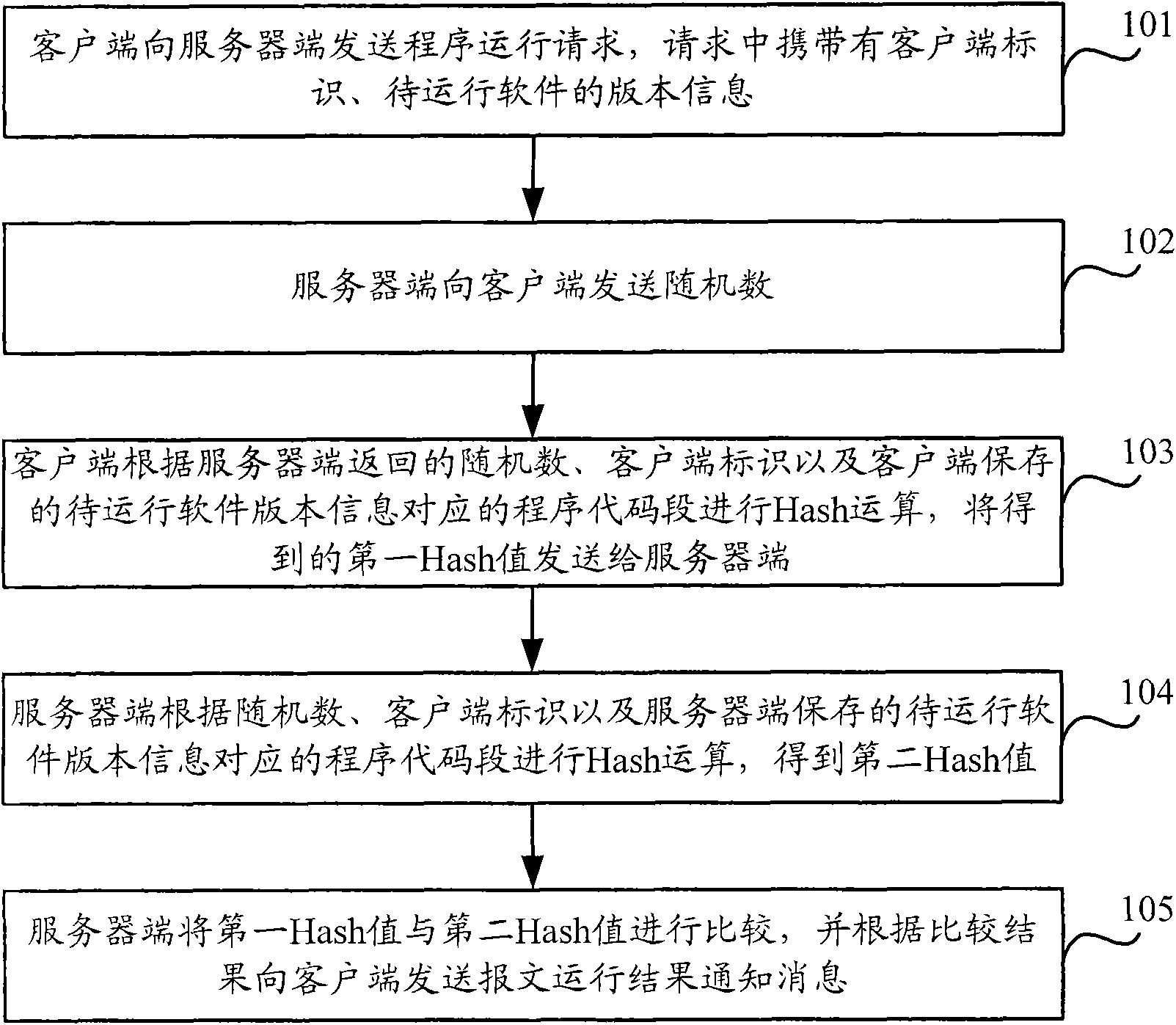
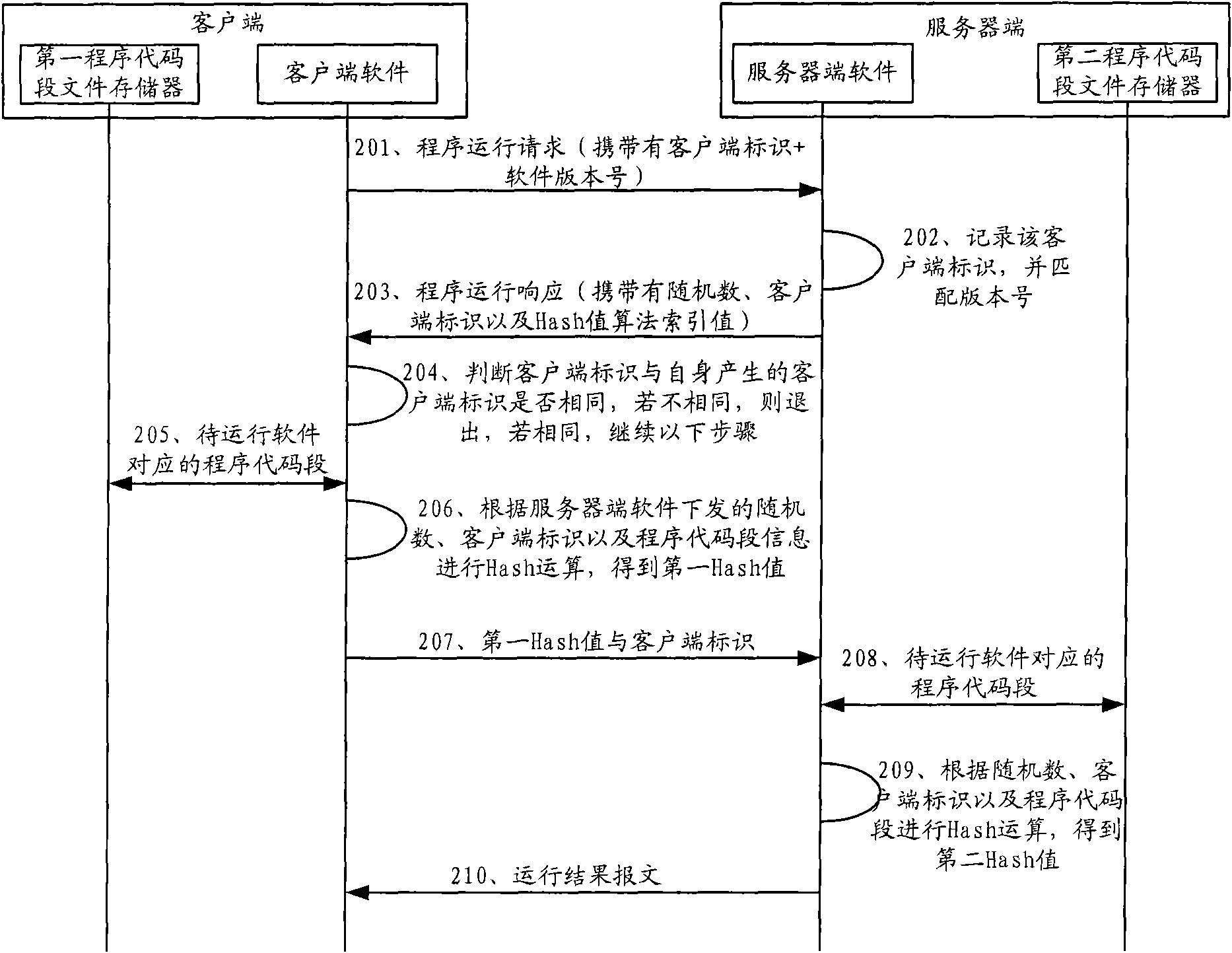
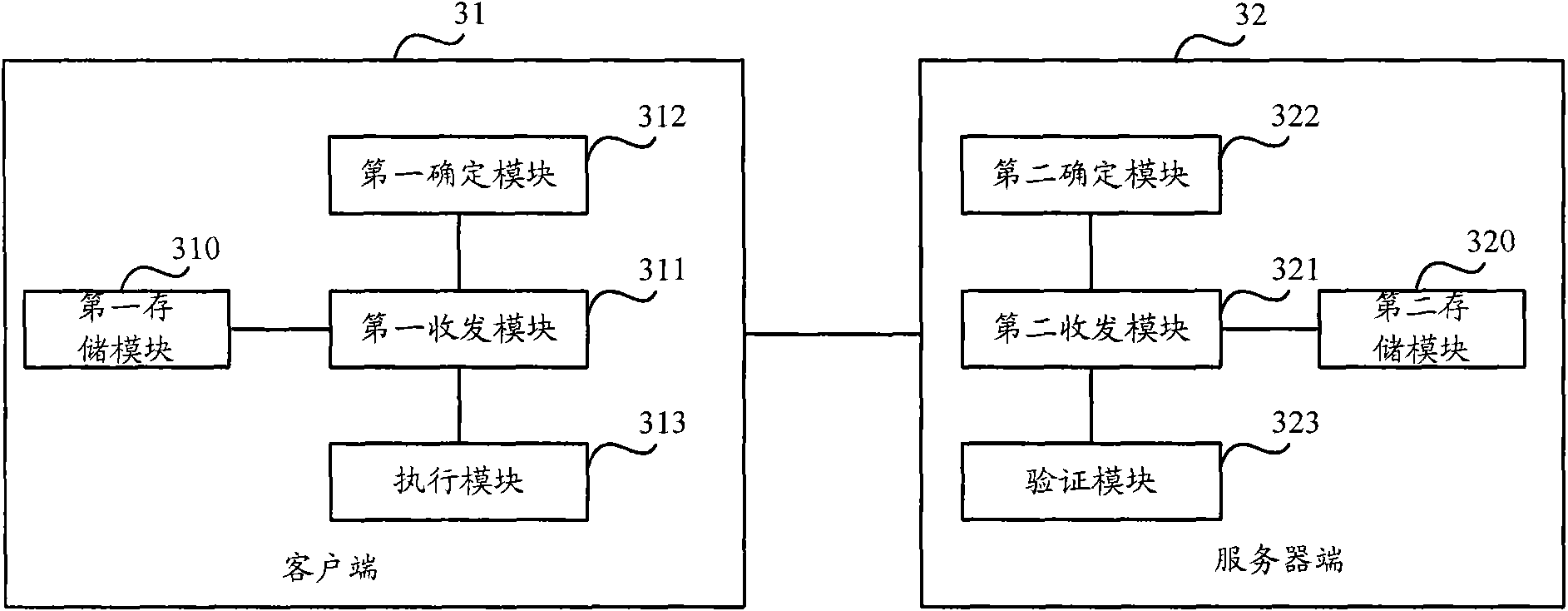
[0024] In order to solve the above-mentioned problems existing in the prior art, an embodiment of the present invention provides a network-based software protection method, which mainly includes: respectively storing program code segments corresponding to each software at the client and server; When detecting whether the software has been tampered with, the client sends a program running request with the client ID and software version information to be run to the server; The client sends random data; the client uses the set Hash algorithm to determine the first Hash value according to the client ID, the random data sent by the server, and the program code segment corresponding to the version information to be run locally stored on the client, and The first Hash value is sent to the server; the server uses the set Hash algorithm to determine the second Hash according to the program code segment corresponding to the client identification, random data and the version information t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com