Method, device and system for realizing data shared access
A data access and data sharing technology, applied in the field of communication, can solve the problems of unguaranteed data access performance, unfavorable unified data maintenance and security, etc., and achieve the effect of convenient unified maintenance management, simplified access, and easy expansion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
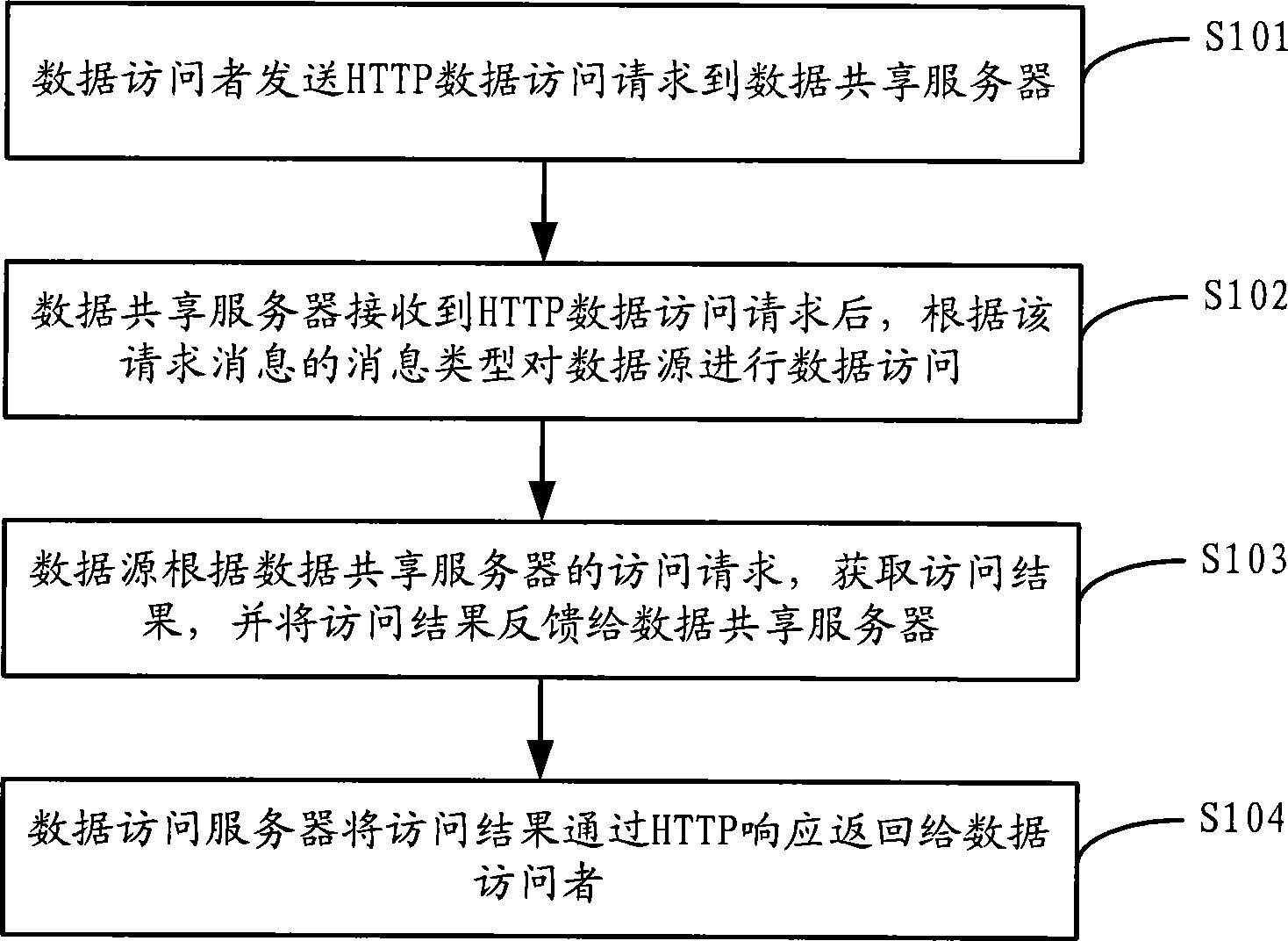
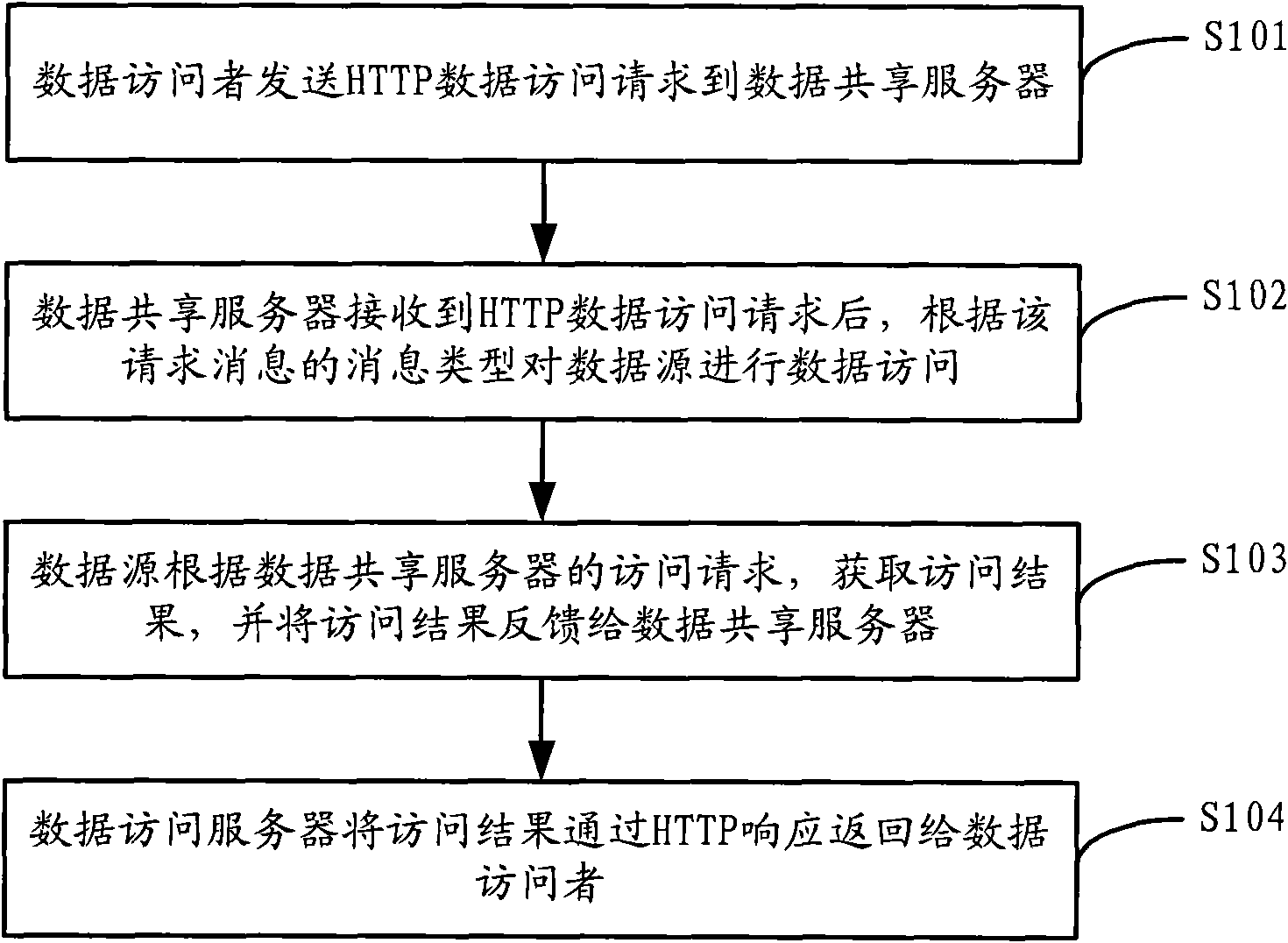
[0040] As shown in Figure 1, the flow chart of the HTTP protocol-based data sharing access method provided by the present invention specifically includes the following steps:
[0041] Step S101, the data visitor sends an HTTP data access request to the data sharing server.
[0042] Step S102, after receiving the HTTP data access request, the data sharing server performs data access to the data source according to the message type of the request message.
[0043] Wherein, the message type of the HTTP data access request message includes one or more of the following: HTTP GET data query, HTTP PUT data update and HTTP DELETE data deletion.
[0044] Correspondingly, in this step, the data sharing server sends an access request to the data source according to the type of the received message, and the types of the access request message include: data query, data update and data deletion.
[0045] Based on the above characteristics, the implementation process according to different ...
Embodiment 2
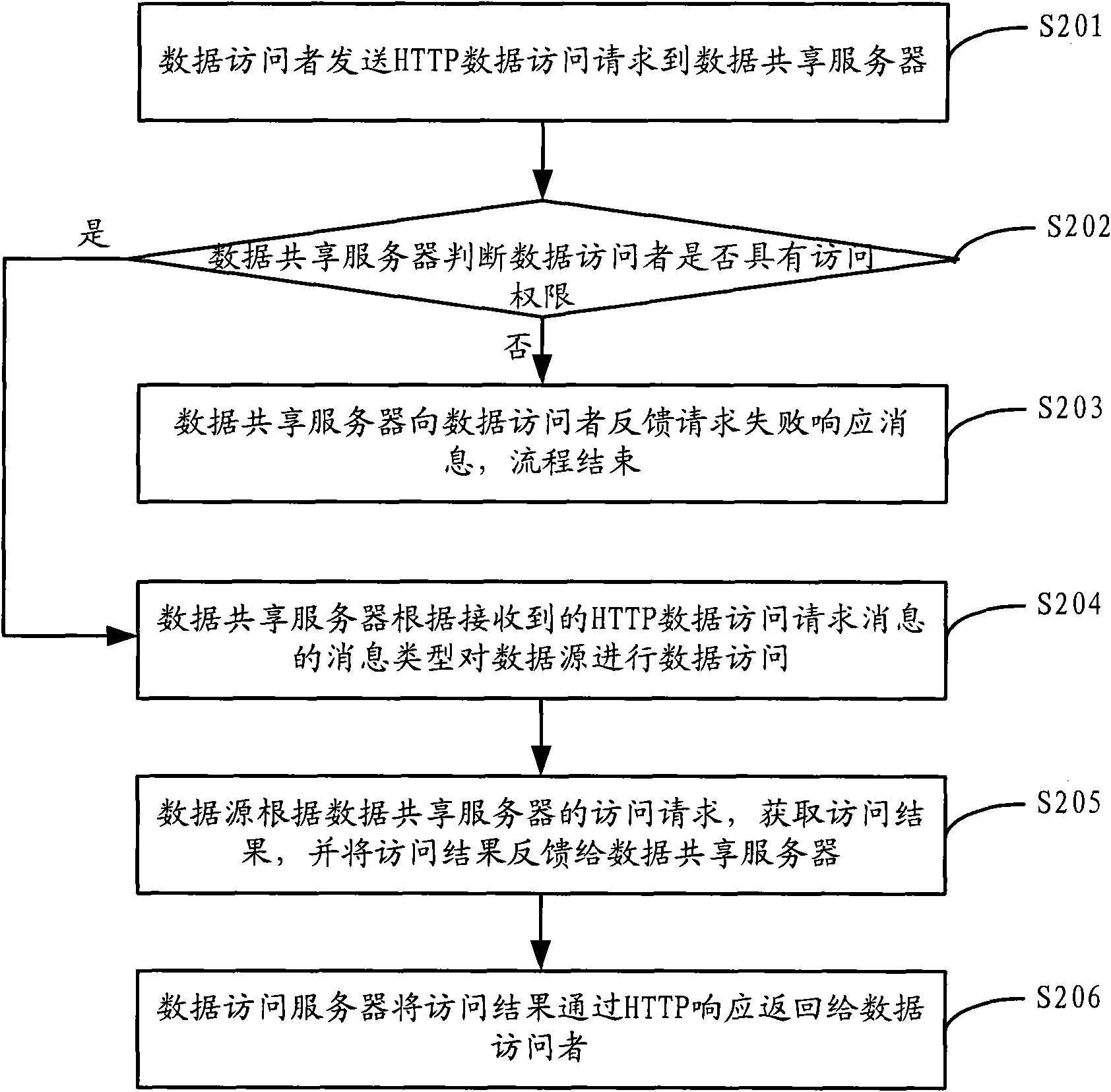
[0053] As shown in Figure 2, another flow chart of the method for realizing data sharing access based on the HTTP protocol provided by the present invention specifically includes the following steps:
[0054] Step S201, the data visitor sends an HTTP data access request to the data sharing server.
[0055] Step S202, the data sharing server determines whether the data visitor has access rights based on the pre-configured access policy, and if so, executes step S204; otherwise, executes step S203.
[0056] Wherein, the data sharing server preferably uses the IP address of the data visitor to identify different data visitors. The data sharing server can set highly trusted data visitors as having access rights, and of course it can also be set according to other requirements, and the present invention does not limit its specific implementation.
[0057] Step S203, the data sharing server feeds back a request failure response message to the data visitor, and the process ends.
...
Embodiment 3
[0064] As shown in Figure 3, another flow chart of the method for realizing data sharing access based on the HTTP protocol provided by the present invention specifically includes the following steps:
[0065] Step S301, the data visitor sends an HTTP data access request to the data sharing server.
[0066] Step S302, the data sharing server judges whether the data visitor has access authority, if yes, execute step S304; otherwise, execute step S303.
[0067] Step S303, the data sharing server feeds back a request failure response message to the data visitor, and the process ends.
[0068] Step S304, the data sharing server parses the received HTTP data access request message, obtains the message type, and judges whether the current data visitor has the access right of the message type based on the pre-configured access policy, and if so, executes step S306; otherwise, Execute step S305.
[0069] Step S305, the data sharing server feeds back a request failure response message...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com