Word-oriented key stream generating method and encrypting method
A key stream and message word technology, applied in the field of information security transmission, can solve problems such as the inability to meet the needs of implementation speed, and achieve the effects of good security, good randomness and non-linearity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
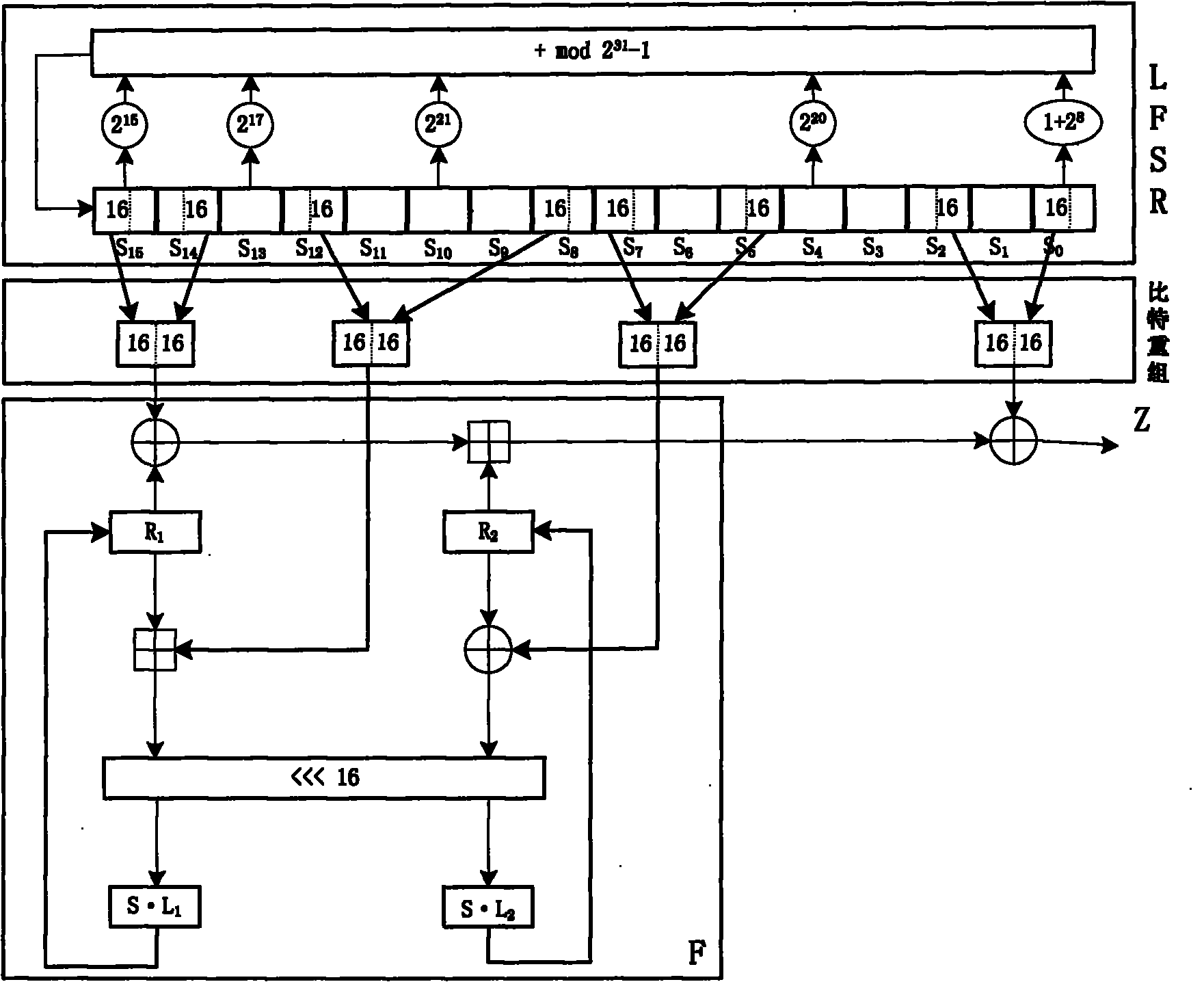
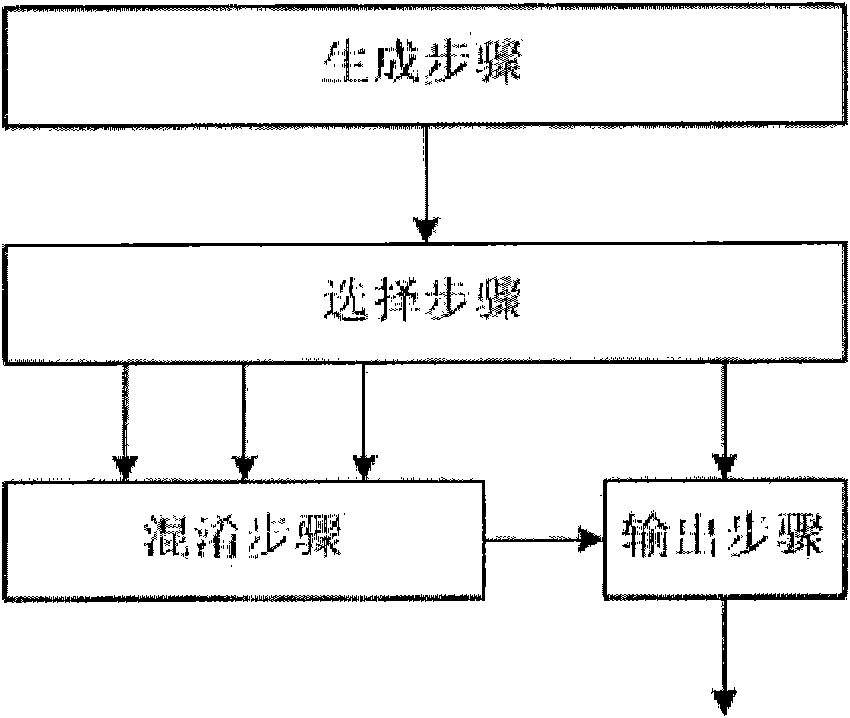
[0050] figure 1 It is a schematic diagram of the basic steps of the key stream generation method of the present invention, including each step and the input-output relationship between each step. Among them, the generation step generates a source sequence with good randomness and long period, which is input to the selection step. The selection step selects bits in the source sequence to form four outputs. Three of them are input to the obfuscation step and one is input to the output step. The obfuscation step performs a non-linear compressive transformation on three inputs to produce one output. The output step receives an output of the selection step and an output of the obfuscation step, and combines and compresses to obtain a key stream output.
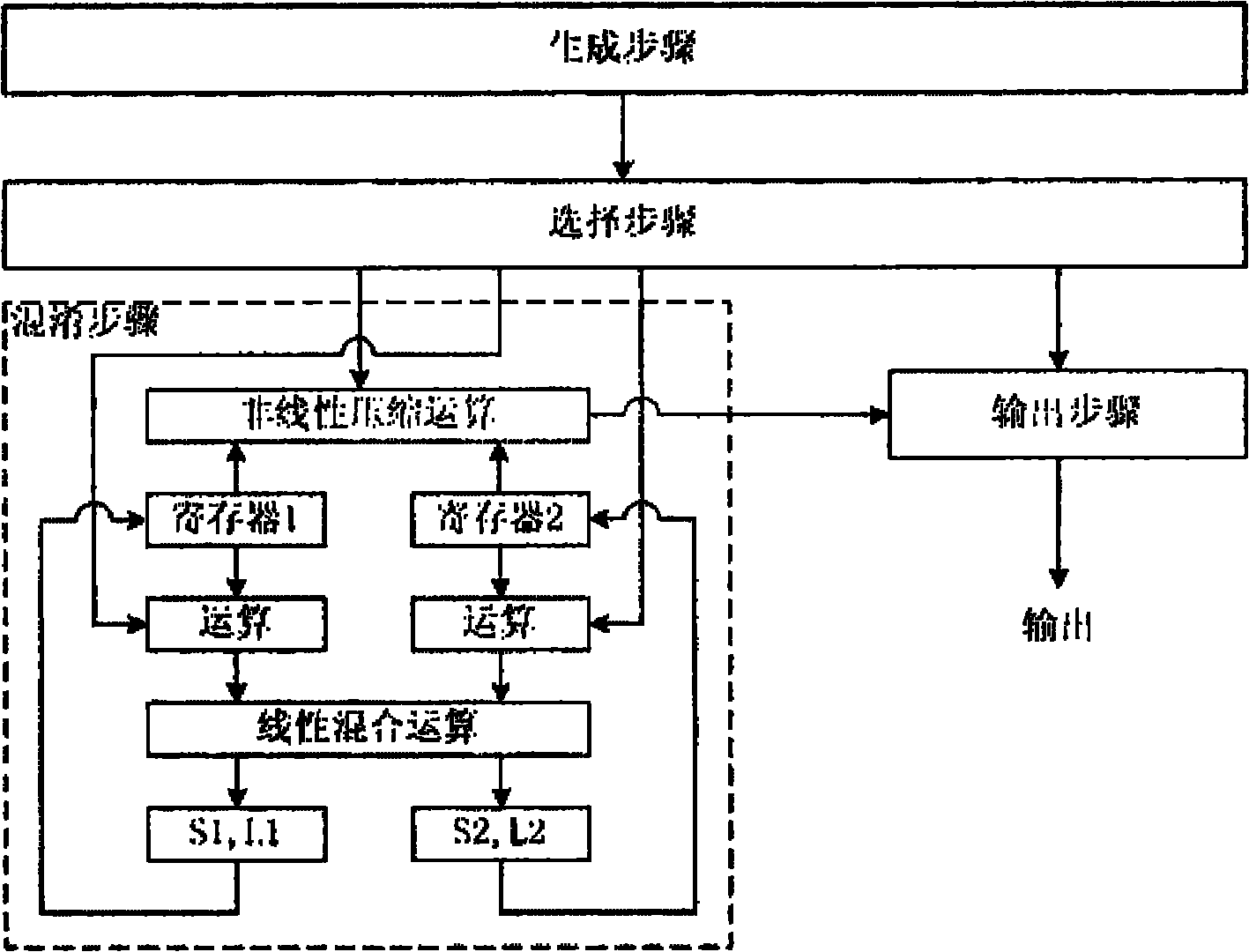
[0051] figure 2 is a schematic diagram of the detailed steps of the key stream generation m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com