Method and system for extracting cipher key by using DPA curve polarity
A key extraction and polarity technology, which is applied in the field of information security, can solve the problems of peak size and polarity not being used, and achieve the effect of improving time complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
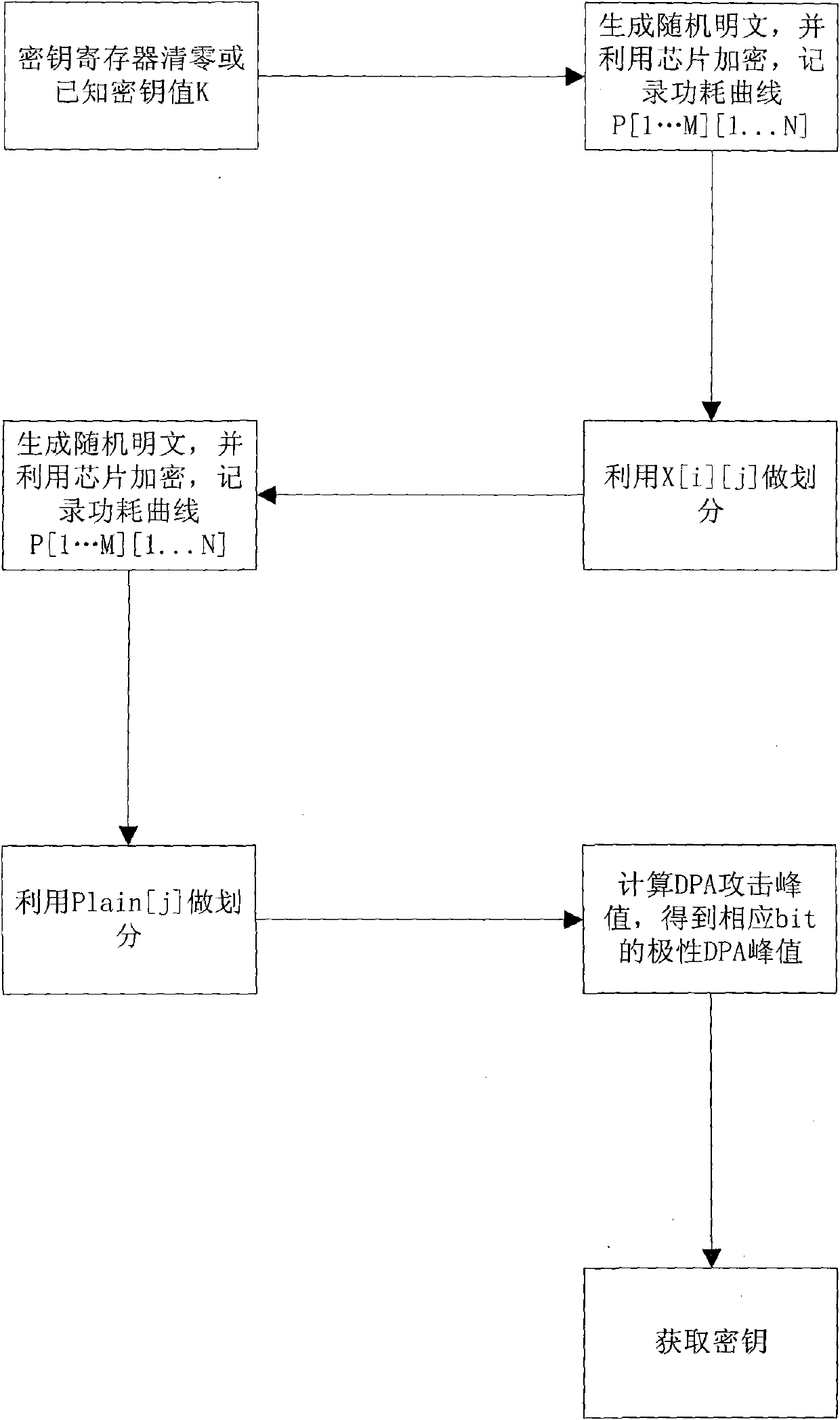
[0052] Below in conjunction with accompanying drawing, the present invention will be further described with specific embodiment:
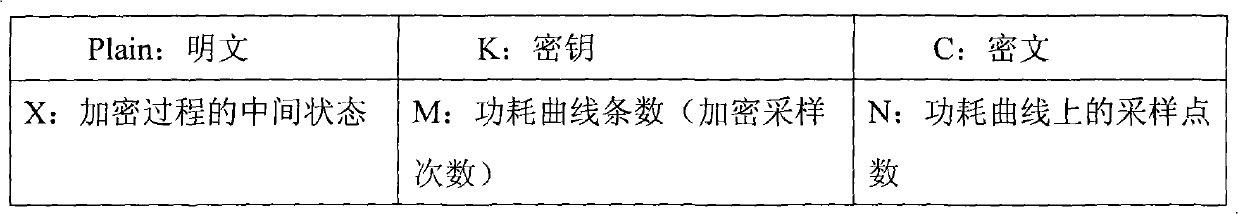
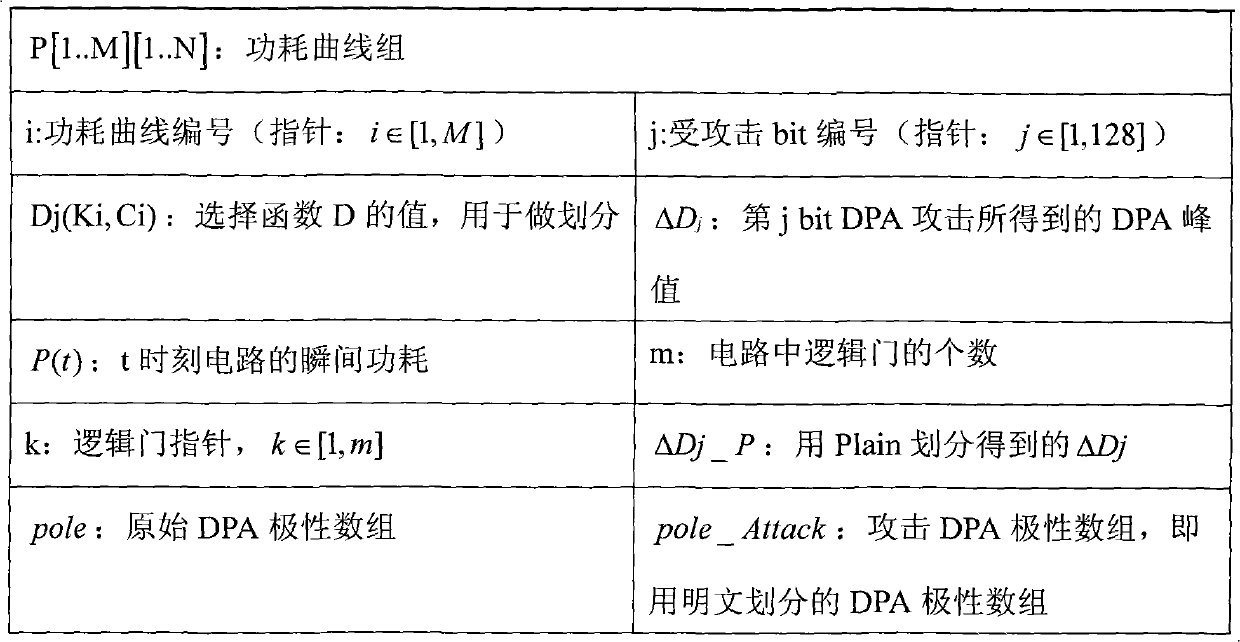
[0053] In the original DPA attack proposed by Paul Kocher, first use a digital oscilloscope to record the power consumption curve of the encryption chip during each encryption process, and write down N sampling points, replace the plaintext, record a total of M groups of power consumption curves, and then select A D function divides the collected samples, calculates the differential power consumption curve according to the division, obtains ΔD, finds the Ki value that can be the largest ΔD, and then obtains the correct key. In the polar DPA attack used here, the original DPA attack is completed first, the obtained plaintext Plain is XORed with the guessed key K, and then the plaintext Plain is used to divide to obtain ΔD_P, and the DPA curve corresponding to bit j and The polarity of the peak, thus obtaining the key. Accordingly, the specific step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com