Alarm shielding method of access device
A technology for accessing equipment and equipment, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of high processing capacity requirements, redundant space occupation, and low configuration efficiency, so as to improve storage efficiency and reduce processing Stress, storage space saving effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be described in further detail below in conjunction with the accompanying drawings.
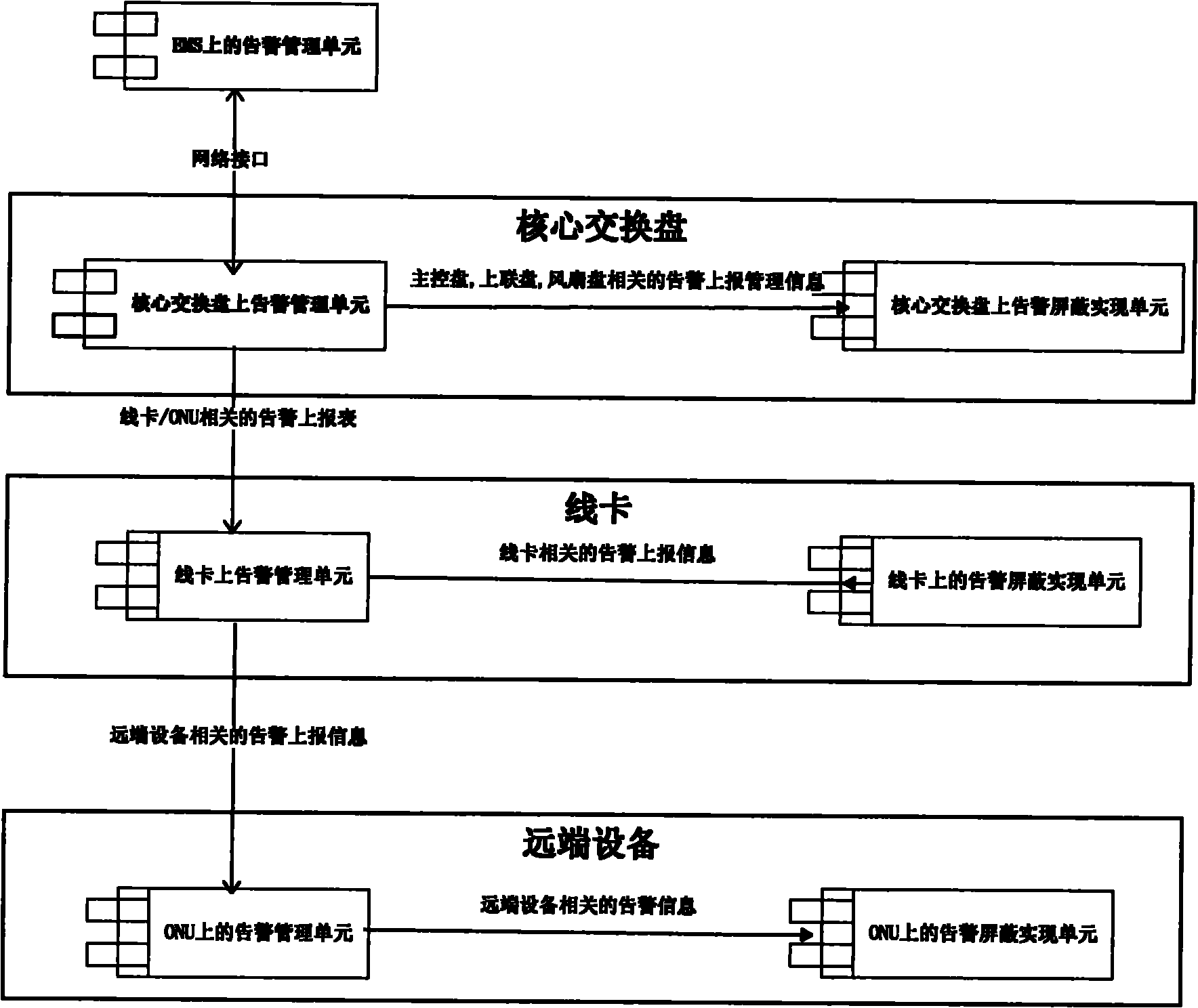
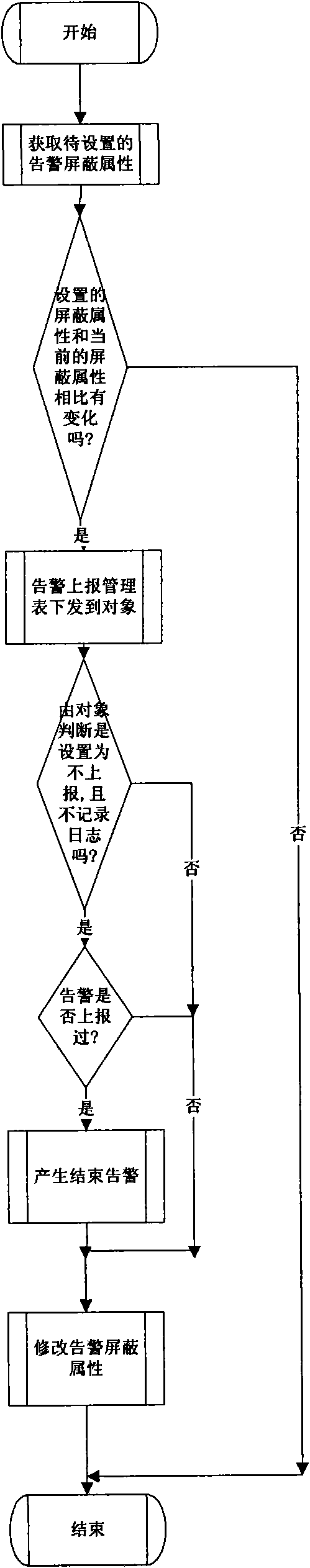
[0062] Because the user does not care about all the alarms reported by the device, a mechanism is needed to block the information that the user does not care about. The present invention designs in detail a set of device-side alarm shielding processing methods and a storage mechanism for related data.
[0063] First, the alarm shielding process adopts a distributed shielding processing method, which distributes the processing pressure to each subsystem and reduces the pressure on the core switching disk.
[0064] Second, for the storage of massive alarm masking information in the system, the method of not storing default configuration and compressing and storing common configuration is adopted to improve the utilization rate of system resources.
[0065] Thirdly, the present invention also proposes a fast and flexible configuration method for configuring and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com