User authentication module setting method and system
A user authentication module and user authentication technology, which are applied in the field of setting method and setting system of user authentication module, can solve the problems of difficult management, poor security, low usage rate of key code segment, etc., so as to improve utilization rate and ensure security. and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
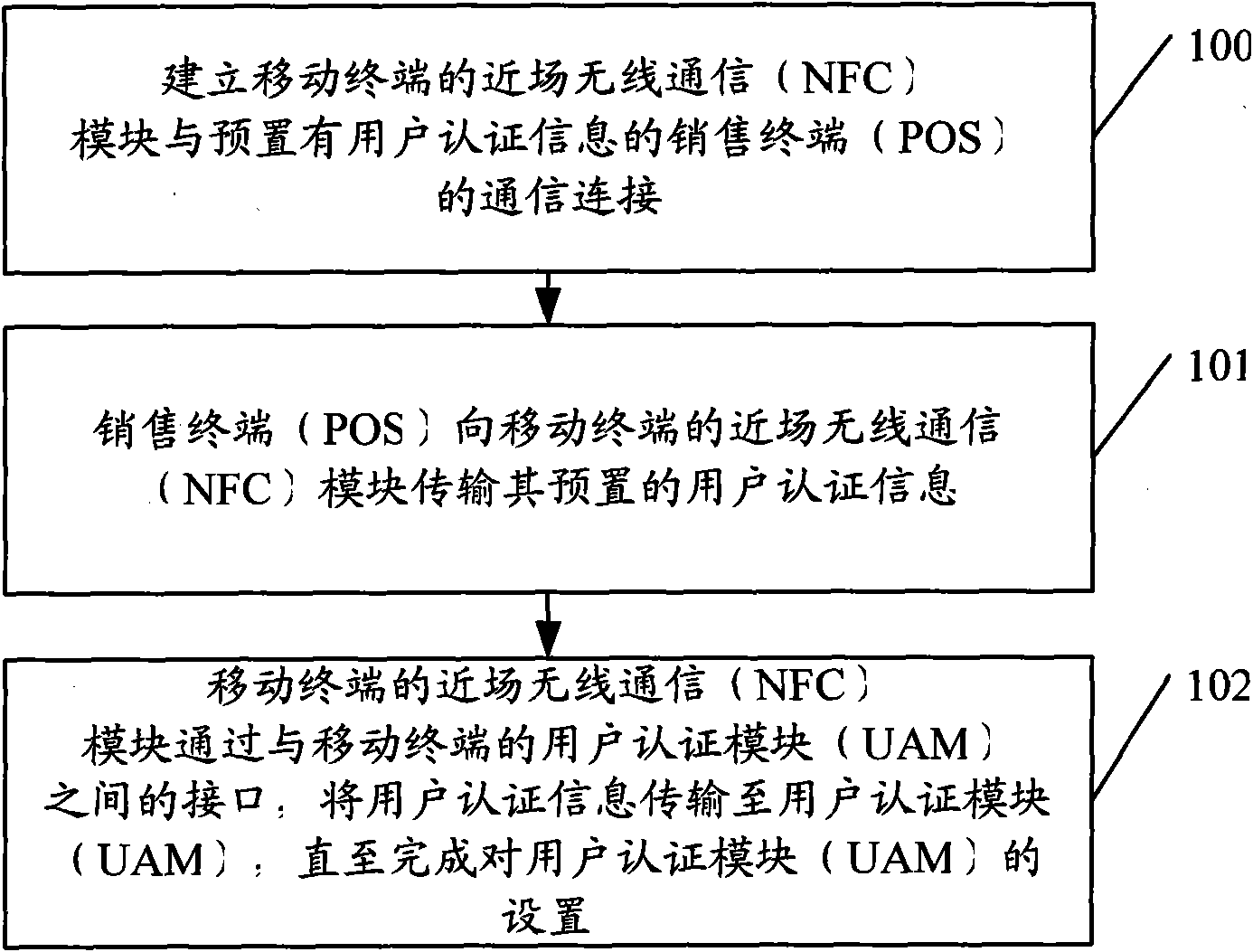
[0023] The setting management of the UAM module has always left operators, service providers and mobile terminal manufacturers at a loss. The three technical solutions for setting the UAM module provided by the existing technology have their own disadvantages, and none of them can improve the security of the UAM setting. Convenience and utilization of the number segment. Based on this technical situation, the present invention provides an efficient and safe user authentication module setting method and system.
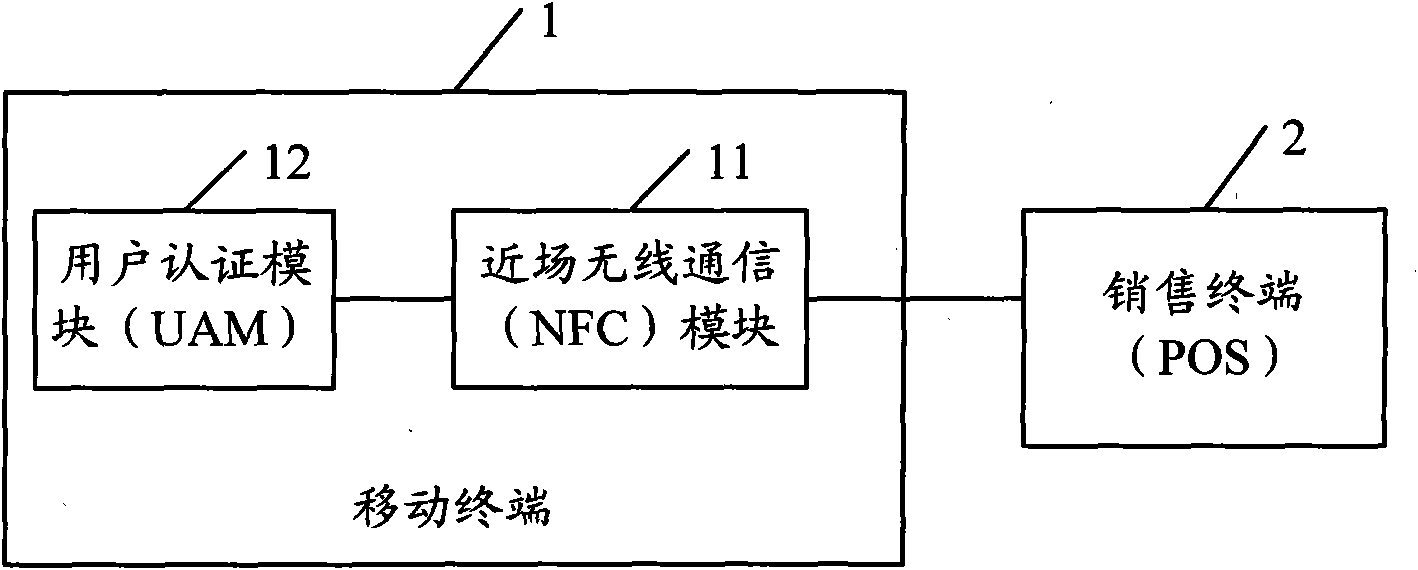
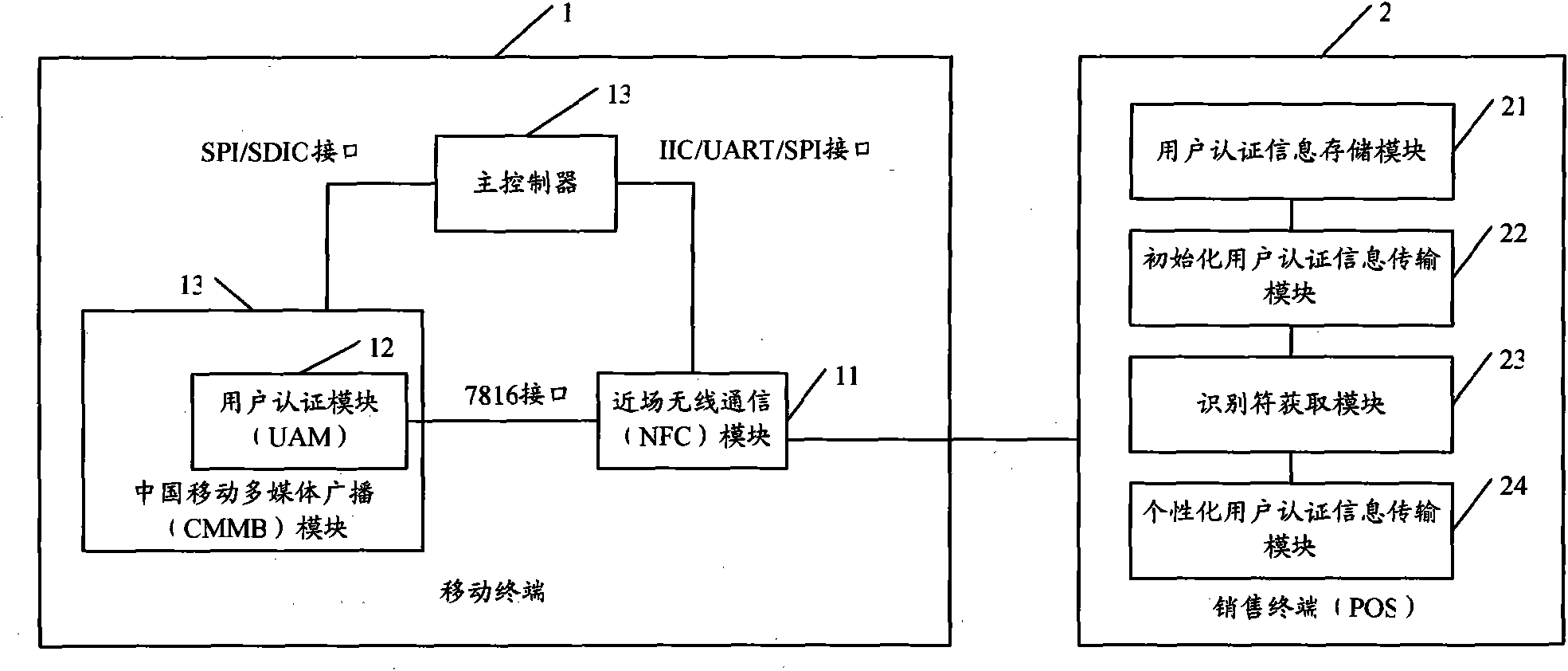
[0024] Before describing the embodiments of the present invention in detail, first explain that the core component UAM module (user authentication module, user authentication module) involved in the present invention means that when the mobile terminal wants to use certain functions, especially the charging function, it needs to first After user authentication, the corresponding functions can be used, these functions include but not limited to CMMB (China Mobile Multim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com