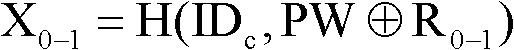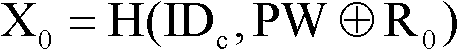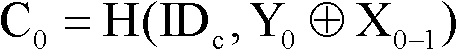Bidirectional ID (Identity) authentication method based on dynamic password and digital certificate
A technology of two-way identity authentication and digital certificate, applied in the field of computer system network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0045] In this example, both the default server and the client already have their own certificate chains, which means that the default server has the server certificate and the upper-level CA certificate, and the client has the client certificate and the upper-level CA certificate.
[0046] First, the client sends a registration request to the server, and the user enters the user's identity information ID on the client c and password PW, when the server receives the registration request, it judges the received ID c Whether it has been registered, if so, go back to the step where the client sends a registration request to the server, and prompt the client to re-enter, if not, the client generates a random number R 0-1 and R 0 , and calculate as follows: Y 0 =H(ID c , X 0 ), get data R 0 、C 0 、X 0 , the client saves the data R 0 、C 0 , and put the data X 0 Send to the server through the network security channel, the server receives and saves the data X 0 , the reg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com