Method and system for controlling SILSN (Subscriber Identifier & Locator Separation Network)
A technology for identifying and separating networks, applied in the field of communications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
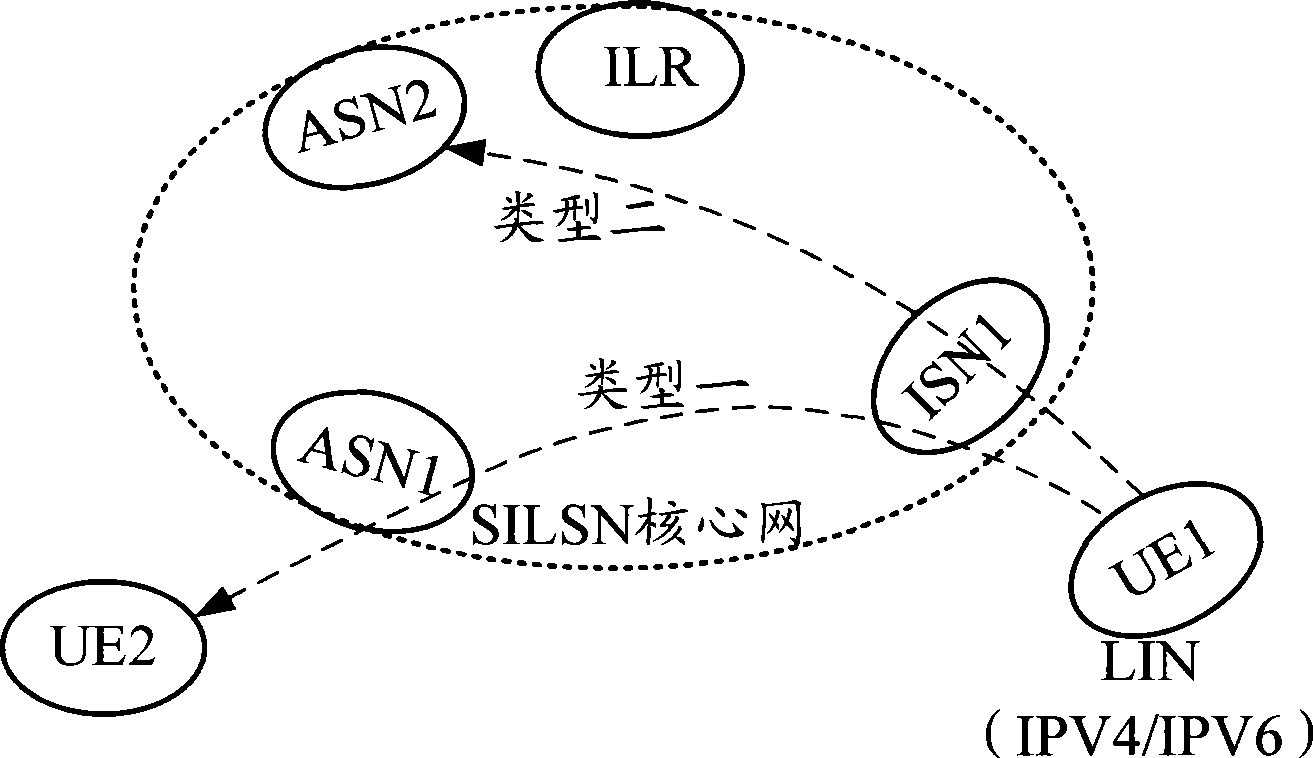
[0136] This embodiment 1 is described with an application example in which the administrator user of the SILSN located in the LIN initiates access, such as Figure 4 Shown:
[0137] Step 401: The user UE1 located in the LIN needs to access the core network node in the SILSN network, and sends a network management request message to the ISN, wherein the network management request message can be encapsulated in an IP data packet, and its destination address is the address of the CNMP, After the ISN receives the network management request message, if it is detected that the receiver of the message is CNMP, step 402 is performed;
[0138] It should be noted that CNMP should pre-determine the format of this network management request message. When ISN finds that the source address / source port of the data packet from LIN is not in OPT, CNMP checks whether the data is in this message format. If not, then throw away. If it is, extract the source address port, and use this source add...
Embodiment 2
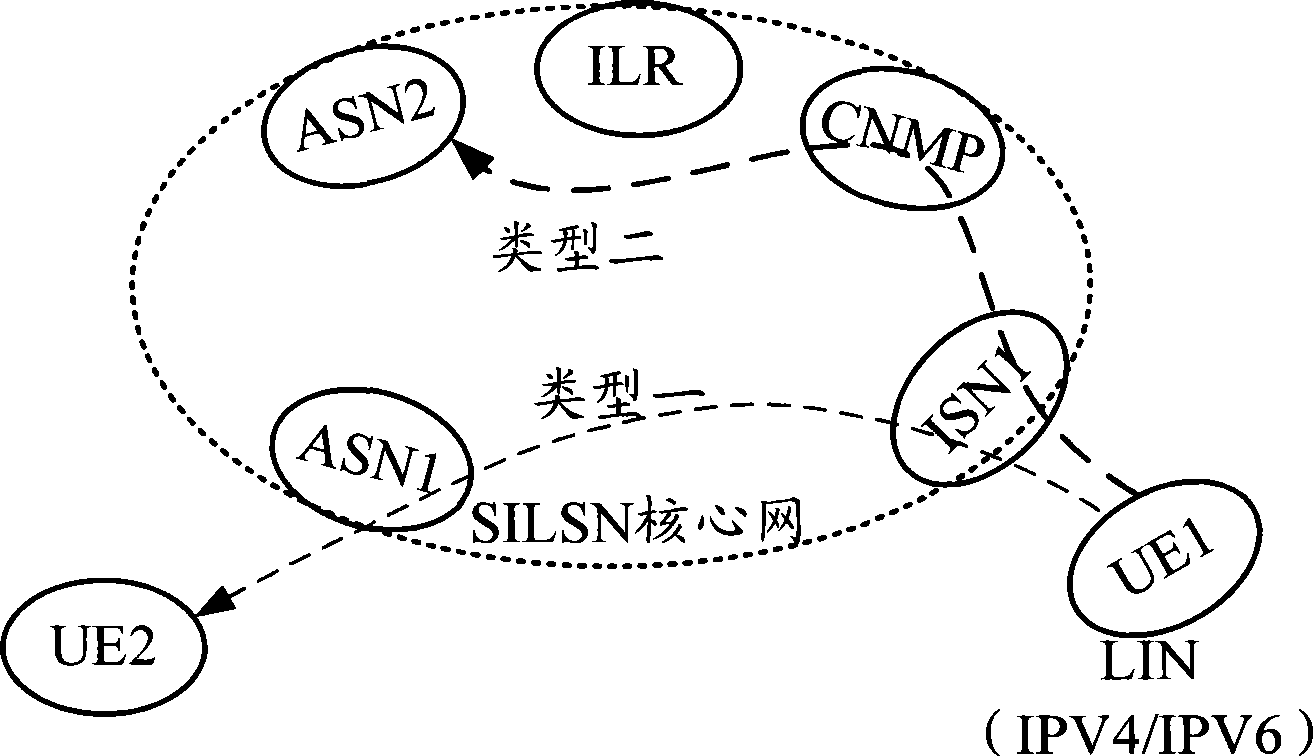
[0157] This embodiment is described with the application example that the common user of LIN network initiates the visit, as Figure 5 Shown:
[0158] Step 501, the ISN receives a data packet from the LIN, and extracts its destination address.
[0159] Step 502, the ISN judges whether the destination address of the data packet is a CNMP address, if yes, execute step 503, otherwise, execute step 507.
[0160] Step 503, when the destination address is the CNMP address, extract the source address and source port number of the data packet.
[0161] Step 504, judge whether the source address and port number are in the OPT, if so, execute step 505, otherwise, execute step 508.
[0162] Step 505, if it is in the OPT, further judge whether its status is "open", if not, then discard.
[0163] Step 506, if it is open, forward the data packet to CNMP.
[0164] Step 507, when the destination address is not the CNMP address, process it as the first type of data packet, and details will...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com