Method of call authentication and VOIP (voice over internet phone) system
A technology of authentication information and authentication request, applied in the field of communication, can solve the problem of user authentication that cannot be called party, and achieve the effect of satisfying the needs of authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
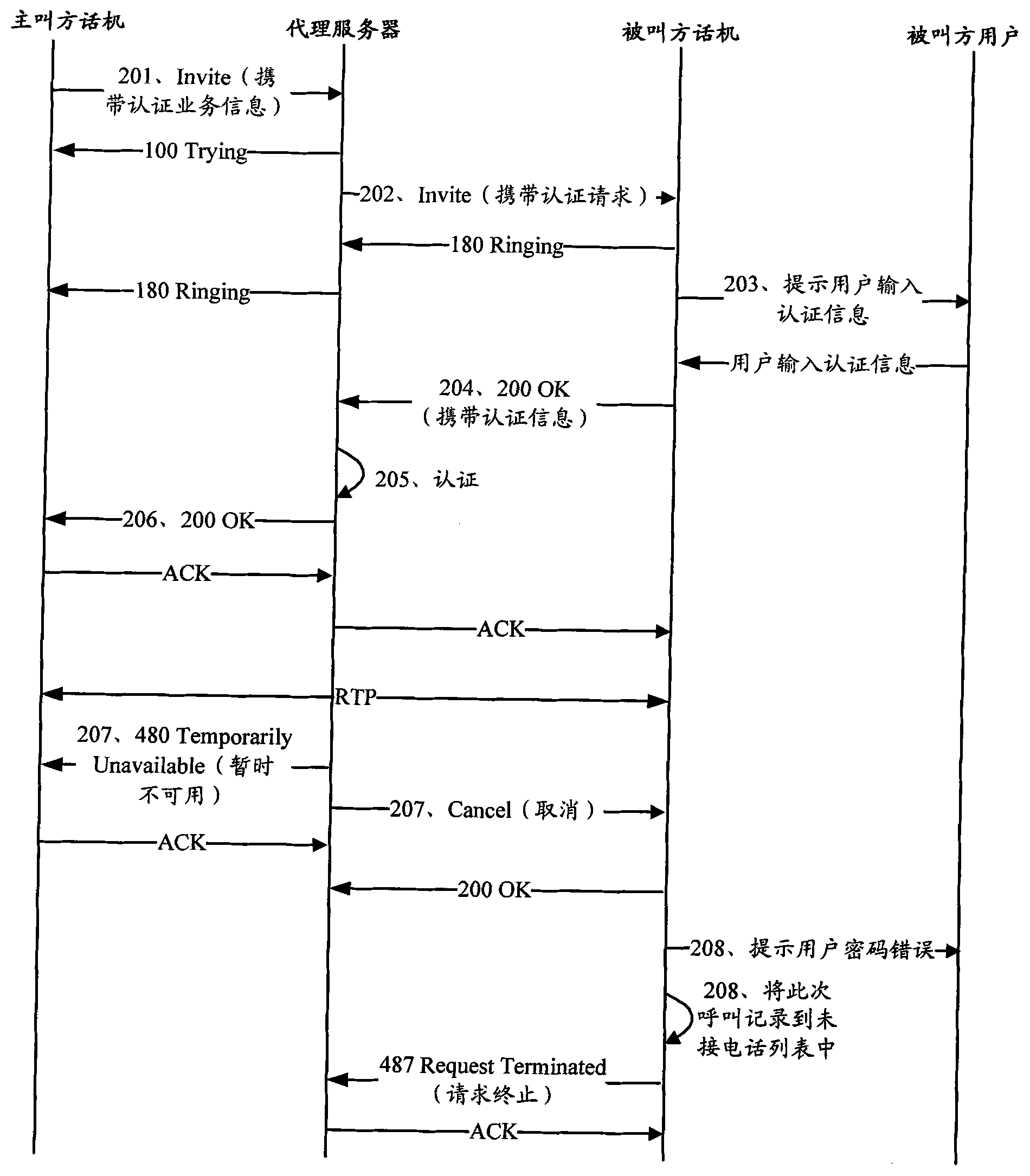
[0047] Embodiment 1 of the present invention provides a method for call authentication, such as figure 2 As shown, the method includes:
[0048] Step 201, the phone of the calling party sends an Invite message carrying authentication service information to the proxy server.
[0049] Specifically, the authentication service information is used to instruct the proxy server to authenticate the called party user. The way of carrying the authentication service information in the Invite message includes but not limited to: extending a SIP header field carrying the authentication service information, or adding the authentication service information to the number in the TO header field. The following takes adding authentication service information to the number in the TO header field as an example to illustrate how to carry the authentication service information in the Invite message:
[0050] To: (1)
[0051] As shown in (1), the called number in the To header field has changed fr...
Embodiment 2
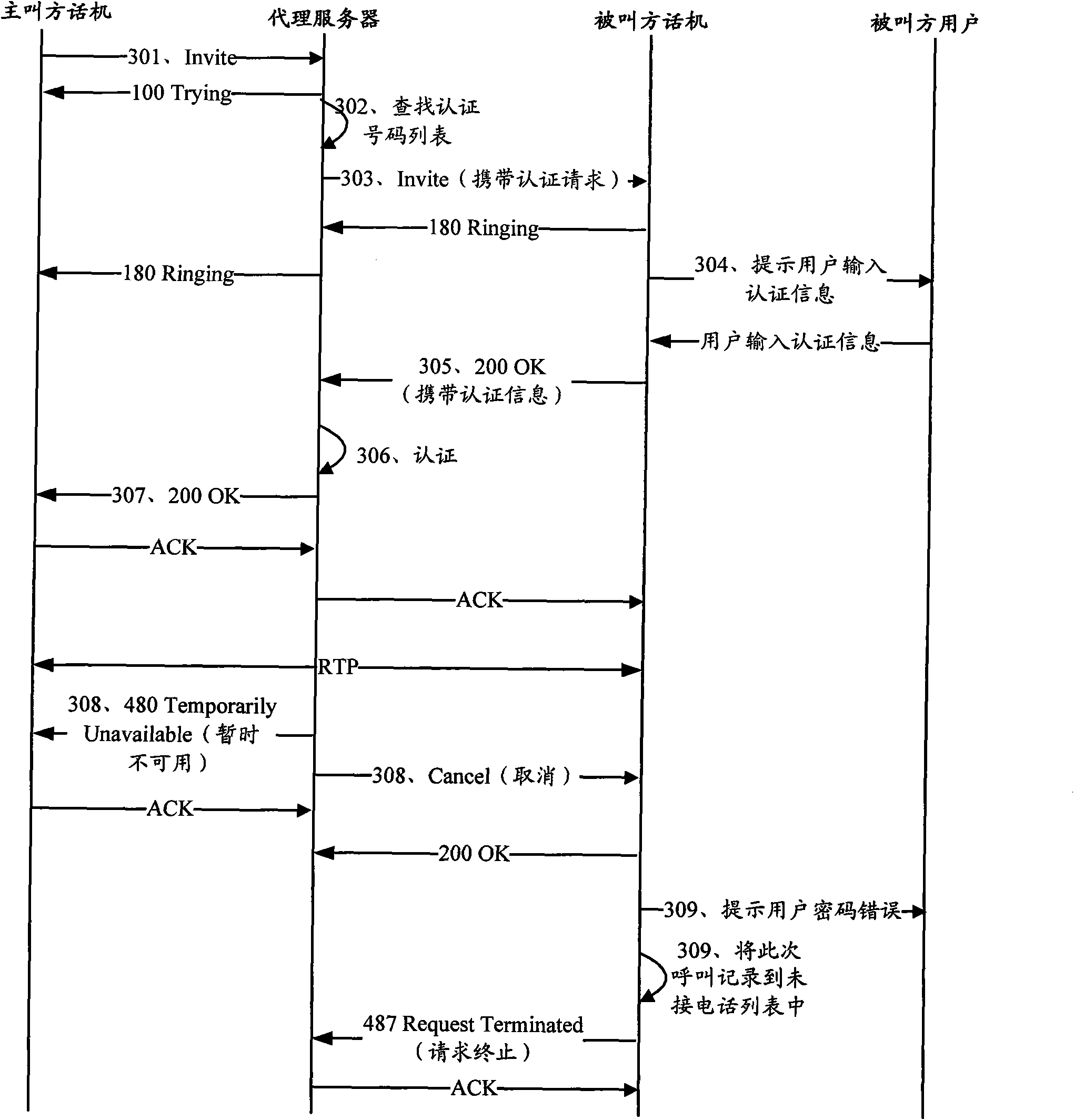
[0065] Embodiment 2 of the present invention provides a method for call authentication, such as image 3 shown, including:
[0066] Step 301, the phone of the calling party sends an Invite message to the proxy server.
[0067] Different from step 201, the Invite message does not carry authentication service information.
[0068] Step 302, the proxy server searches the stored authentication number list according to the number of the called party's phone, and if the number of the called party's phone is found in the authentication number list, step 303 is executed.
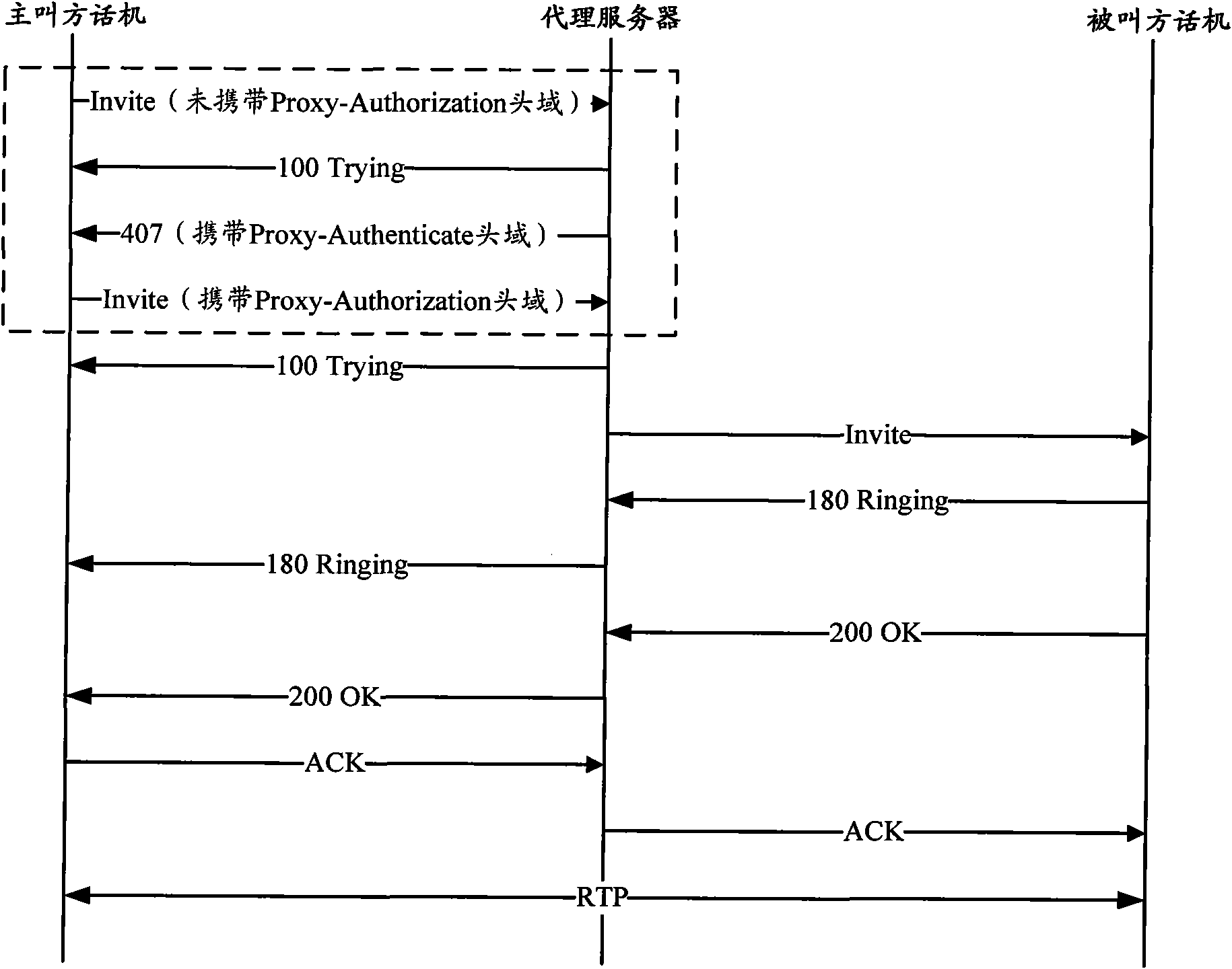
[0069] For example, for some important phone numbers, the user of the called party using the phone number can be pre-set in the proxy server for authentication. After the proxy server receives the call, it first judges whether the number of the called party's phone is a number that needs to be authenticated, if yes, execute step 303, if not, refer to figure 1 As shown in , the proxy server sends an invitation mes...
Embodiment 3
[0074] Embodiment 3 of the present invention provides a method for call authentication, and figure 2 and image 3 As shown, before the called party's phone sends a 200 OK message carrying authentication information to the proxy server, the called party's phone first authenticates the authentication information input by the user. by figure 2 The scenario shown is taken as an example, the method provided in the third embodiment is as follows Figure 4 shown, including:
[0075] Steps 401-403, and figure 2 Steps 201 to 203 in the illustrated embodiment are the same and will not be repeated here.
[0076] In step 404, the called party's phone performs authentication according to the authentication information input by the user. If the authentication is passed, step 407 is executed; if the authentication fails, step 405 is executed.
[0077] Wherein, at least two ways for the called party's phone to perform authentication according to the authentication information input by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com