Method for generating and authenticating digital image tampered content recoverable variable capacity watermarks
A digital image and authentication method technology, which is applied in image data processing, image data processing, instruments, etc., can solve the problems of redundant, vulnerable to constant mean attack, non-smooth image block recovery quality, and low positioning accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
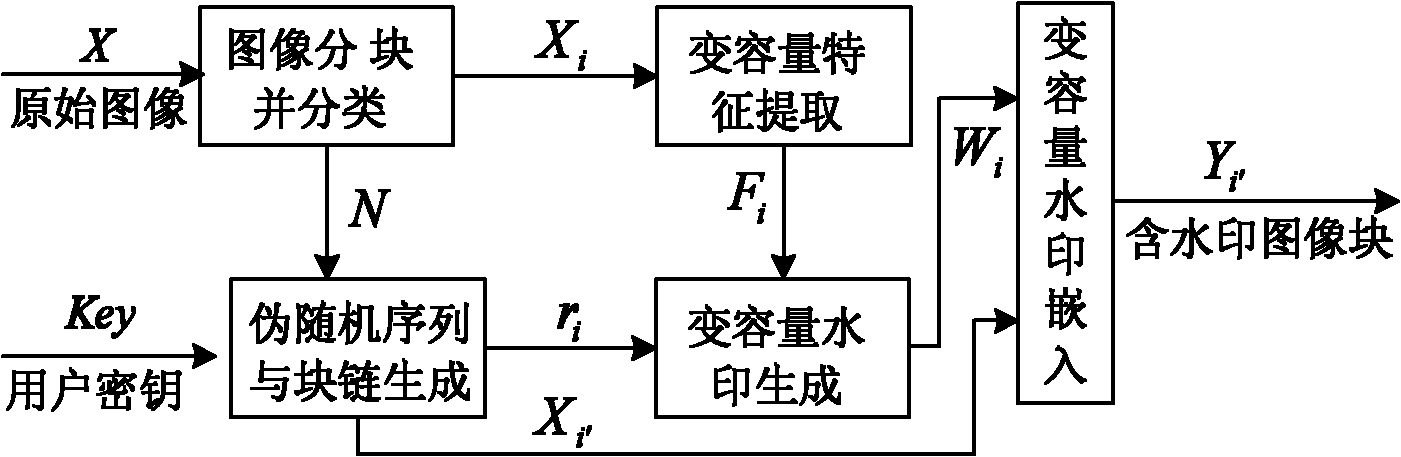
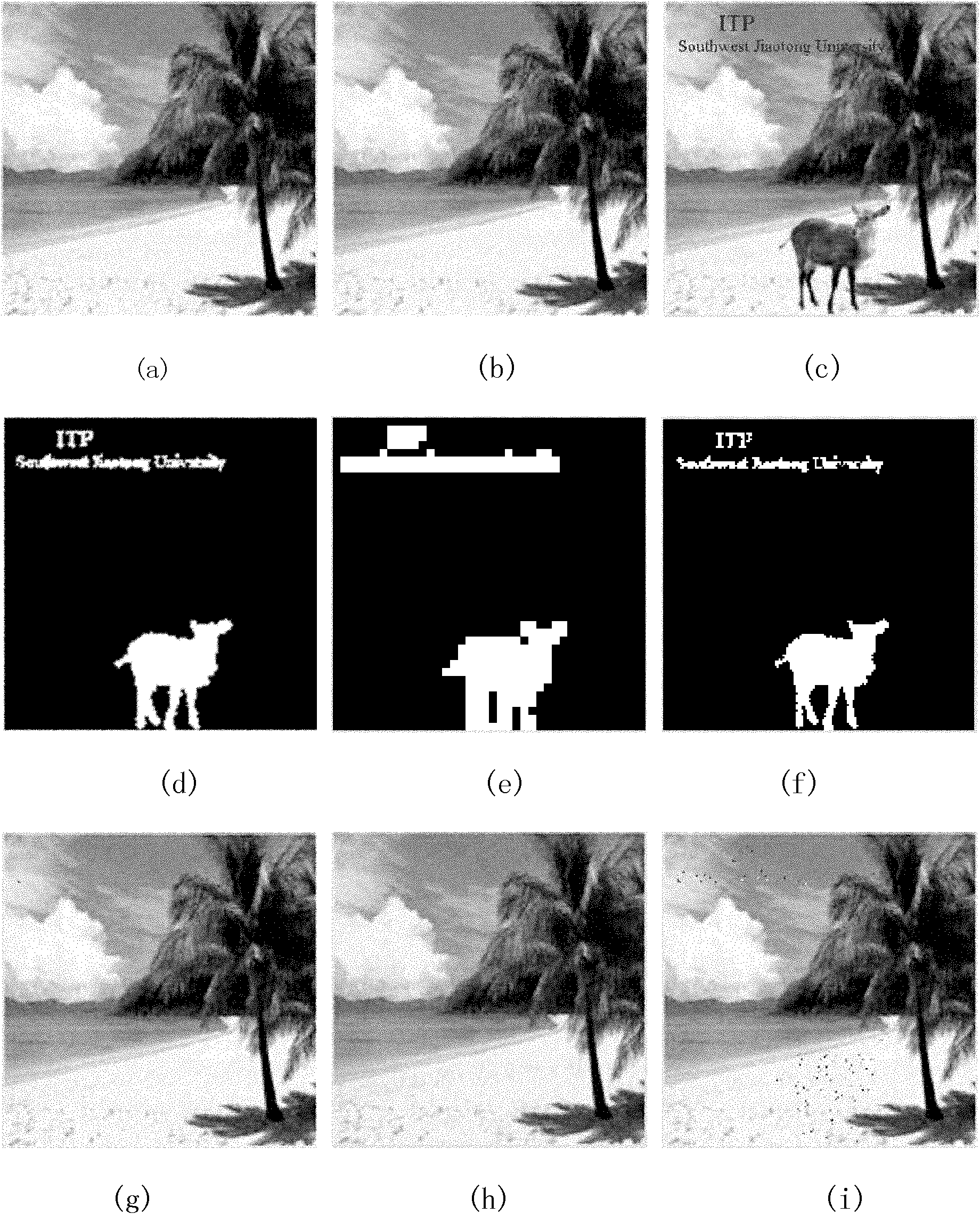
[0056] A variable-capacity watermark generation and authentication method with recoverable tampered content of a digital image, including four parts: watermark generation and embedding, watermark extraction and comparison, tampering detection and tampering recovery.
[0057] A. Watermark generation and embedding
[0058] figure 1 It is a block diagram of specific steps of watermark generation and embedding in the method of the embodiment of the present invention, including the following five steps:
[0059] A1. Image block and classification: Divide the original image X with a size of 2m×2n into m×n non-overlapping 2×2 image blocks X i ={x i1 , x i2 , x i3 , x i4}, wherein, i is the image block number, i=1, 2, ..., N, N=m×n is the number of image blocks; and the image blocks are divided into smooth image blocks and non-smooth images according to the content of the image blocks Two types of blocks;
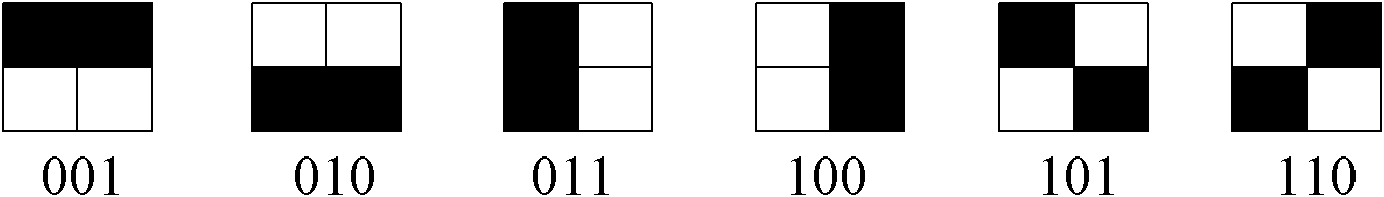
[0060] Image block classification in this embodiment: for 2×2 image blo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com