Mobile terminal and password input method thereof
A mobile terminal, password input technology, applied in the fields of instruments, digital data processing, computer security devices, etc., can solve the problems of password leakage, password being peeped by others, etc., to achieve the effect of protecting interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
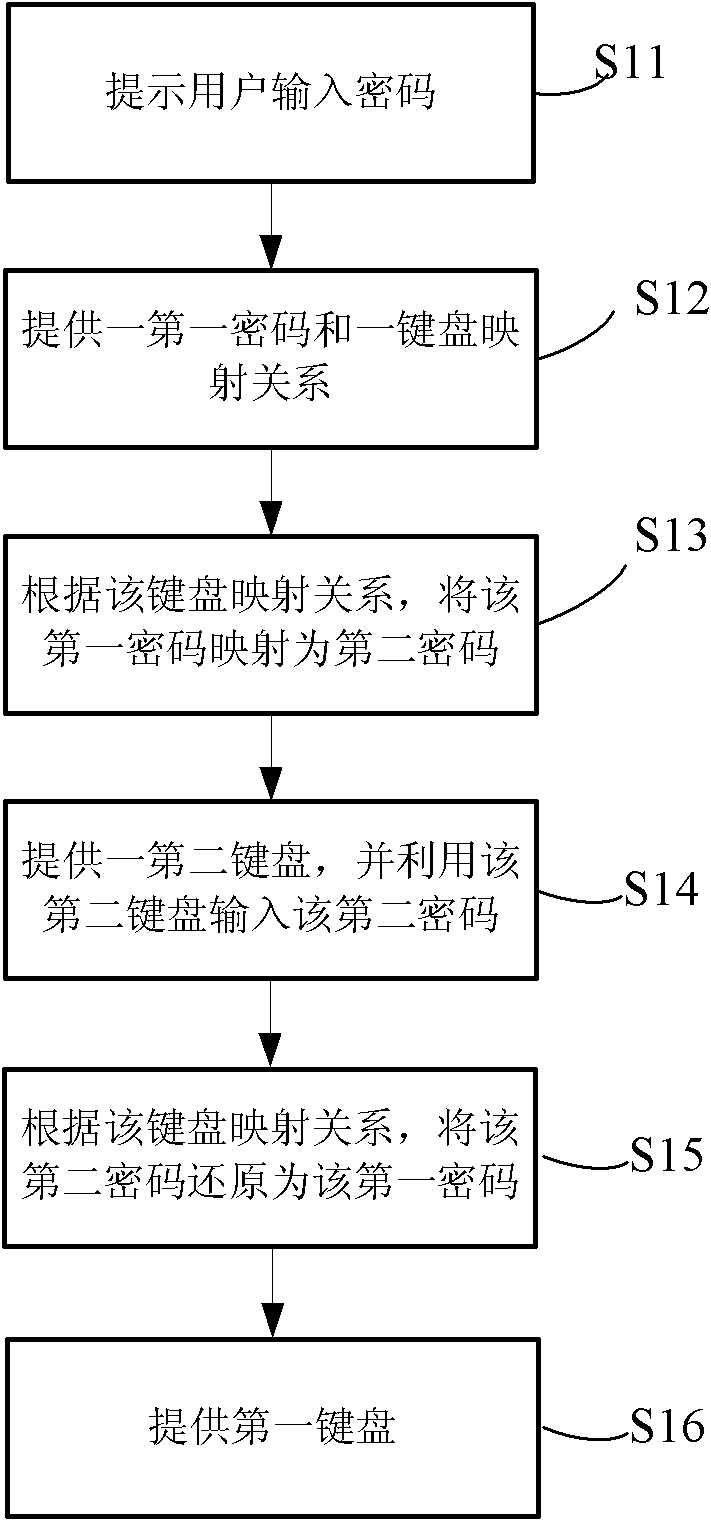
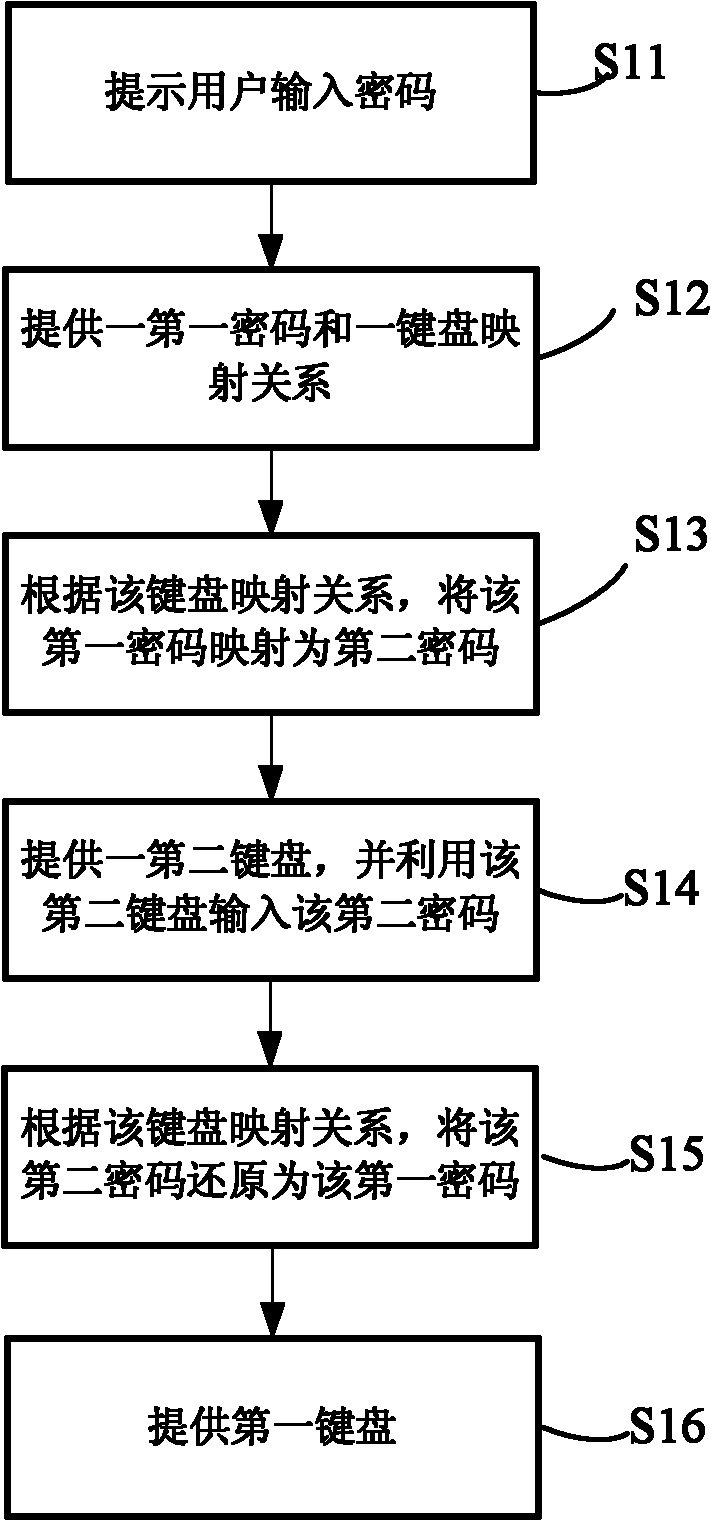
[0022] The invention provides a mobile terminal, which can be various electronic devices such as a mobile phone or a personal digital assistant (PDA).
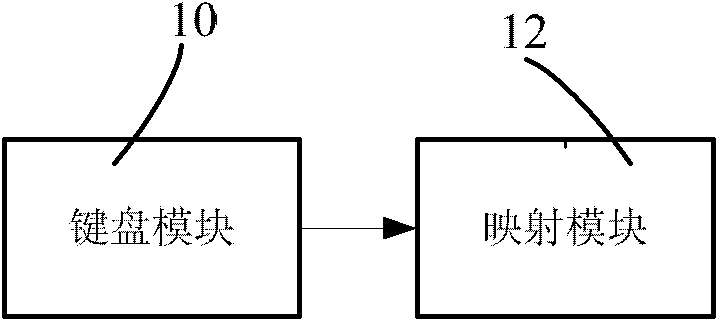
[0023] see figure 1 , figure 1 According to a schematic diagram of some functional modules of a mobile terminal according to an embodiment of the present invention, the mobile terminal includes a keyboard module and a mapping module. The main function of the keyboard module is to provide a first keyboard and a second keyboard, and the first keyboard and the second keyboard can be virtual keyboards or physical keyboards.
[0024] The key layout of the first keyboard may be a common mobile phone keyboard layout. For example, the first keyboard includes three rows of number keys, wherein the number keys in the first row are 1, 2, 3, the number keys in the second row are 4, 5, 6, and the number keys in the third row are 7, 8, 9. The first keyboard corresponds to a first password, wherein the first password is the real password ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com