Method, device and system for configuring access device
A technology for accessing equipment and equipment, applied in the field of communication, can solve the problem of consuming user energy and time, and achieve the effect of reducing burden and requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
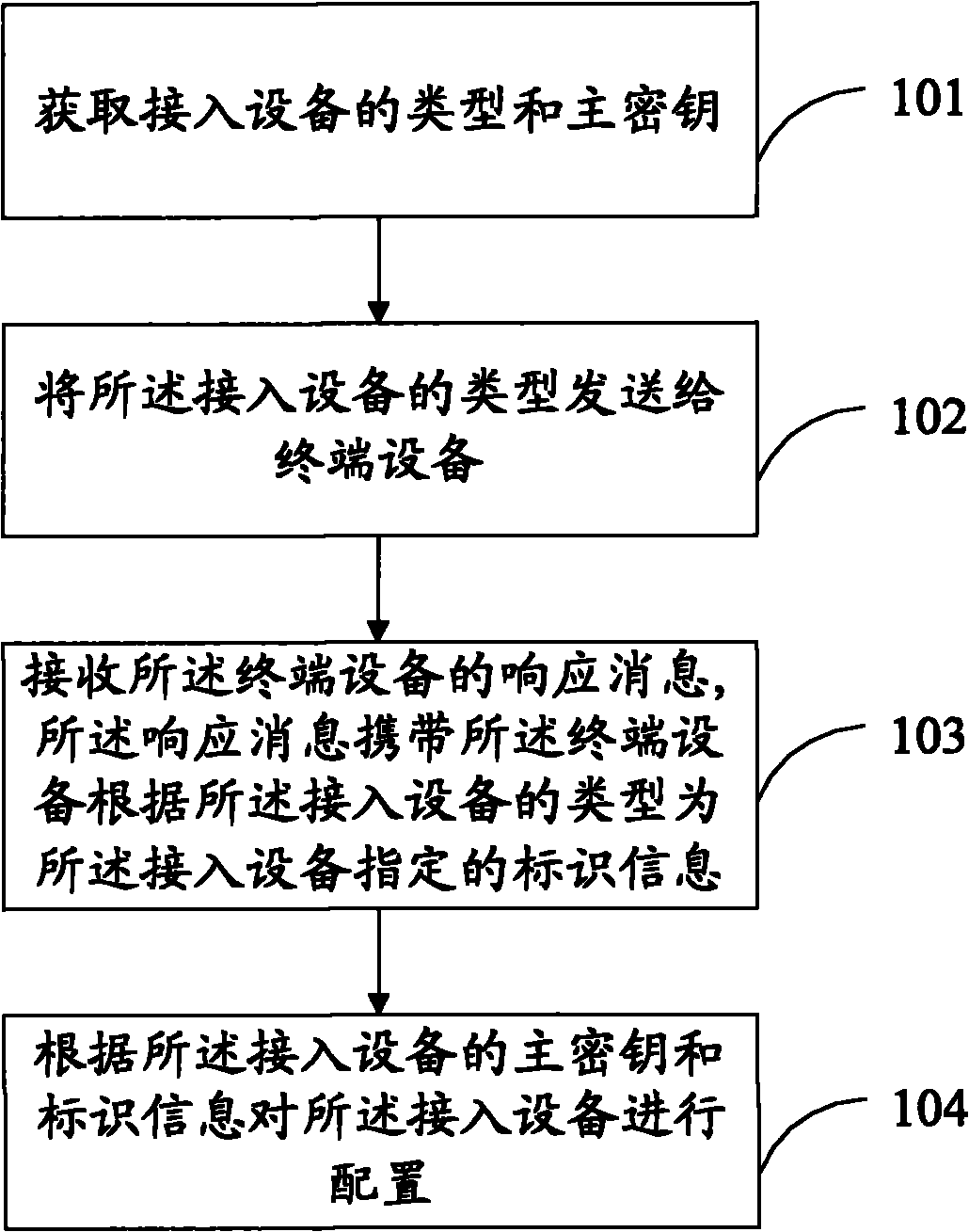
[0042] A gateway device configuration access device method, please refer to figure 1 , mainly including the following steps:
[0043] 101. The gateway device acquires the type and master key of the access device.
[0044]The gateway device sends a topology detection message to the access device, and the access device responds with the first information message after receiving the topology detection message, and reports the type of the access device and empty configuration information to the gateway device, and the gateway device receives After the empty configuration information, an authentication request is sent to the access device. After the authentication is passed, the access device responds with a second information message and reports the master key of the access device to the gateway device. The manner of authentication may be certificate (CA, Certificate Authority) authentication. In order to improve security, the access device can use the key of the certificate to ...
Embodiment 2
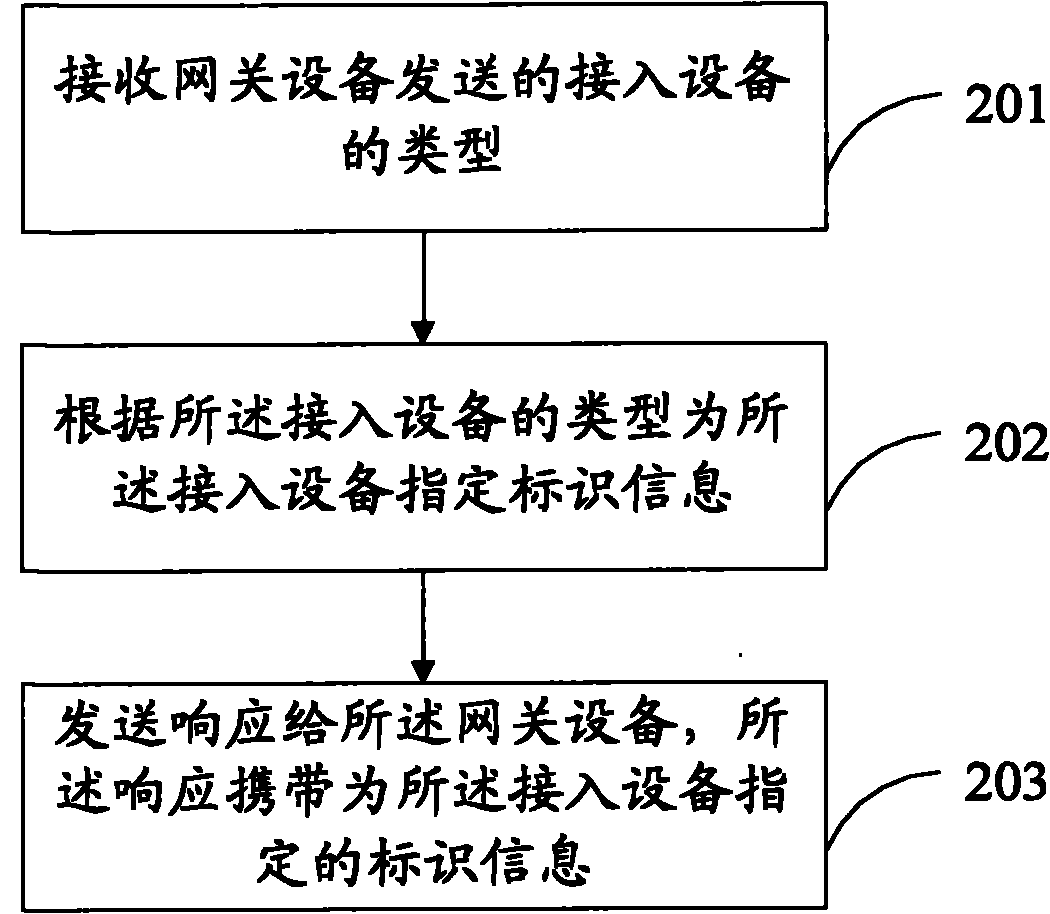
[0054] A method for terminal equipment to configure access equipment, please refer to figure 2 , mainly including the following steps:
[0055] 201. The terminal device receives the type of the access device sent by the gateway device.
[0056] The terminal device may be connected to the gateway device through Ethernet or other established secure channels, such as a Secure Shell (SSH, Secure Shell) channel, and receive the type of the access device sent by the gateway device.
[0057] 202. Specify identification information for the access device according to the type of the access device.
[0058] The terminal device may use a pre-configured program to automatically assign identification information to the access device according to the type of the access device, or the user may assign identification information to the access device according to the type of the access device. When the identification information is specified by the user, it includes the following steps: the ...
Embodiment 3
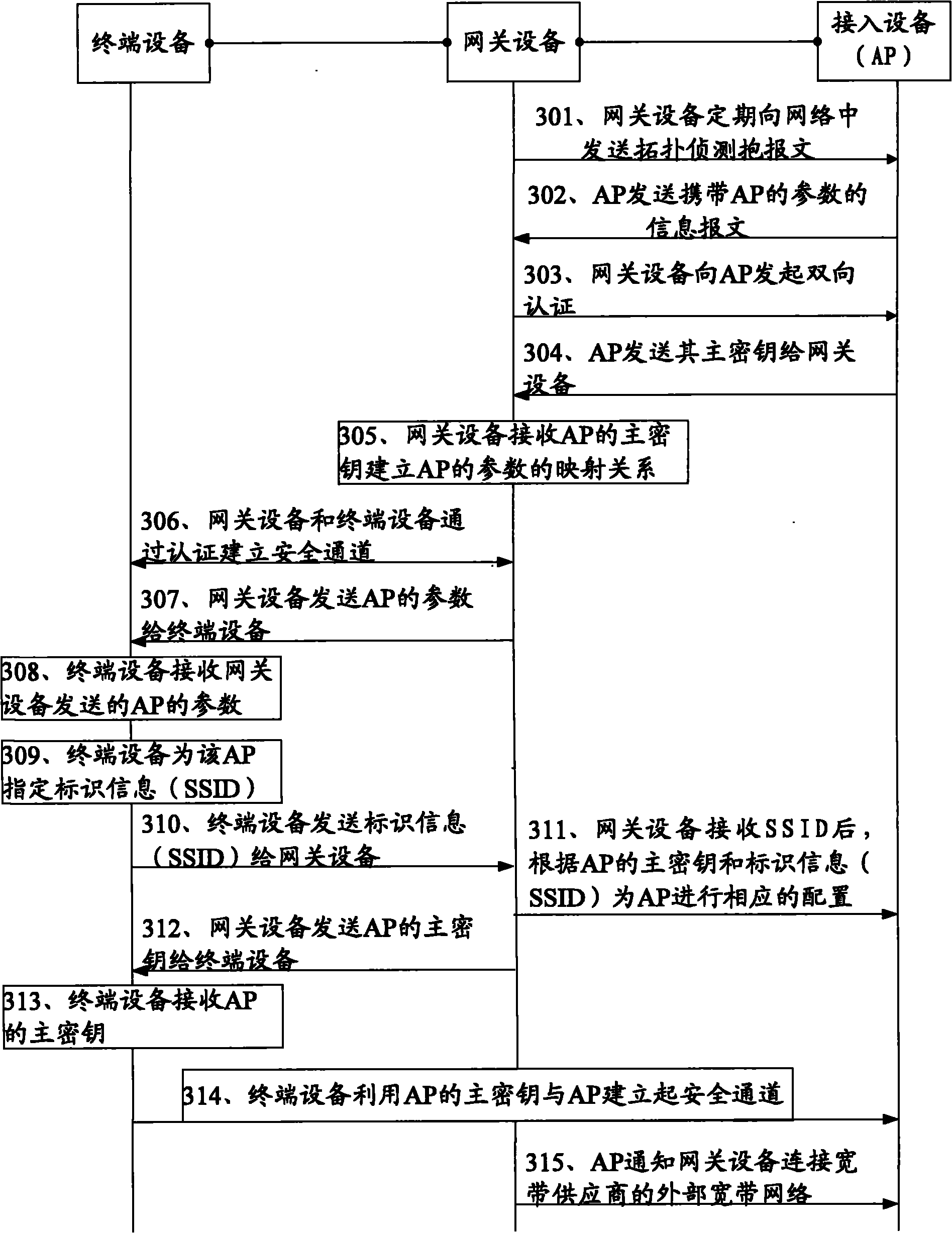
[0070] According to the methods described in Embodiment 1 and Embodiment 2, the method for configuring an access device is described in more detail in this embodiment. Please refer to image 3 with Figure 7 .
[0071] In this embodiment, the method for configuring an access device is applied in the following application scenarios:
[0072] Broadband operators provide users with broadband access services, install home gateway equipment, and the home networks established by users themselves are connected to the broadband network through the gateway equipment. In order to access and use the network more conveniently, the user has purchased an access device AP to set up a wireless network. In this embodiment, the terminal device used by the user is described by taking a personal computer as an example, and of course it may also be a terminal device such as a set-top box; the access device is described by taking an AP as an example. Of course, this embodiment is also applicabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com