Covert communication method based on IPID (Internet Protocol Identification) bit delta modulation
A communication method and delta modulation technology, applied in digital transmission systems, error prevention, electrical components, etc., can solve problems such as poor robustness in network emergencies, and achieve the effects of improving concealment, ensuring types, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
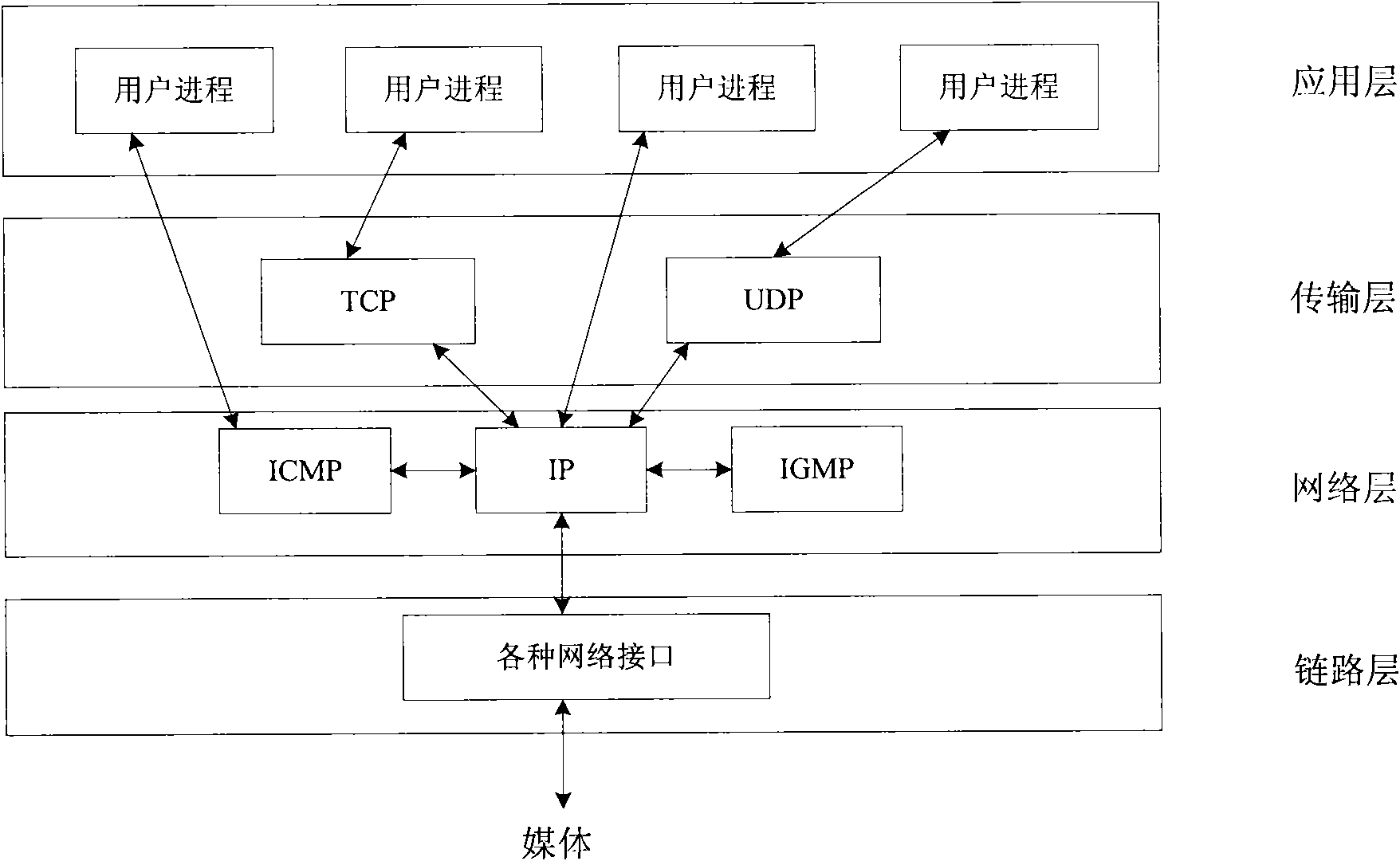
[0036] The present invention is independent of platform, is applicable to operating systems such as windows, Linux, and the carrier of covert communication is the ID bit of IP packet, so the present invention is applicable to all communication protocols based on IP agreement, below with the present invention in windows The implementation below is taken as an example for illustration. NDIS is a network driver interface specification under the windows system jointly developed by Microsoft and 3COM. The purpose of NDIS is to develop a standard API interface for the network card. Using these APIs, you can develop related windows-based system programs. This type of program can realize functions such as windows-based network data interception, modification, and release.
[0037] The invention utilizes NDIS technology to develop a program based on windows. This program can block the normal data flow, according to the sending step 3, embed the connection information into the IPID bit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com