Encryption and decryption method and device for a cloud computing key
A cloud computing and key technology, applied to key distribution, can solve problems such as poor user experience, consumption of system resources, and increased service response delay, achieving the effects of convenient management, ensuring security, and reducing service response delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
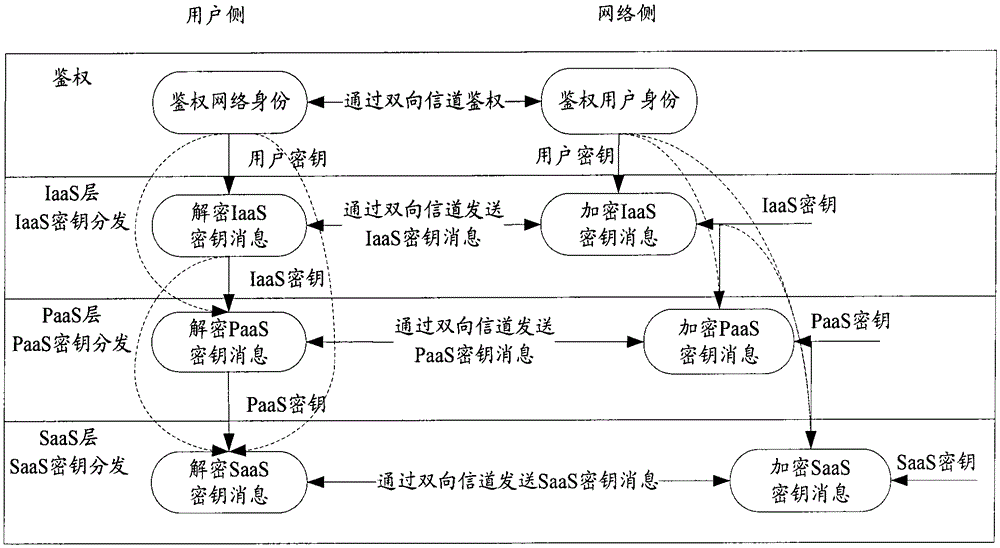
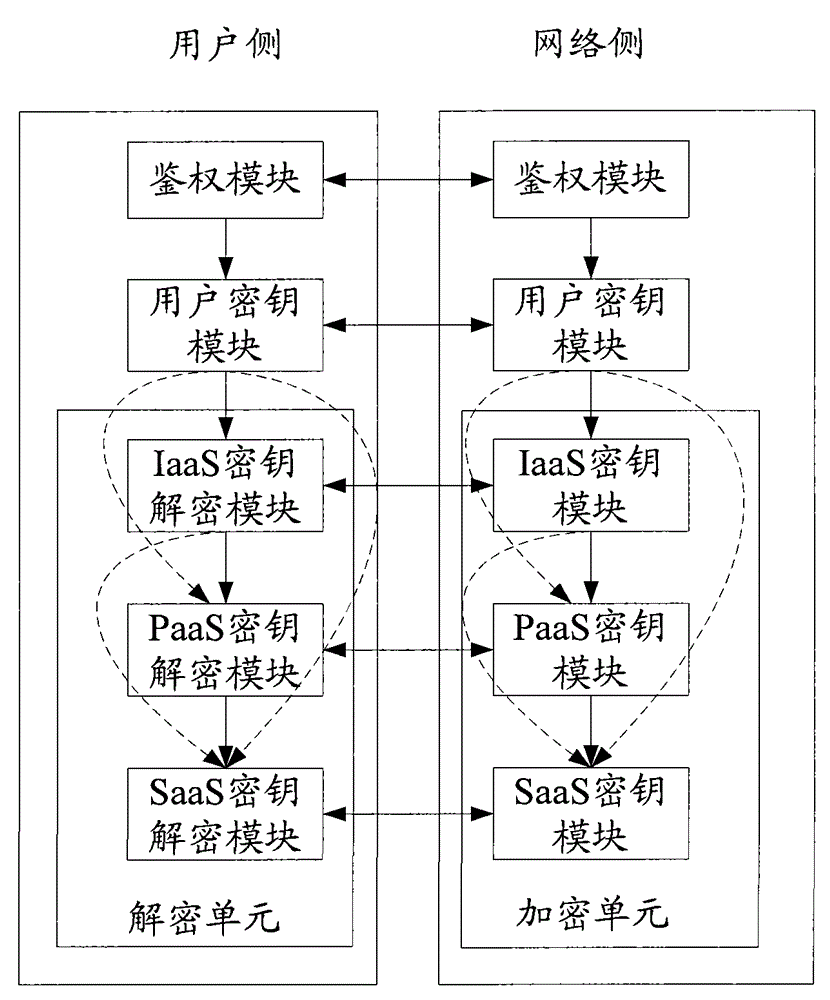
[0033] The basic idea of the present invention is: in the cloud computing service, a key with a longer life cycle is used to encrypt a key message with a shorter life cycle, so as to improve the security of key distribution.
[0034] The scheme of the present invention will be described in detail below by taking all three services provided by cloud computing, ie, IaaS, PaaS and SaaS, as examples.
[0035]The key with a long life cycle is a relative concept. For example, in the above three services, the life cycle of the IaaS key is generally several days to several months, and the life cycle of the PaaS key is generally several hours to several day, the life cycle of a SaaS key is only a few minutes or even a few seconds to a few hours. It can be seen that the life cycle of an IaaS key is longer than that of the other two, while the life cycle of a PaaS key is longer than that of a SaaS key; the life cycle Shorter keys are also a relative concept. For example, the life cycle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com