A secure data transfer method and system
A technology for securing data and data packets, applied in security devices, electrical components, wireless communications, etc., to overcome authentication failures and improve security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
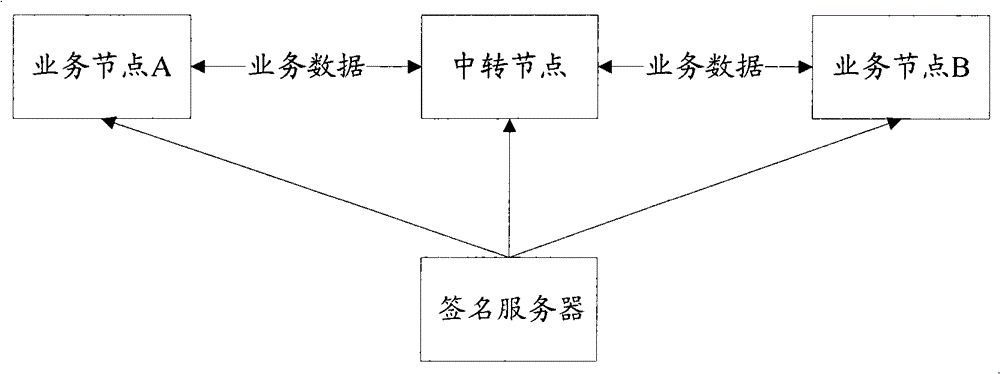
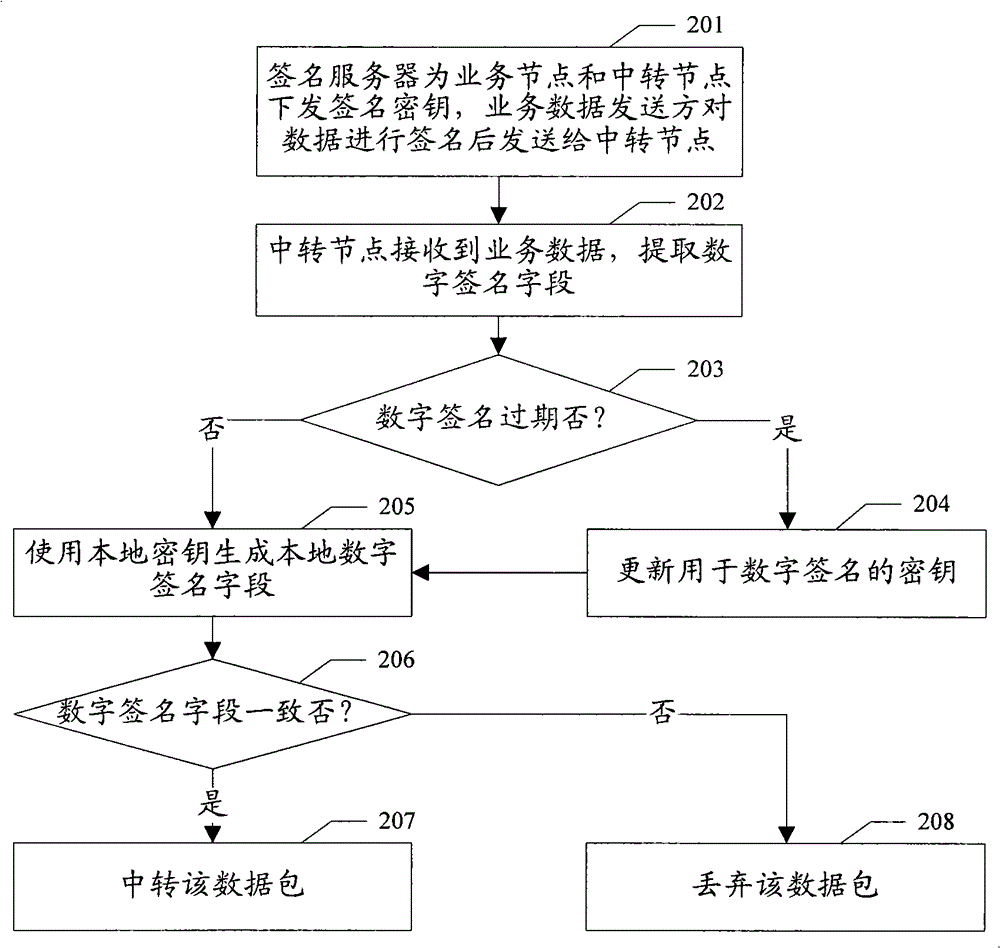
[0027] The basic idea of the present invention is: through the signature server, distribute time-sensitive digital signatures to the business data sender, business data transfer node, and business data receiver, the sender of the data digitally signs the data packet, and the party receiving the data passes the digital signature Signature to verify that the sender of the data packet is legitimate. The transfer node of business data authenticates the sender of business data through digital signature, and refuses to transfer the business data if the authentication fails; the receiver of business data authenticates the transfer node of business data through digital signature, and refuses to receive the transfer node if the authentication fails Transferred business data. The invention enhances the security of the transfer data through the data signature technology, ensures that the transfer node only transfers legal data, and the data receiver only receives legal data.
[0028] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com