A method and system for realizing identity management interoperability
A technology of identity management and interoperability, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve problems such as practical application inconvenience, and achieve the effect of convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
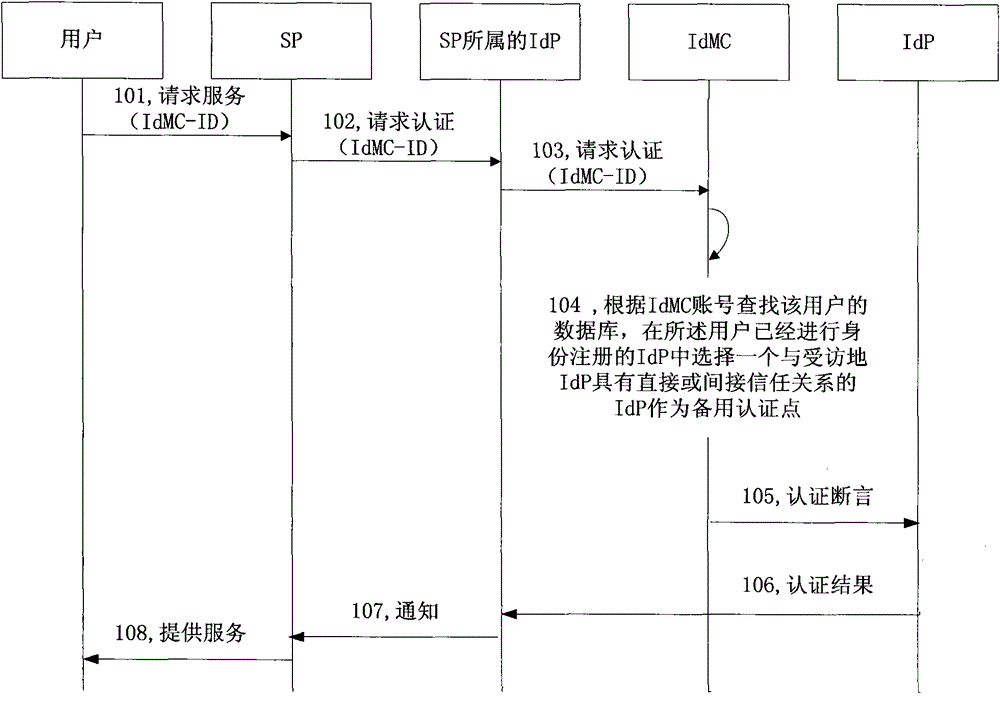
[0053] In Embodiment 1, the identity provider maintained by the identity management center establishes a direct connection trust path with other identity providers as needed; when the identity management center selects a backup authentication point, it will An identity provider that has a direct trust relationship or an indirect trust relationship with the identity provider to which the service provider belongs is selected as a backup authentication point among the identity providers for which the user has performed identity registration.
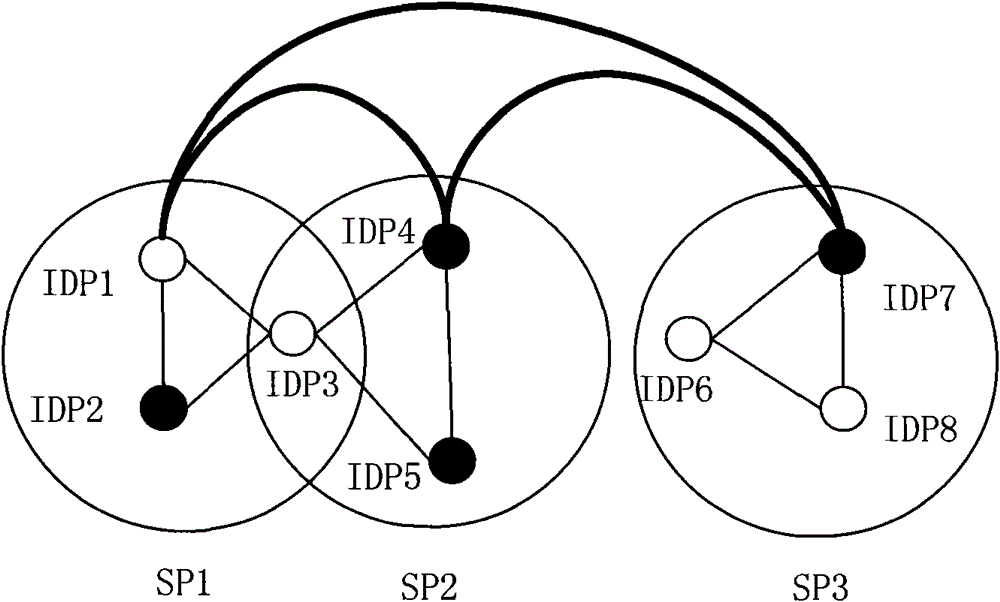
[0054] Among them, two identity providers have a direct trust relationship means that they belong to the same trust domain, or both do not belong to the same trust domain but they have a direct trust path; two identity providers have an indirect trust relationship means they belong to different Both of the trust domains can establish indirect trust paths through the intersection of trust domains between identity providers and / or direct trust...
Embodiment 2
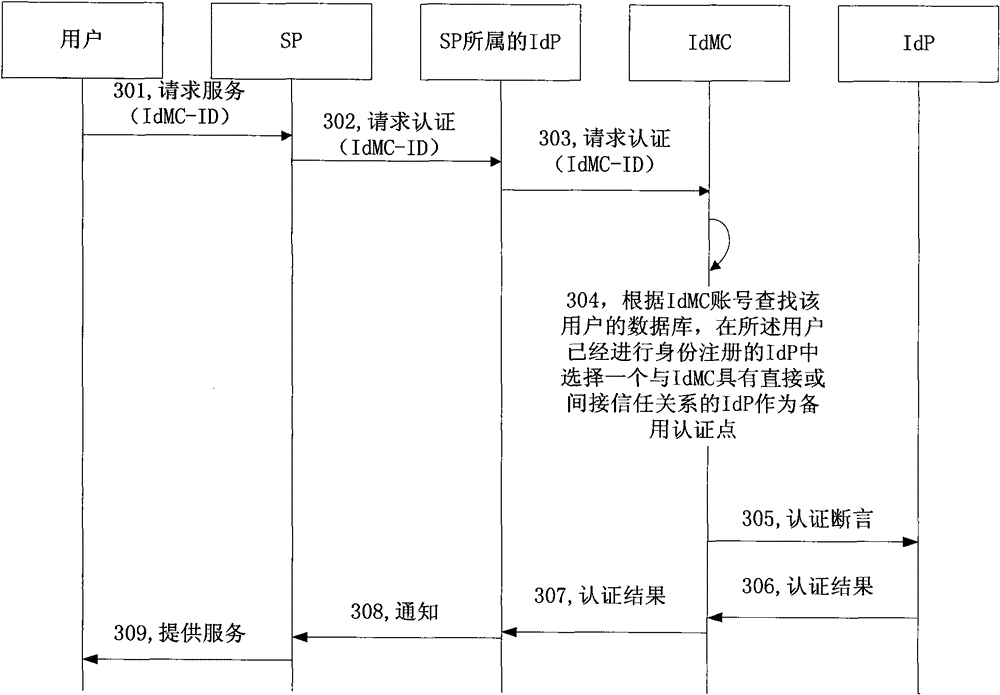
[0083] In Embodiment 2, the identity provider maintained by the identity management center establishes a direct trust path with the identity management center as required, and the identity provider to which the service provider belongs has a direct trust path with the identity management center; When the identity management center selects a backup authentication point, according to the direct trust path between each identity provider and the identity management center, select one of the identity providers for which the user has registered has a direct relationship with the identity management center. Or an identity provider in an indirect trust relationship as an alternate authentication point.
[0084] The direct trust relationship between the identity provider and the identity management center means that the two have a direct trust path; any two identity providers in the same trust domain have a direct trust path, and the identity provider and the identity management center ...
Embodiment 3
[0106] Embodiment 2 combines the application conditions of Embodiment 1 and Embodiment 2. The identity provider maintained by the identity management center establishes a direct connection trust path with other identity providers as required, and establishes a direct connection trust path with the identity management center as required; when the identity management center selects a backup authentication point, according to The direct connection trust path between each identity provider and the direct connection trust path between each identity provider and the identity management center selects one of the identity providers that the user has registered with the identity that the service provider belongs to The identity provider with which the provider has a direct or indirect trust relationship acts as a backup authentication point. Two identity providers have a direct trust relationship means that they belong to the same trust domain, or they do not belong to the same trust d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com