Method and system for killing mobile terminal viruses
A mobile terminal and virus technology, applied in instruments, computing, electronic digital data processing, etc., can solve problems such as leakage of personal information, user mobile phone data security issues, and missing viruses, so as to protect data security, improve antivirus capabilities, and repair damage effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
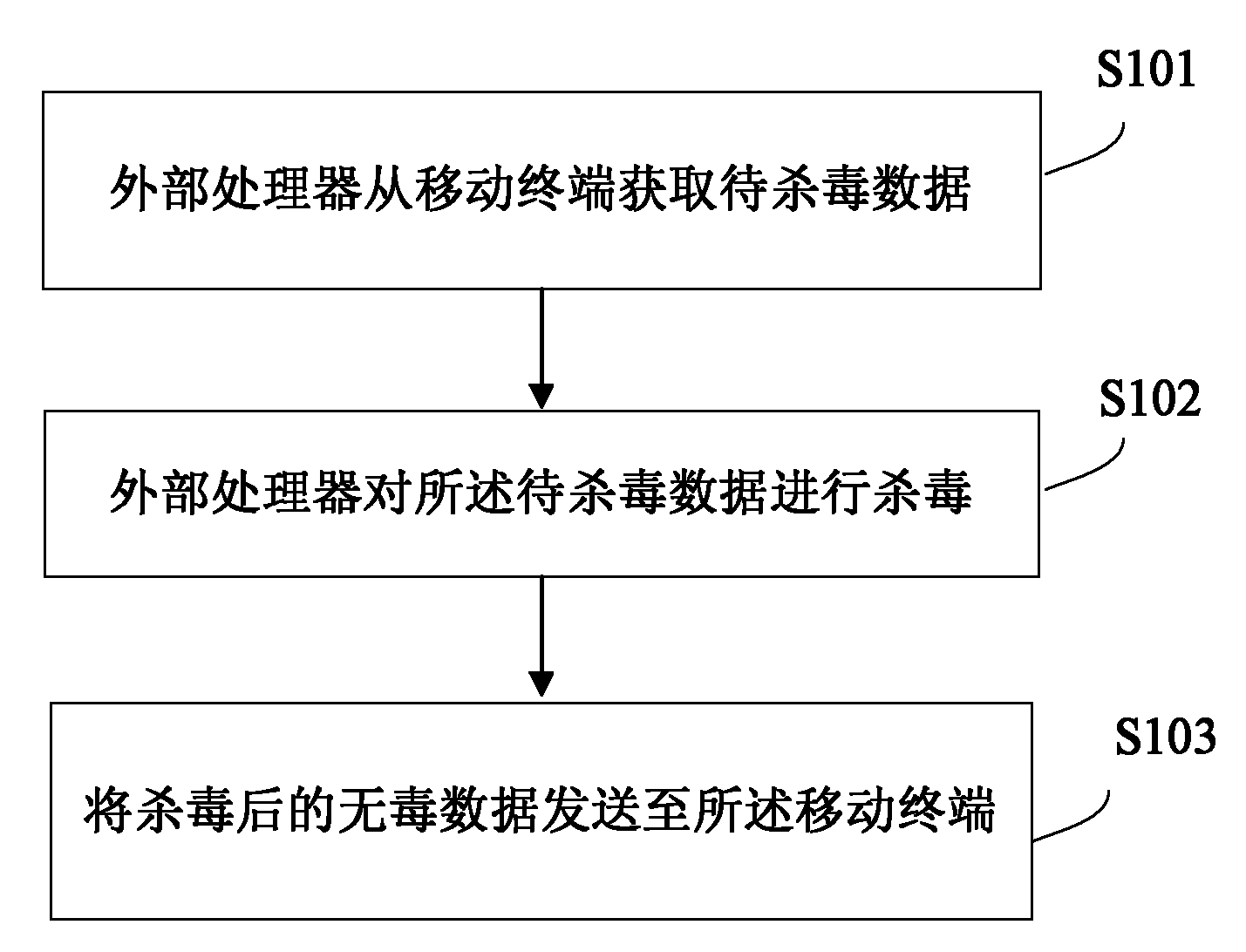
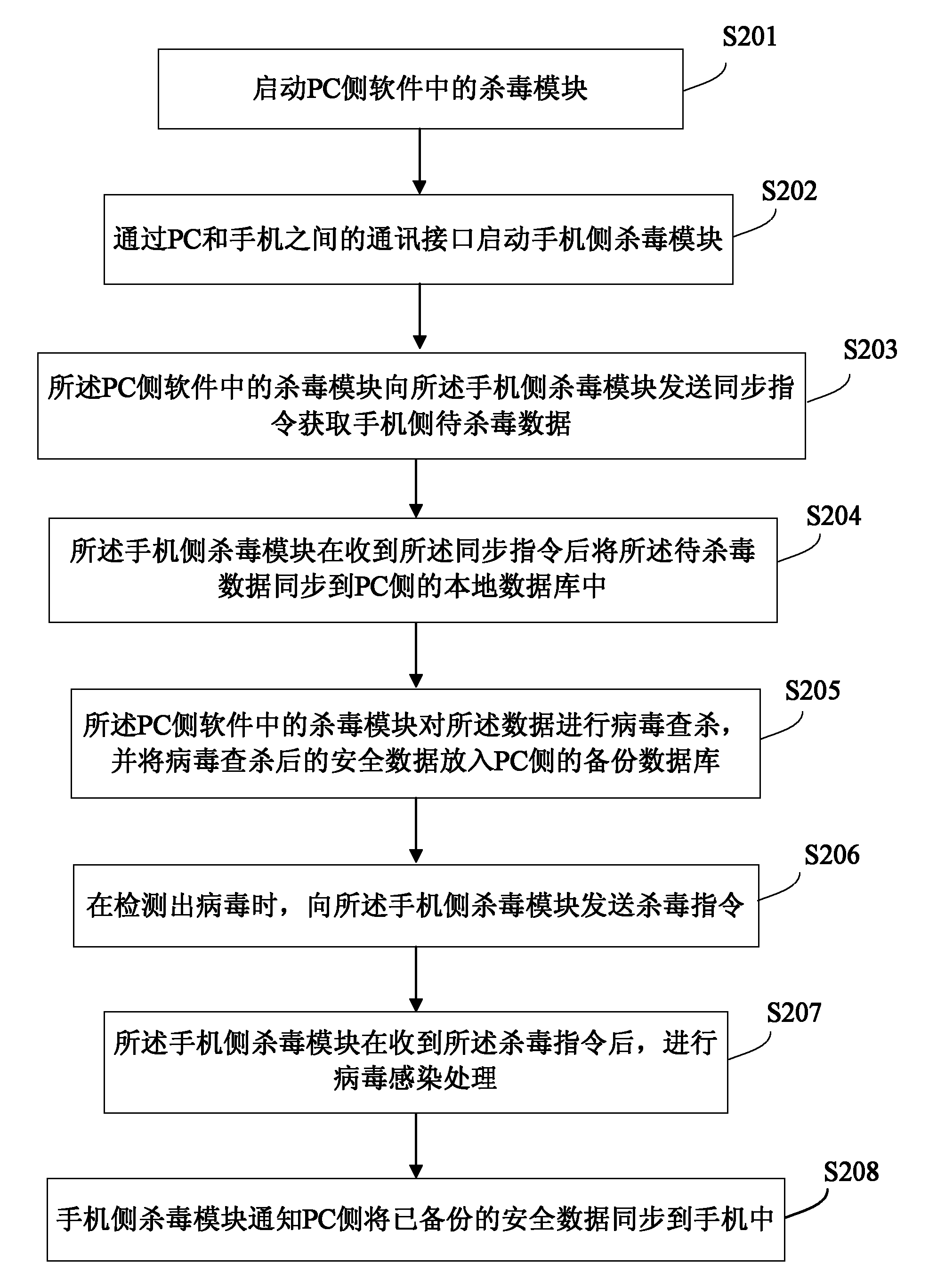
[0054] Such as image 3 As shown, the external processor is an example of a PC, and the mobile terminal is an example of a mobile phone. This embodiment provides a method for checking and killing viruses on a mobile phone using the supporting PC side software of the mobile phone, including the following steps:
[0055] S201: Start the antivirus module in the PC side software;
[0056] The initialization operation is performed when starting the antivirus module in the PC side software, including updating the virus library of the antivirus module in real time, starting the virus scanning engine and the virtual machine, and the virus library of the antivirus module includes a virus signature library and a dangerous behavior pattern library.
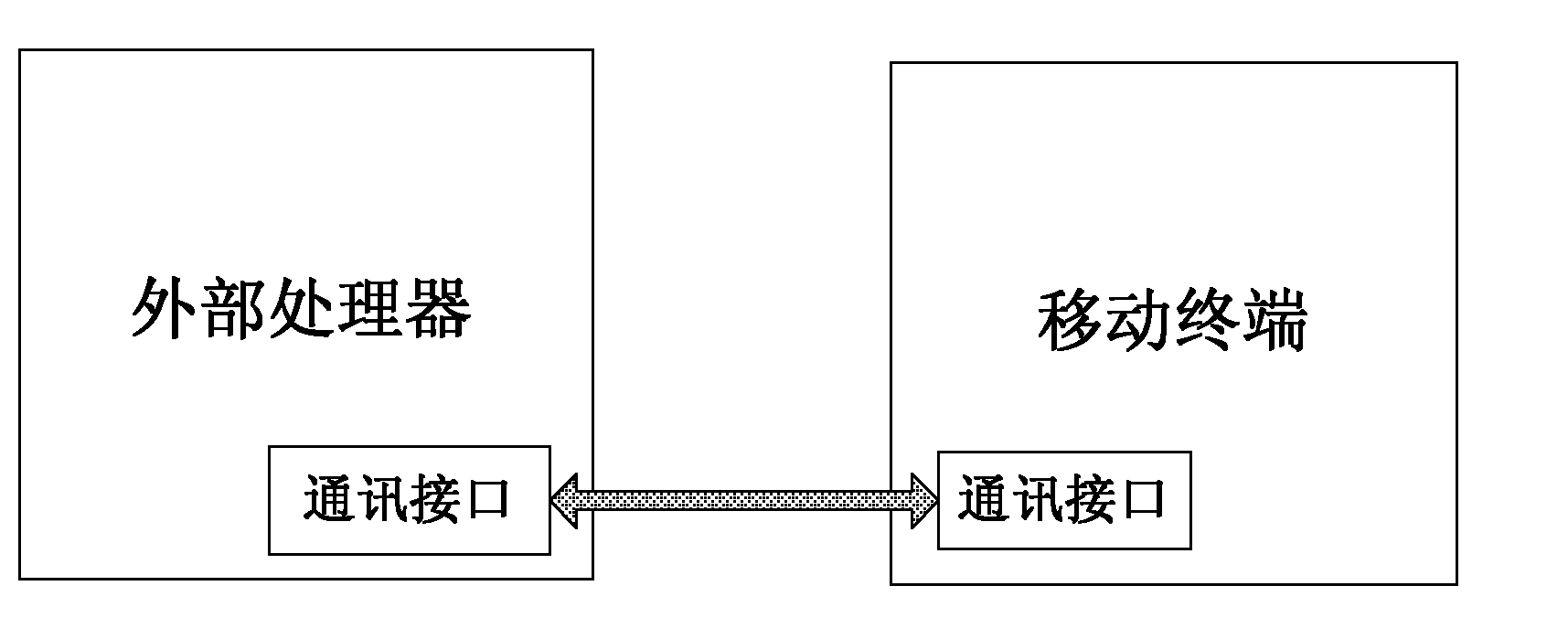
[0057] S202: Start the mobile phone side antivirus module through the communication interface between the PC and the mobile phone;
[0058] After the antivirus module on the mobile phone side is started, it is in a monitoring state, waiting f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com