Dynamic encryption and decryption methods and equipment for network communication
A network communication and dynamic encryption technology, applied in the field of computer networks, to achieve high protection strength and security level, easy to implement, and achieve the effect of key agility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The method and apparatus according to the invention will now be described in detail through several exemplary embodiments with reference to the accompanying drawings, by way of example only. It should be understood that the illustrated and described embodiments are only exemplary, which are intended to explain the principle and spirit of the present invention, but not to limit the scope of the present invention.
[0025] In the following description, for the sake of clarity, the term "first network entity" is used to indicate the party that initiates key synchronization and sends data, and the term "second network entity" is used to indicate the party that accepts key synchronization and receives data. It should be understood that the first network entity and the second network entity may be any network entities capable of data transmission.
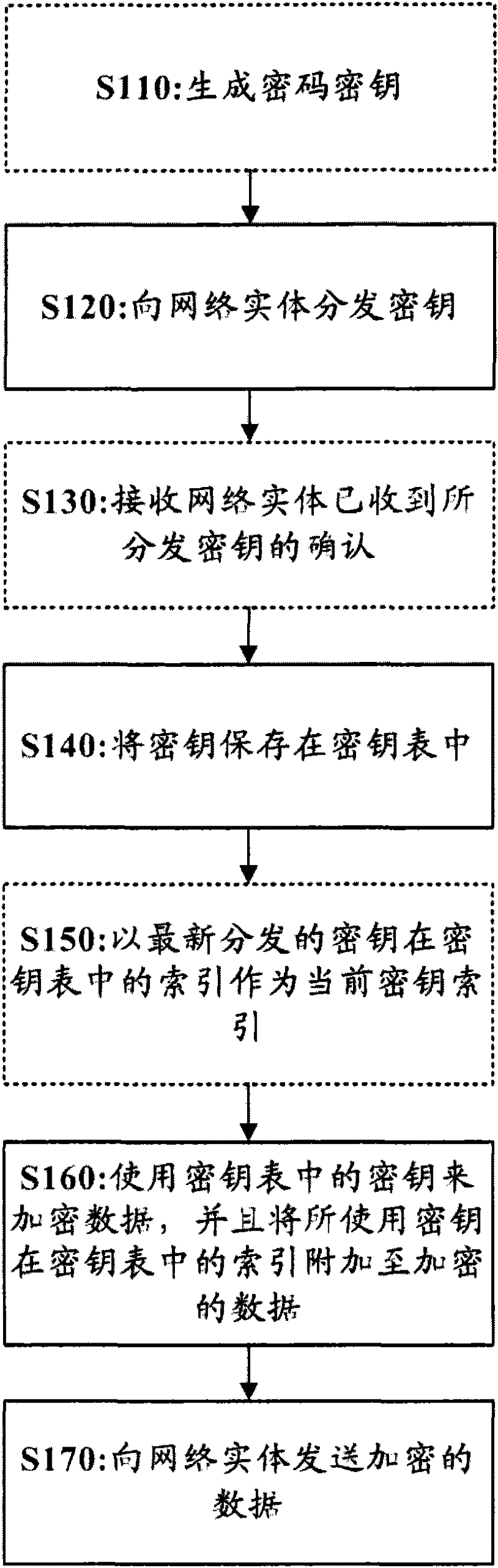
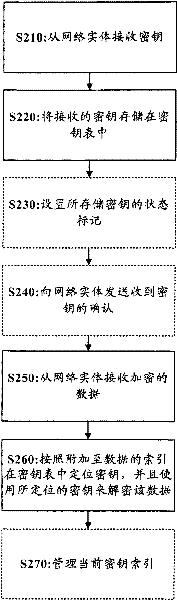
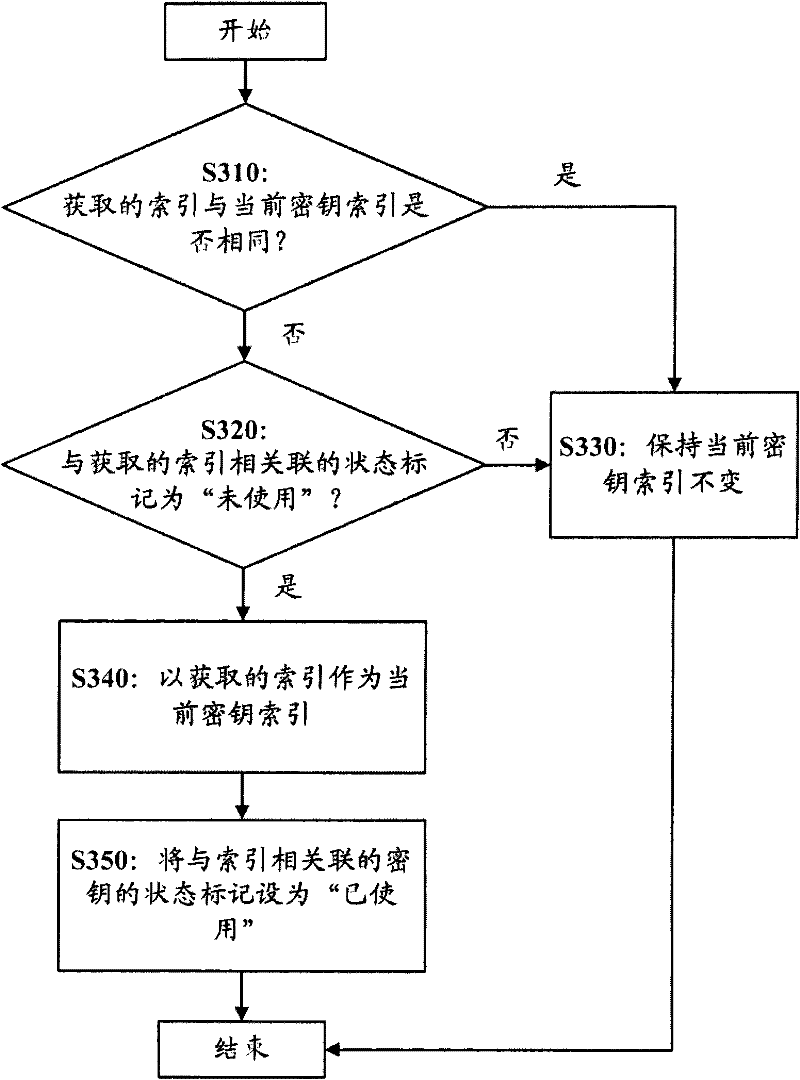
[0026] figure 1 A flowchart showing a dynamic encryption method for network communication according to an embodiment of the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com