Encryption and decryption method and encryption and decryption device of multi-data security module
A security module and data security technology, applied in the field of information security, can solve the problems of low security, limited application of RFID technology, poor security of passive RFID cards, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
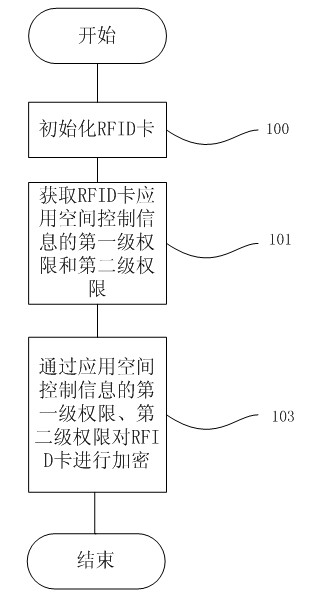
[0034] The flow chart of the encryption method of the multi-data security module of a preferred embodiment of the present invention can be found in figure 1 , including the following steps,
[0035] Step 101: Initialize the RFID (Radio Frequency Identification, radio frequency identification) card, including, check the key index number of the RFID card, query the access key of the RFID card,
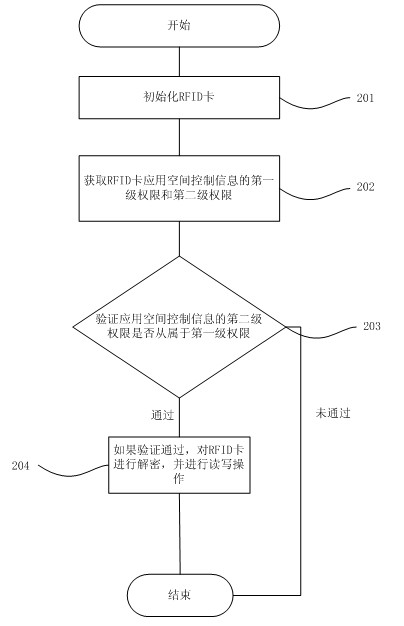
[0036] Step 102: Obtain the first-level authority and the second-level authority of the RFID card application space control information, including, after multiple encryption checks, obtain the first-level authority of the RFID card application space control information, and also include the RFID card application space control The second-level authority of the information assigns the read-write authority of each bit of the RFID card application space.
[0037] Step 103: Encrypt the RFID card by using the first-level authority and the second-level authority of the space control informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com