A Software Identification Method Based on Data Stream Slicing
A data flow and slicing technology, applied in the computer field, can solve problems such as the reduction of dynamic K-gram robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
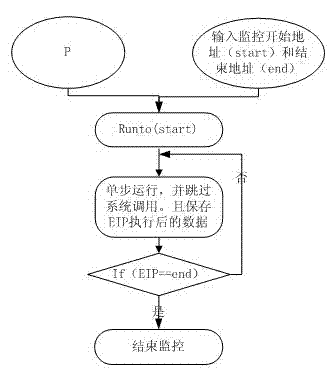
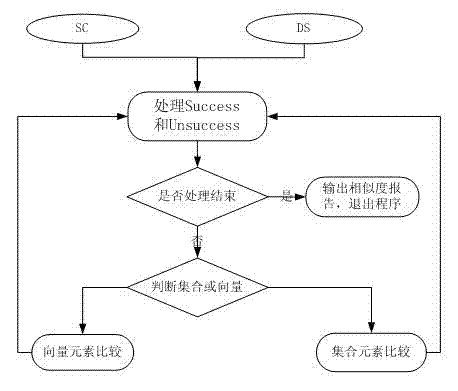
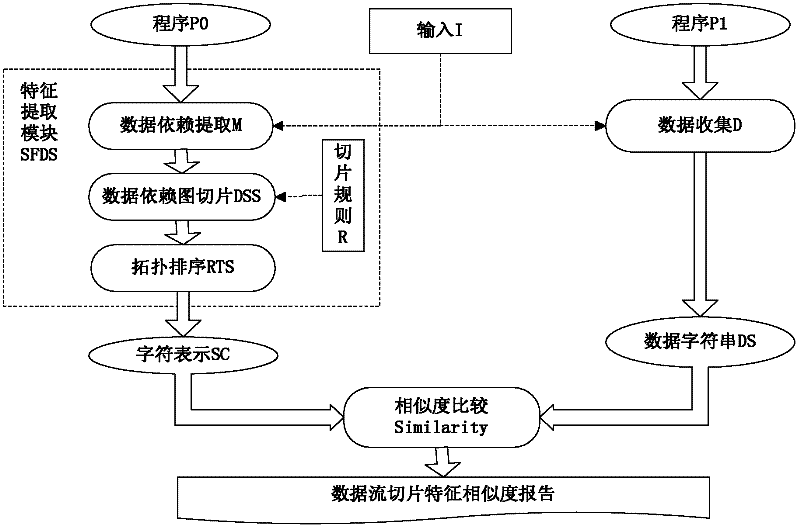
[0054] The invention is a software identification method based on data flow slicing, which mainly uses a computer system to provide support for software identification and virus detection. A computer system model such as figure 1 As shown, it specifically includes the following modules:
[0055] The data dependency extraction module is used to extract the data flow and its dependencies of the original software itself, and express the extracted data flow with a data dependency graph;
[0056] The data flow described in this application is a data sequence formed by new data generated during software operation, which is different from the concept of data flow in software engineering. The specific definition is as follows:
[0057] Data Stream (Data Stream referred to as DS): When the software P inputs I, di is the new data generated by the software expression calculation, i represents the sequence of time, and a data string d1, d2...dn will be formed in turn. The data flow is d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com