Method for monitoring illegal access device and apparatus thereof
An illegal access and monitoring device technology, applied in the network field, can solve the problems of increasing the difficulty of illegal access equipment, unable to completely eliminate the phenomenon of rubbing the network, and difficult to detect in time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
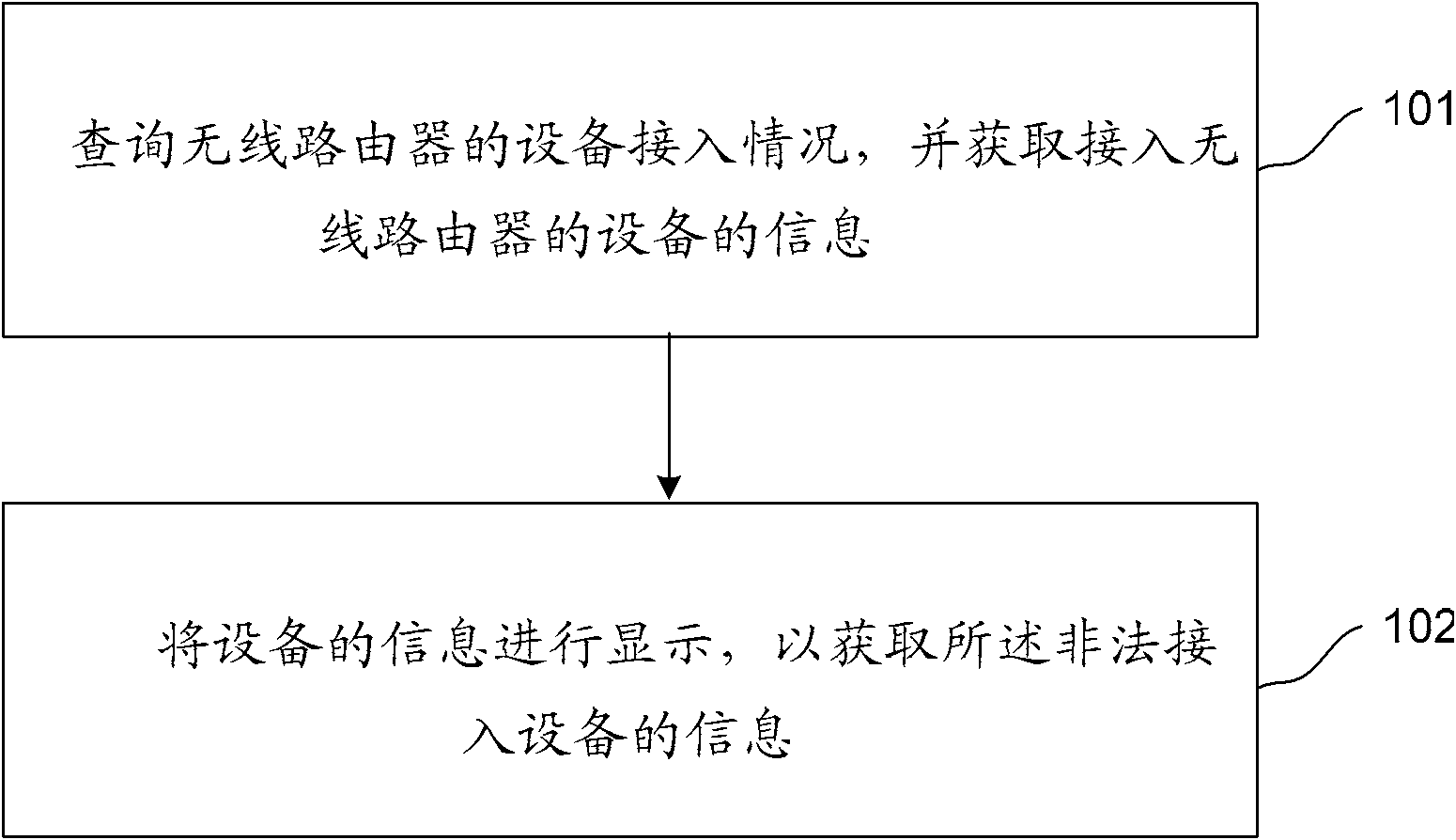
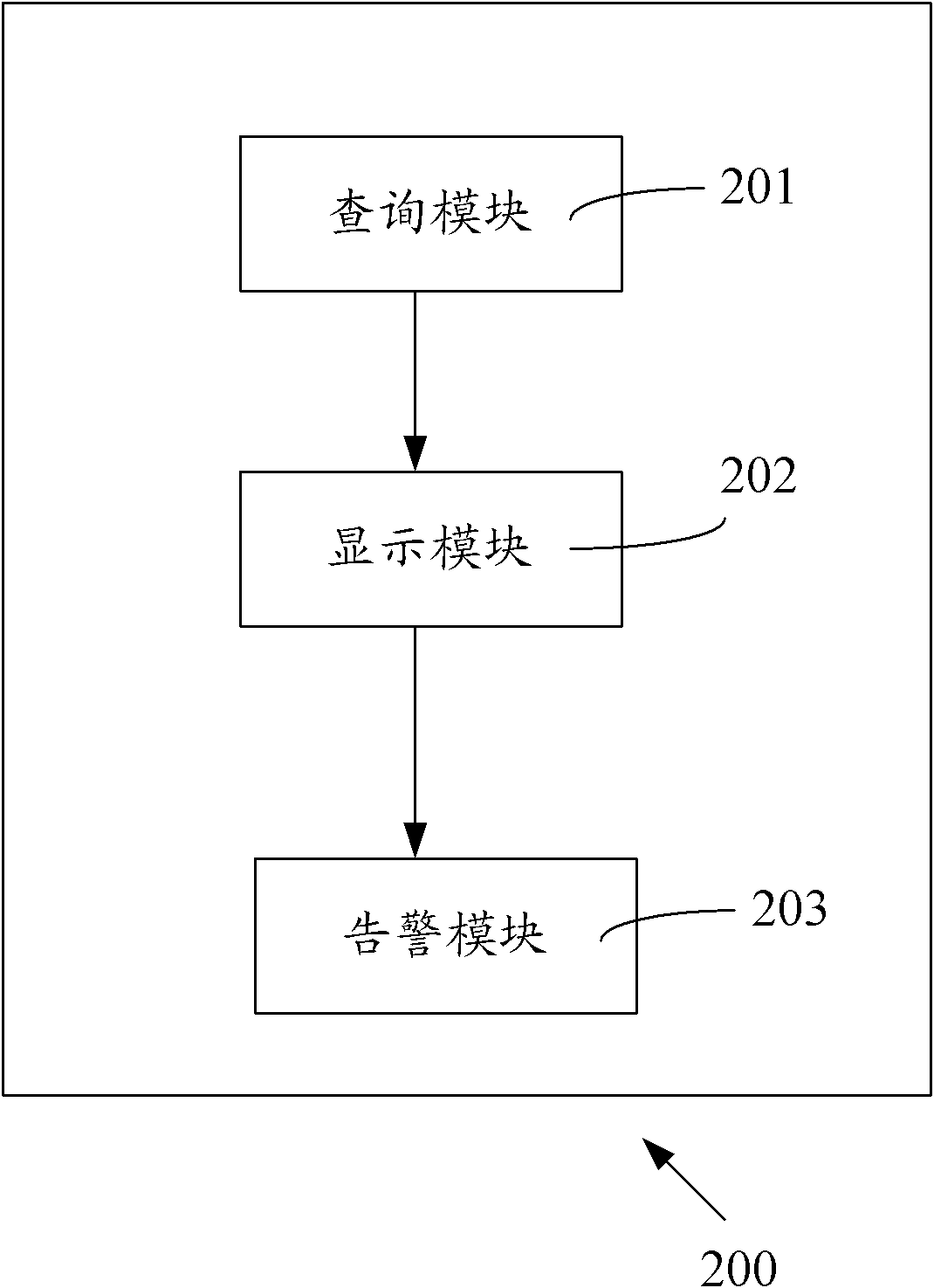
[0037] This embodiment 1 provides a method for monitoring illegal access devices, which is applicable to various system architectures that can provide wireless access network functions. For example, a current typical system architecture is to set a wireless router on the terminal side. The wireless router accesses the Internet through a cable, and the user accesses the wireless router wirelessly through a terminal device. The method of this embodiment can be implemented by the monitoring device of the illegal access device, and the monitoring device of the illegal access device can be integrated in the wireless router, that is, all or part of the steps of the method can be implemented through program instructions related to the wireless router. hardware to complete. The device for monitoring illegal access equipment can also be integrated in the terminal equipment, and can be completed through program instructions to relevant hardware in the terminal equipment. Such as figur...
Embodiment 2
[0045] The second embodiment further describes the method for monitoring illegally accessed devices in the first embodiment, wherein step 101 may include:
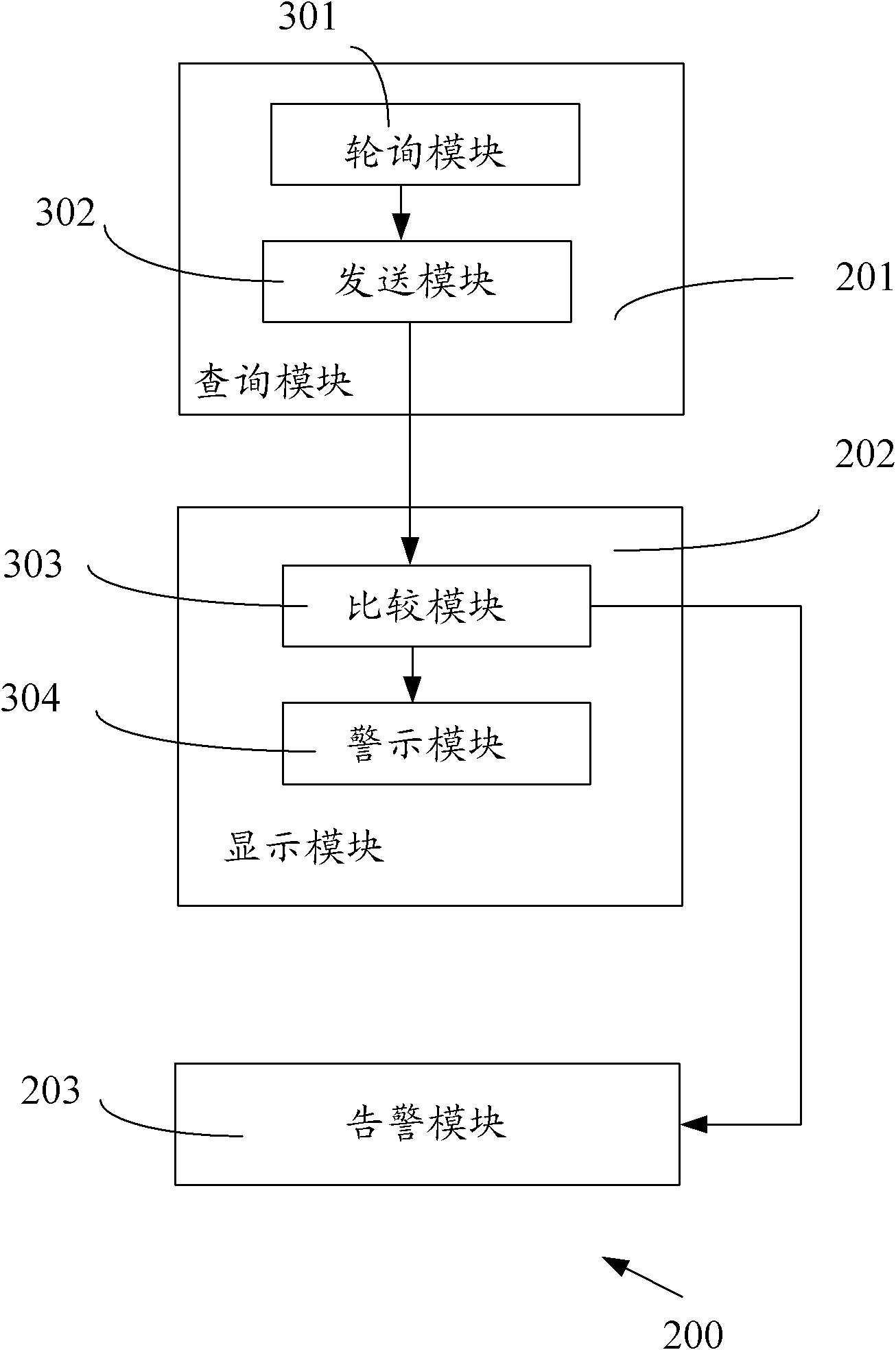
[0046]Regularly query the preset address resolution list in all devices connected to the wireless router, and obtain at least one of the device's IP address, device MAC address and device user name from the address resolution list.
[0047] Step 102 may include:
[0048] Compare the information of all devices with the preset white list. The white list includes the information of the devices that are allowed to access; form to display information about the device.
[0049] Blacklist and whitelist can be set in advance, and the blacklist includes the information of devices that are prohibited from accessing. When a device in the blacklist tries to access the wireless router, the monitoring device for the illegal access device can automatically prevent the access of the illegal device. In this way, the user does not need t...
Embodiment 3
[0054] The third embodiment further describes the monitoring method for illegal access devices in the first embodiment.
[0055] Wherein, step 101 includes:
[0056] When it is recognized that a new device is connected to the wireless router, the address resolution list preset in the new device is queried, and at least one of the IP address of the device, the MAC address of the device and the user name of the device is obtained from the address resolution list.
[0057] Step 102 includes:
[0058] Comparing the information of the new device with the preset white list, the white list includes the information of the devices that are allowed to be accessed; when the information of the new device is not recognized in the white list of the devices that are allowed to be accessed, the new device is displayed on the display module Information.
[0059] Blacklist and whitelist can be set in advance, and the blacklist includes the information of devices that are prohibited from acces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com