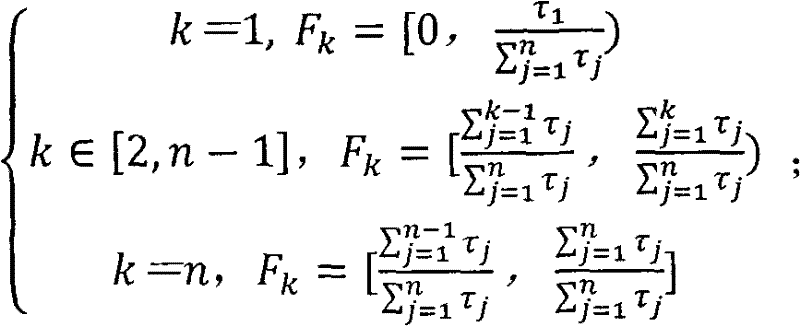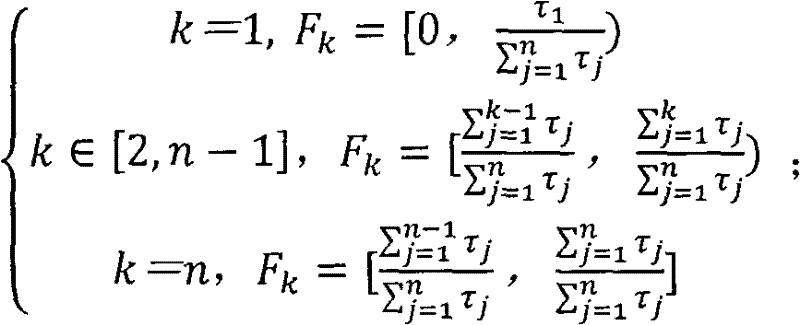Cloud-based user visit request scheduling method
A technology for access requests and user requests, applied to electrical components, transmission systems, etc., can solve problems such as rigid rules, difficulty in responding to user request loads, difficulty in adapting to server hardware performance and dynamically changing load environments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention is described in more detail below in conjunction with accompanying drawing example:
[0038] Algorithm of the present invention is characterized in that:
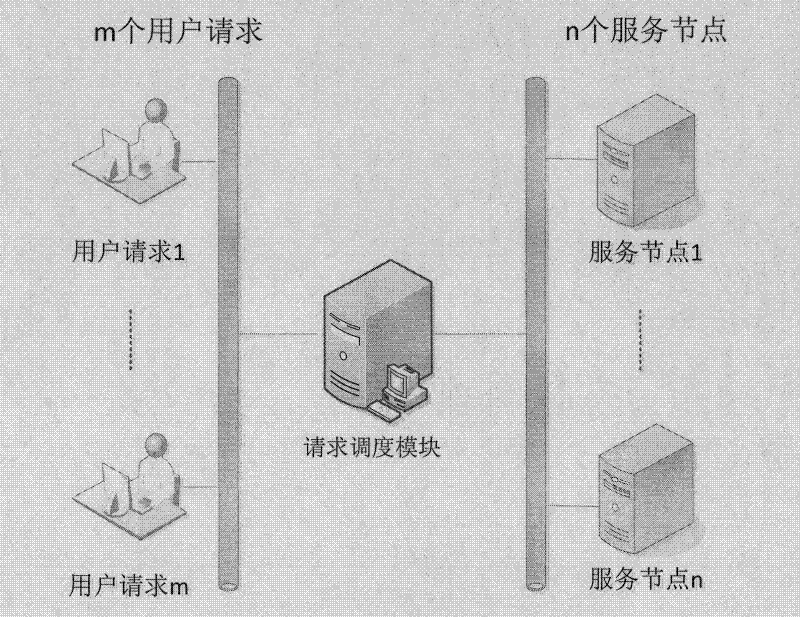
[0039] Let the pending user request queue contain m requests, denoted as R 1 , R 2 ,...,R m ; The set of service nodes in the cloud computing system contains n service nodes, denoted as S 1 , S 2 ,...,S n , the average request execution time of each service node is expressed as The lengths in the pending request queue are denoted as u 1 , u 2 ,...,u n , the weights are denoted as τ 1 , τ 2 ,...,τ n , and the load intervals are denoted as F 1 , F 2 ,...,F n , and for j≠k, The overload threshold is expressed as μ; the adjustment step size is expressed as is a positive number; the request scheduling module is mainly responsible for scheduling user access requests, while monitoring the load of each service node, and timely adjusting their weights and load intervals;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com