Operating system object reuse check method based on exhaustive search
An inspection method and object technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of inspection technology and tools without relevant reports, and achieve the goal of improving inspection speed, simplifying inspection methods, and improving accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
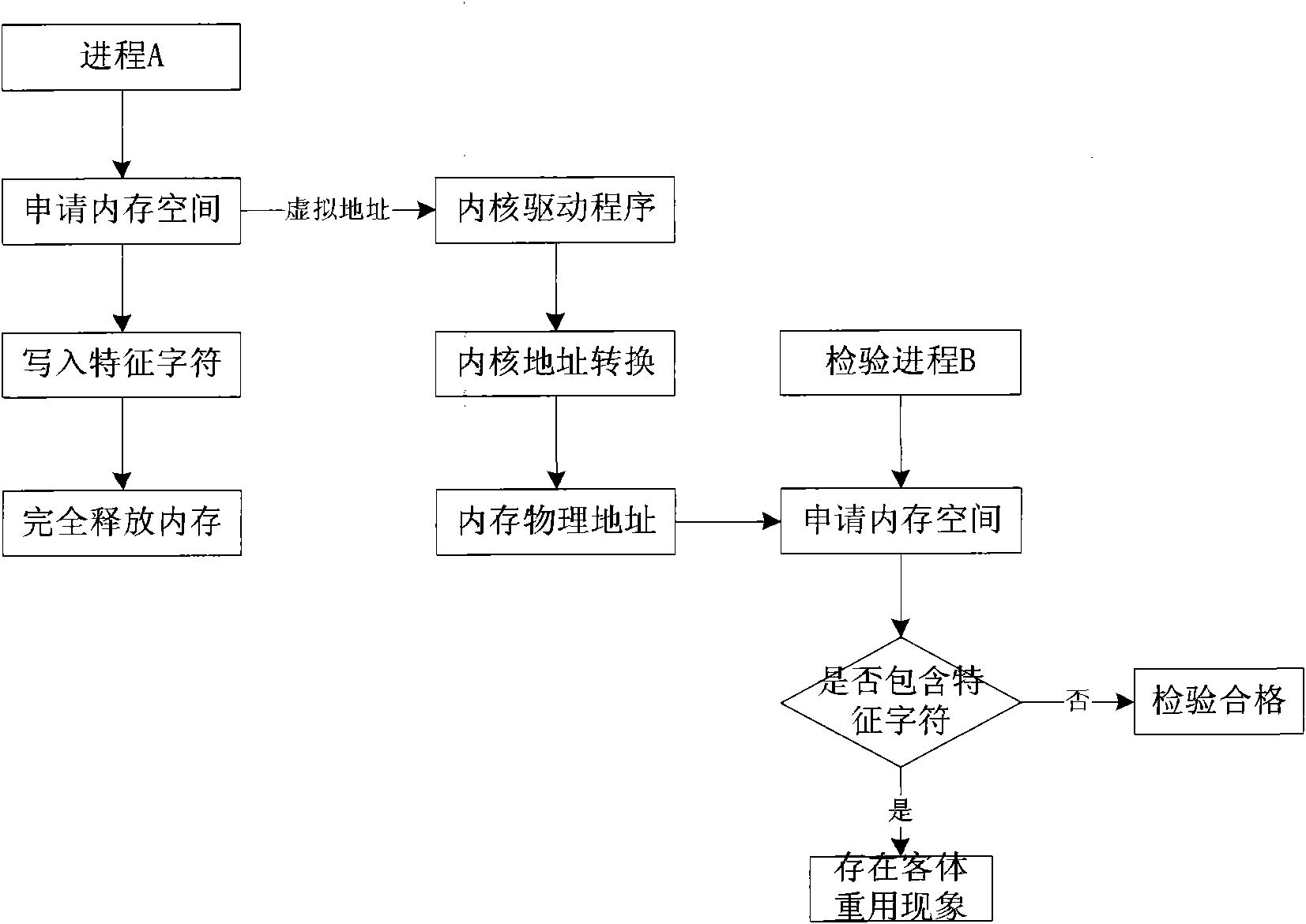
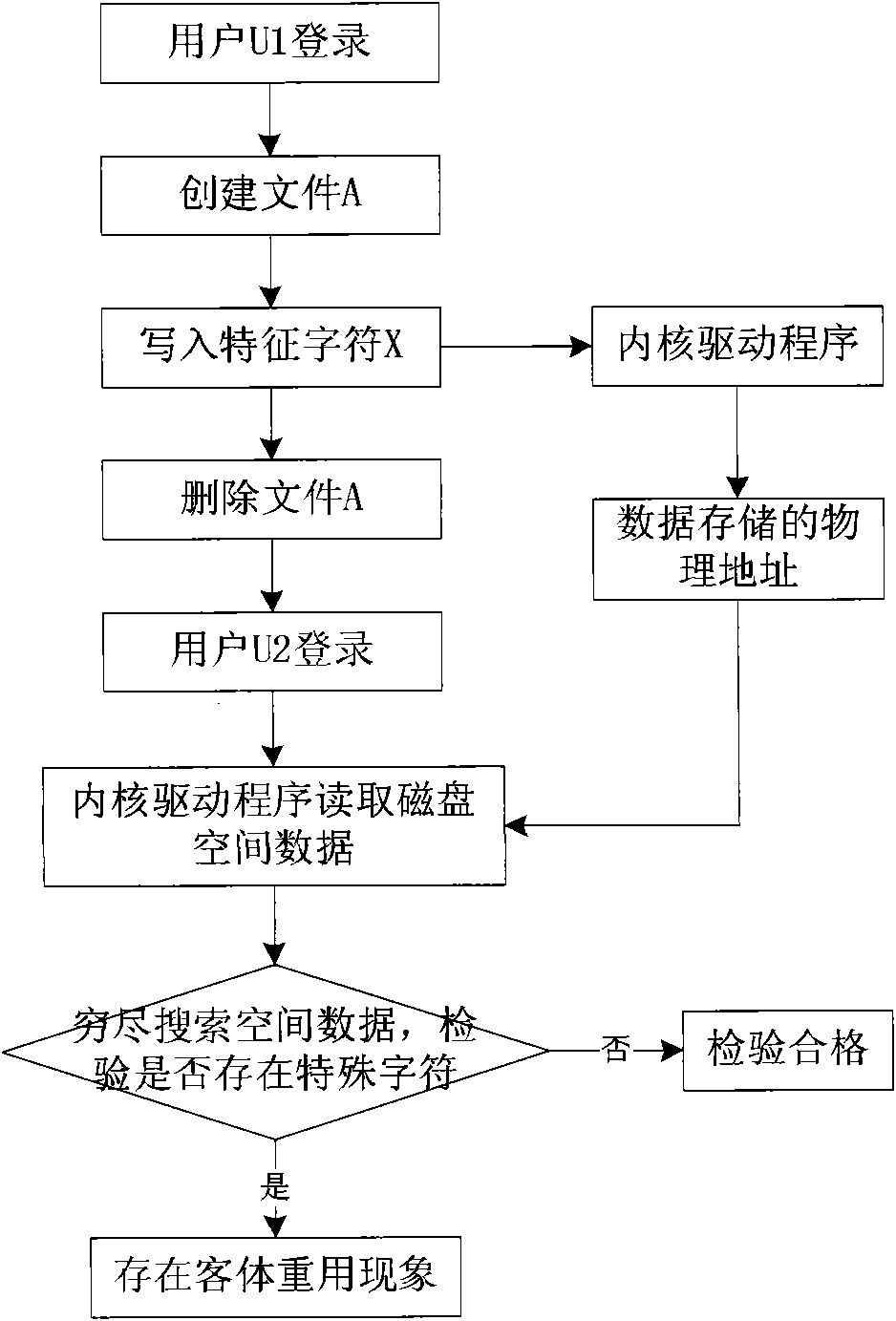
[0027] An exhaustive search-based operating system object reuse inspection method includes a memory space object reuse inspection method and a disk space object reuse inspection method. For the object reuse inspection of memory space, the inspection tool should inspect that when the same physical memory area is used by a process and then allocated to another process, the latter cannot obtain information belonging to the former. For the inspection of disk space object reuse, the inspection tool should inspect whether another user can obtain data belonging to the original user from the disk space after the same disk space is used and released by a file belonging to a user.
[0028] 1. The corresponding steps of the memory space object reuse inspection method are as follows:
[0029] Step 1: Start process A, apply for a memory space for it, and write characteristic characters in it.
[0030] Because the operating system allocates an independent 4GB virtual memory address space f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com