Method and system for realizing integrality protection
An integrity protection and algorithm technology, applied in the transmission system, connection management, network topology, etc., can solve the problem of increasing air interface signaling overhead, avoid modifying the time point of integrity protection configuration, and reduce the air interface load.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
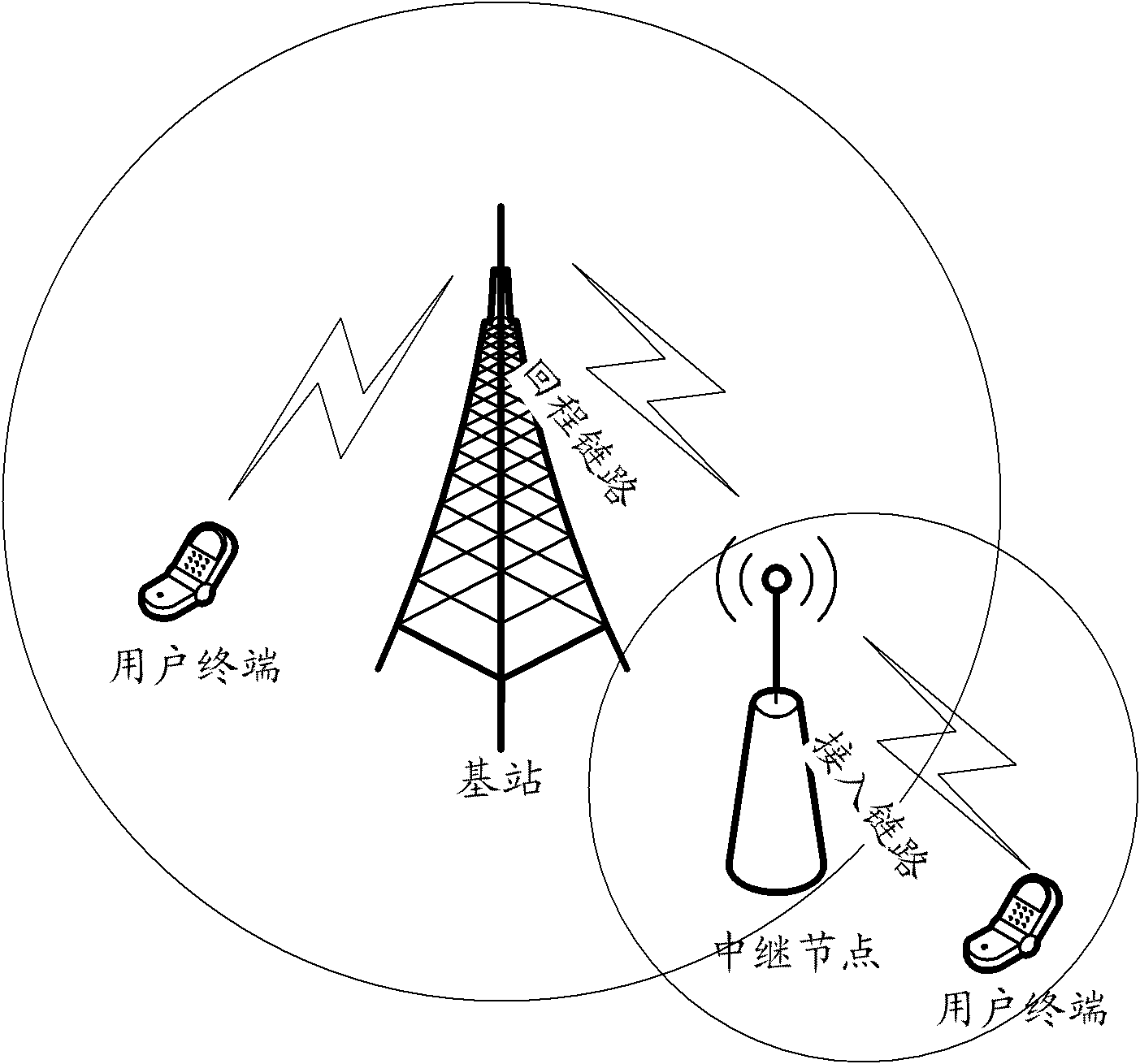
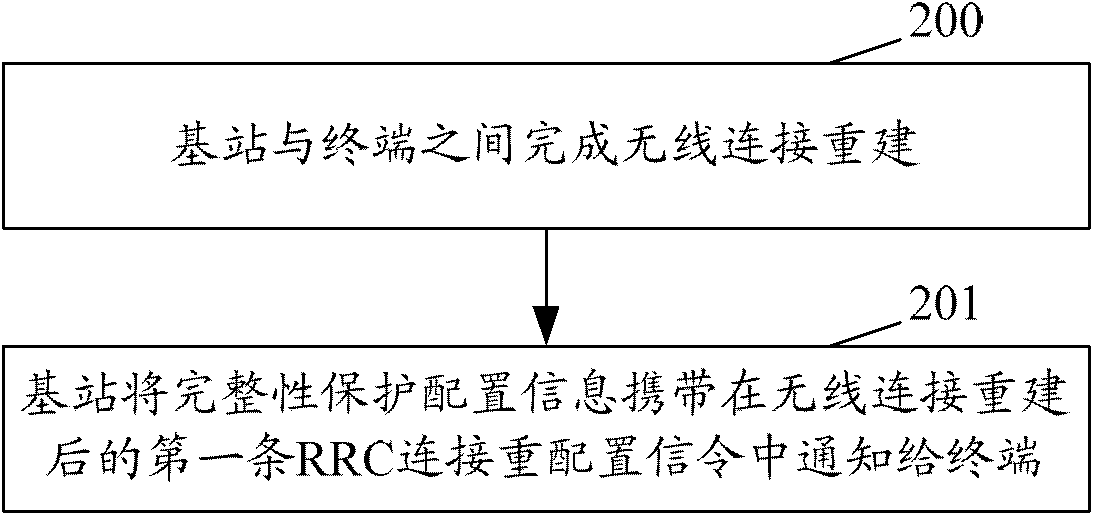
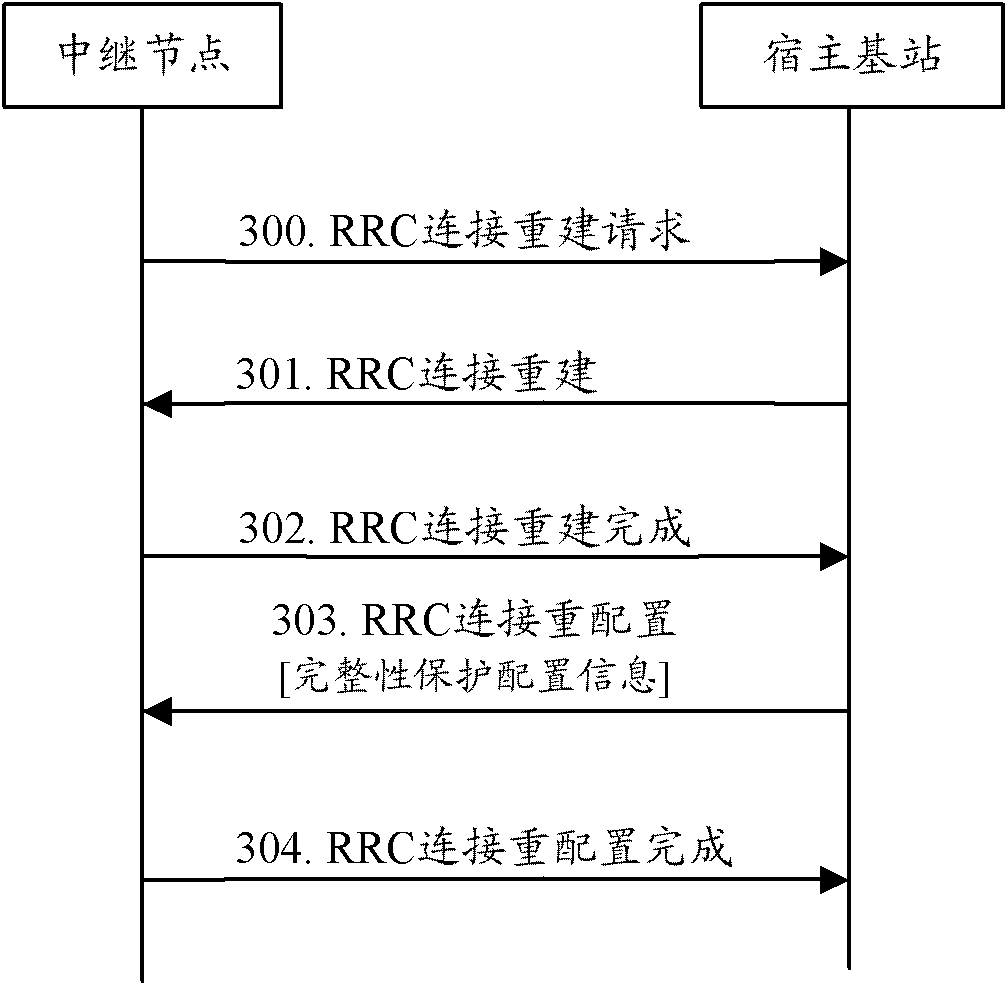
[0042] In the first embodiment, it is assumed that the RN accesses the cell under the jurisdiction of the Donor-eNB and is in a normal working state. On the backhaul link, the Donor-eNB manages the RN like a normal user equipment, and adds, modifies, or deletes the configuration of the DRB for it. , add, modify, or delete measurement configurations for it, establish or release semi-persistent scheduling (SPS, Semi-Persistent Scheduling) for it, and configure MAC layer configuration (MAC-MainConfig) and physical layer dedicated configuration (physicalConfigDedicated) for it Wait. Usually, the Donor-eNB realizes this part of functions through RRC connection reconfiguration. The above configuration content may be sent in one configuration signaling or may be sent in multiple configuration signalings.
[0043] At this point, it is assumed that the donor base station configures three DRBs for the relay node, namely DRB1, DRB2 and DRB3. Among the three DRBs, DRB1 is used to transm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com