International mobile equipment identification inspection method and system for power wireless private network
A technology for international mobile and equipment identification, applied in transmission systems, wireless communications, electrical components, etc., can solve the problems of occupying air interface resources and increasing air interface burden, meaningless occupation of core network signaling resources, increasing terminal attachment delay, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0073] Embodiment 1 of the present invention is that the end user initiates the attachment, and the core network checks that the ME identity is successful and continues the attachment process, which specifically includes:
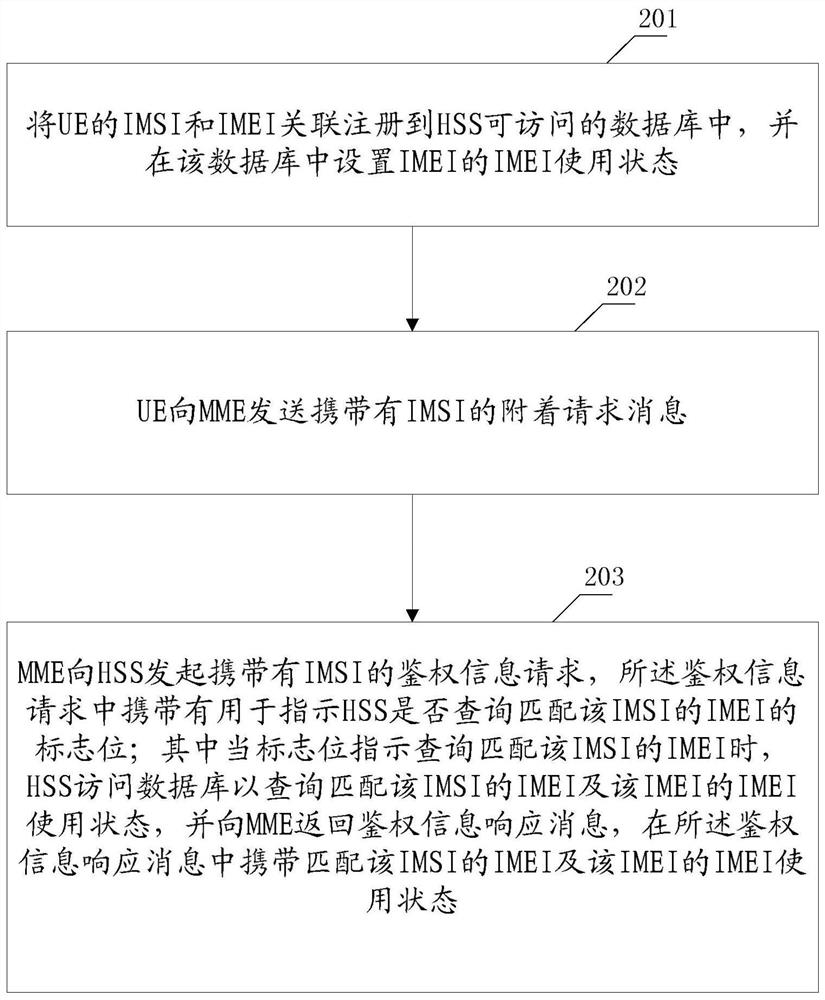
[0074] Step 1: The UE signs the legally matched IMSI / IMEI information in advance, and the IMSI and IMEI information must be unique.
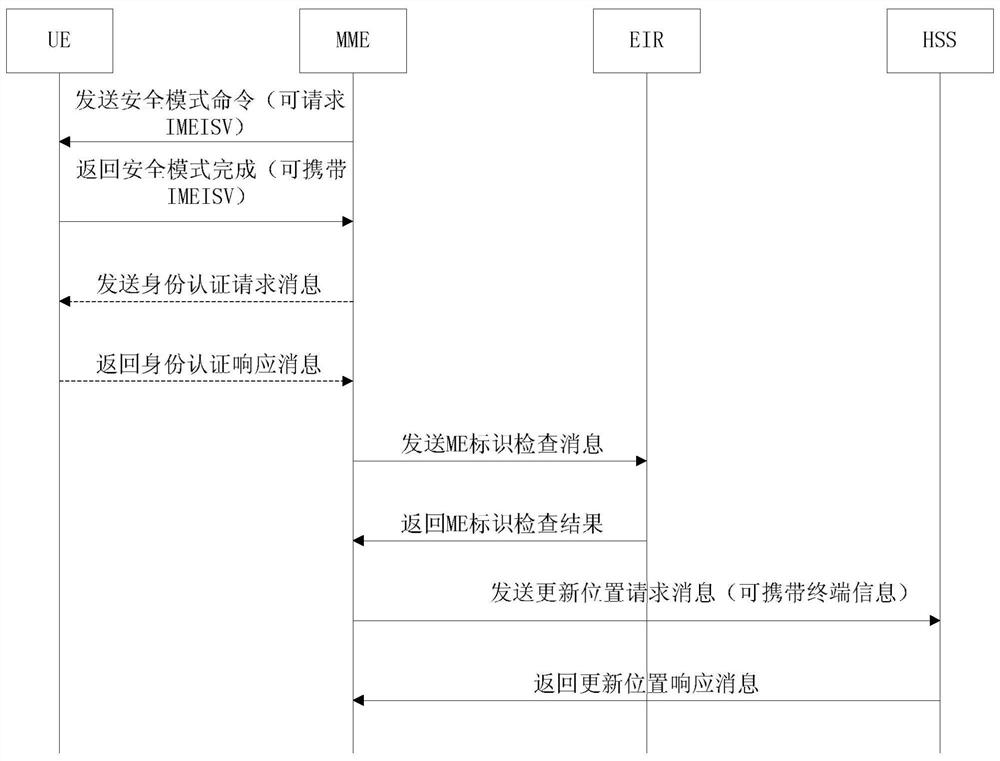
[0075] Step 2: If Figure 6 As shown, the UE sends an attach request (AttachRequest) message carrying its own IMSI to the network side to initiate attach.
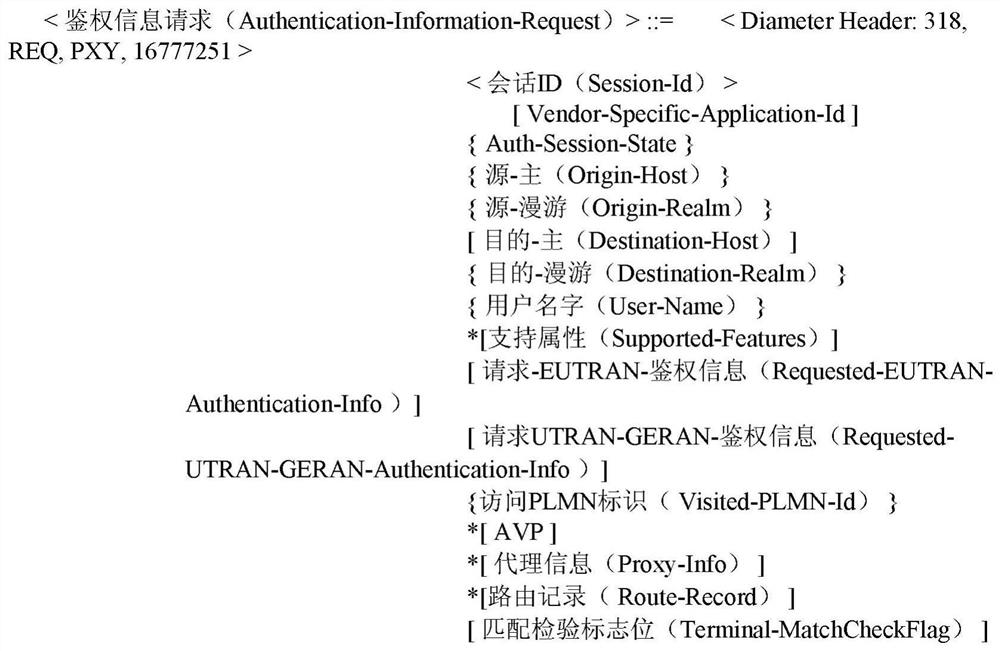
[0076] Step 3: After receiving the UE's Attach Request message, the MME sends an Authentication Information Request (Authentication Information Request) to the HSS. The Authentication Information Request is used to request the authentication vector information of the terminal user, which should carry the information of Terminal-MatchCheckFlag=1 , to instruct the HSS to query the corresponding IMEI information of the user.
[0077] Step 4: The HSS calculates the authenti...
Embodiment 2
[0084] Embodiment 2 of the present invention is that the end user initiates the attachment, and the core network fails to check the ME identity to terminate the attachment process, specifically including:
[0085] Step 1: For known stolen terminals, the IMEI usage status of the stolen terminal should be set to prohibited.
[0086] Step 2: If Figure 6 As shown, the UE initiates an attach to the network side Attach Request (Attach Request) message.
[0087] Step 3: Steps are the same as Steps 3-4 in Embodiment 1, the MME initiates an authentication information request process to the HSS, and the specific process includes: the MME sends an Authentication Information Request (AuthenticationInformation Request) to the HSS after receiving the UE's Attach Request message, and the authentication The authorization information request is used to request the authentication vector information of the terminal user, which should carry the information of Terminal-MatchCheckFlag=1 to instru...
Embodiment 3
[0090] Embodiment 3 of the present invention is that the end user initiates the attachment, and the core network fails to check the ME identity to terminate the attachment process. The specific steps include:
[0091] Step 1: For an unknown stolen terminal, the IMEI usage status of the stolen terminal is still allowed or tracked.
[0092] Step 2: The UE sends an Attach Request message to the network side to initiate attachment.
[0093] Step 3: The steps are the same as steps 3-7 in Embodiment 1. The MME initiates the authentication information request process to the HSS, and initiates the authentication and security establishment process to the UE, specifically including: the MME sends the authentication message to the HSS after receiving the Attach Request message from the UE. Authentication Information Request (Authentication Information Request), the authentication information request is used to request the authentication vector information of the terminal user, which shou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com