Method and system preventing software from copying
A software and software authorization technology, applied in the direction of instruments, program/content distribution protection, electrical digital data processing, etc., can solve the problems of poor security and high cost, and achieve the effect of simple and effective authorization management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
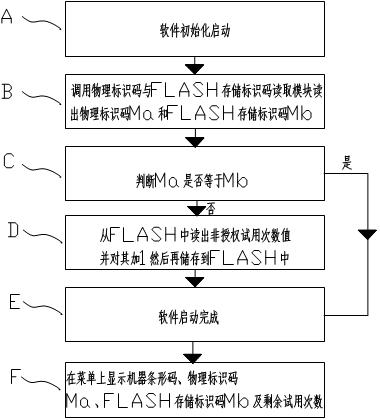
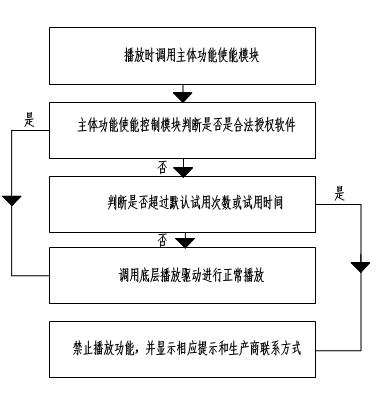
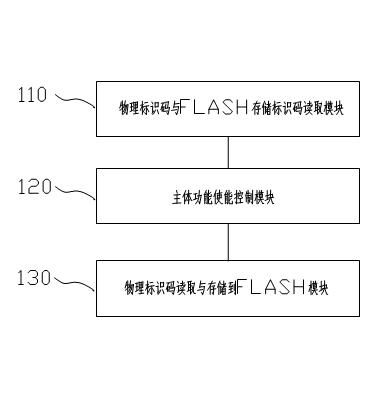
[0047] The present invention provides a method and system for preventing software copying. In order to make the purpose, technical solution and effect of the present invention clearer and clearer, the present invention will be further described in detail below. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0048] Before describing the present invention, it is necessary to explain how criminals realize machine copy board cloning at present: obtain the machine at different stages such as the early prototype stage, factory production stage or finished product market sales stage; for hardware, use its direct visibility to pass The circuit copy board can realize hardware cloning; for the software, it is stored in the FLASH, due to the general requirements of the software upgrade function and cost considerations, these FLASH can be read and written repeatedly, use the stor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com