Anonymous communication path selection method and network node
An anonymous communication, network node technology, applied in electrical components, transmission systems, etc., can solve the problem of failing to meet the requirements of anonymous communication security, unable to ensure nodes on the anonymous communication path, etc., to increase security and reliability. , the effect of not easy to attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
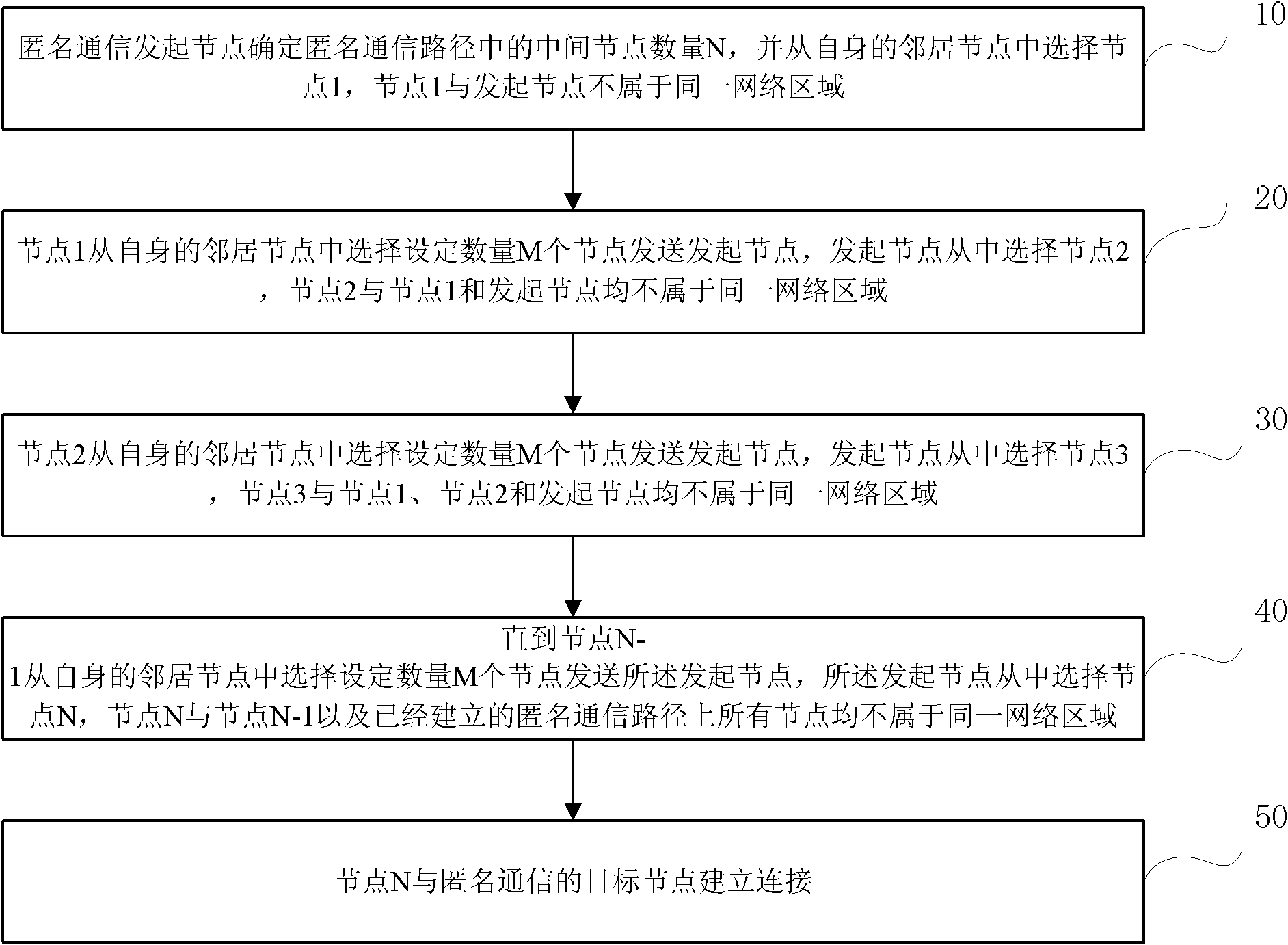
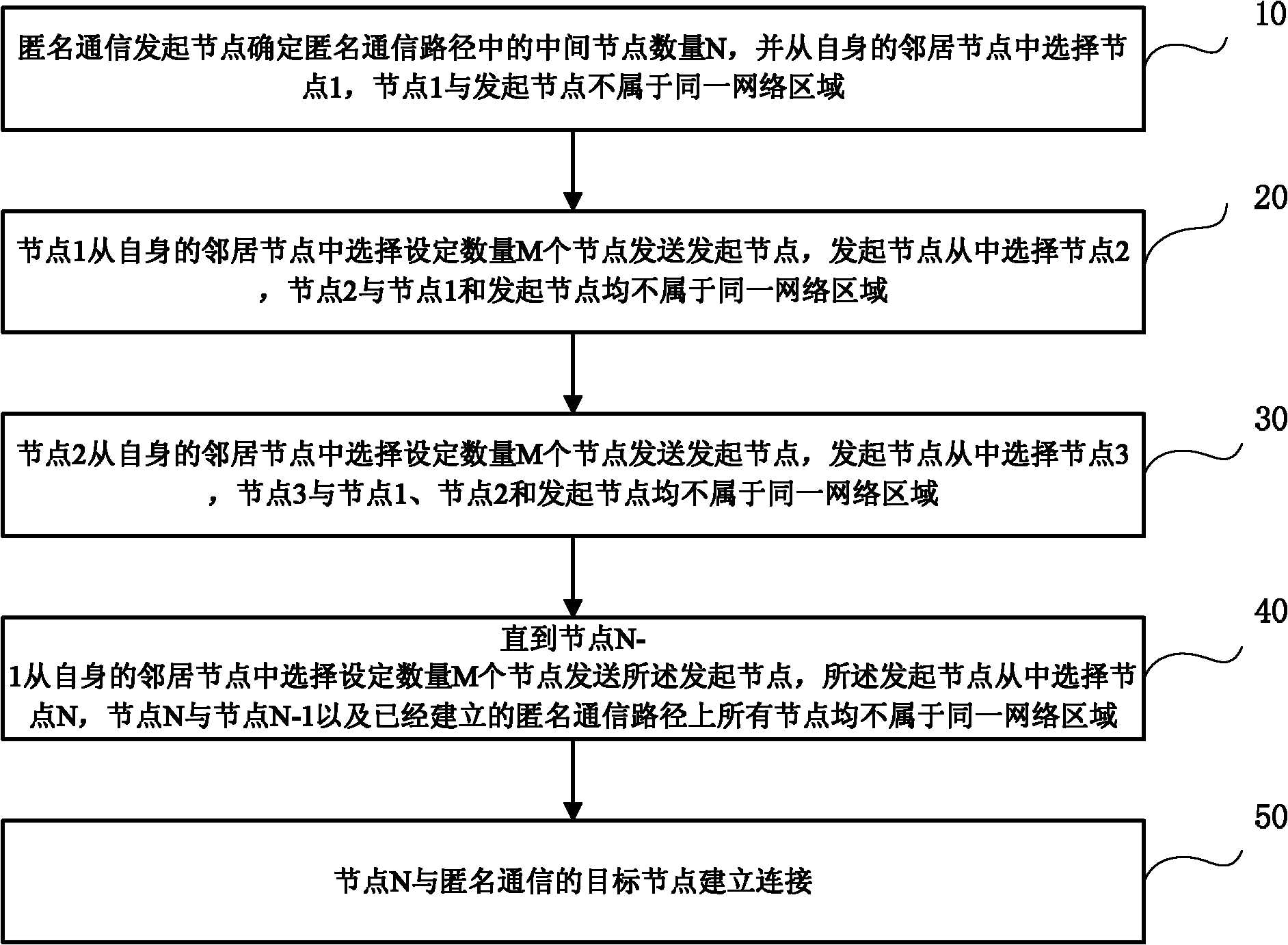
[0044] Such as figure 1 As shown, it is a flow chart of the anonymous communication path selection method provided in Embodiment 1 of the present invention, wherein,
[0045]Step 10, the anonymous communication initiating node determines the number N of intermediate nodes in the anonymous communication path, and selects node 1 from its neighbor nodes, and node 1 and the initiating node do not belong to the same network area.
[0046] Here, if an anonymous communication initiating node wants to initiate anonymous communication, it first needs to determine the number N of intermediate nodes in the anonymous communication path according to the specific requirements of anonymous communication, and use this number N to control the overall number of nodes in the anonymous communication path. is the length of the path. The intermediate nodes here only include all other nodes in the entire anonymous communication path except the initiator node and the target node.
[0047] After tha...
Embodiment 2
[0065] In the above-mentioned embodiment 1, the initiating node selects node 1, and node 1 selects some nodes from its own neighbor table, which can be 2, 3, or 4, etc., but at least 2, can be set to M. It is required that the M nodes themselves are located in different countries, regions, ISPs, etc., and the M nodes are located in different countries, regions, or ISPs from the initiating node and node 1 . The initiating node selects one of the received M nodes as node 2. Node 2 is required to be located in a different network area from Node 1 and the initiating node.
[0066] By analogy, when node i selects the next node, node i selects M nodes from its own neighbor nodes, and requires that these M nodes are located in different network areas from node i and node i-1 (here, only the following A node is located in a different network area from node i and node i-1, because node i only knows node i-1 and the network area it is in when selecting, and node i cannot know the other...
Embodiment 3
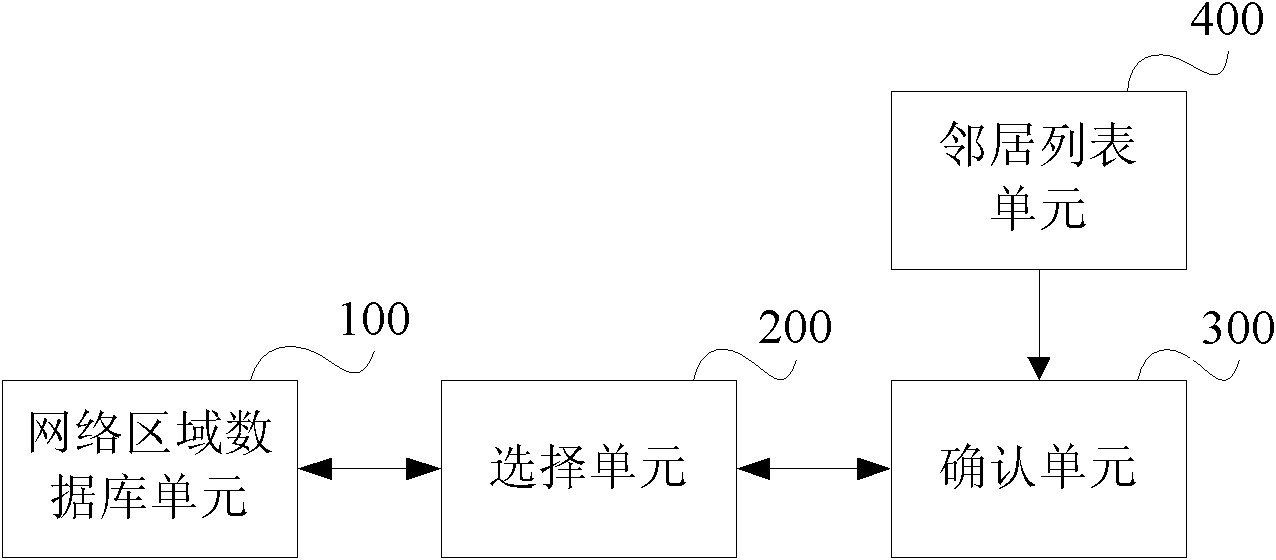
[0068] In order to ensure the establishment of an anonymous communication path, according to the principle of anonymous communication, each node in the network needs to maintain a network area database. When each node in the anonymous communication path selects the next node, it sends the information of M next nodes to be selected to the anonymous communication initiating node, and the anonymous communication initiating node selects the next node.
[0069] Here, the anonymous communication initiating node controls whether to select a node as the next node of the anonymous communication path. When each node selects the next node, it needs to send the information of the M next nodes back to the initiating node. node selection.
[0070] The information sent back by each node to the initiating node may include information about the network area to which the selected next node belongs, and the initiating node only needs to determine whether it belongs to the same network area as al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com