Strategy adaptation system and method based on SELinux (Security-Enhanced Linux) security subsystem
A subsystem and strategy technology, applied in the field of Linux operating system, can solve the problem of difficult to write and maintain the source code of strategy files, achieve the effect of flexible and convenient collection work, reduce the generation of loopholes, and reduce the load of the system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
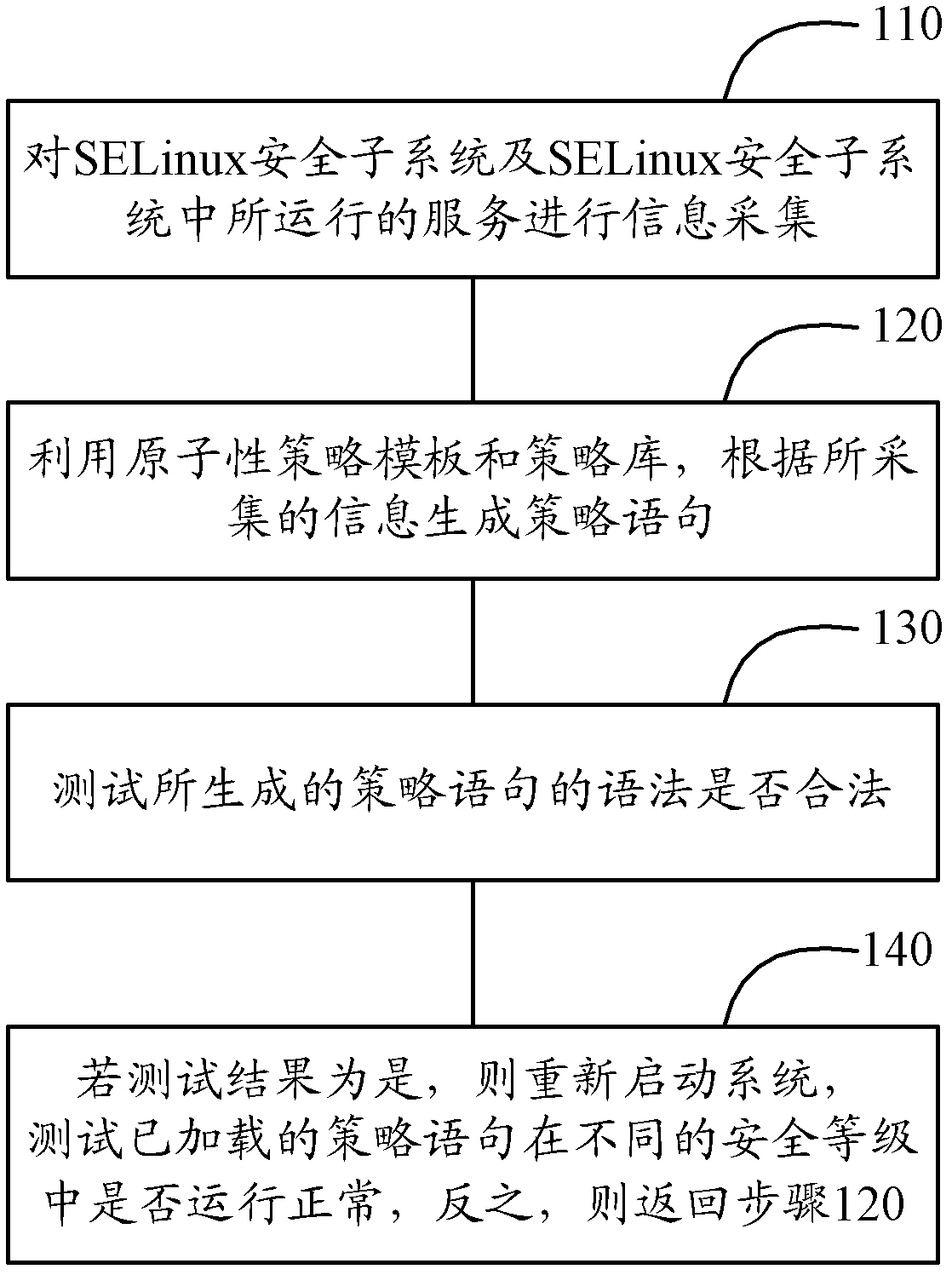
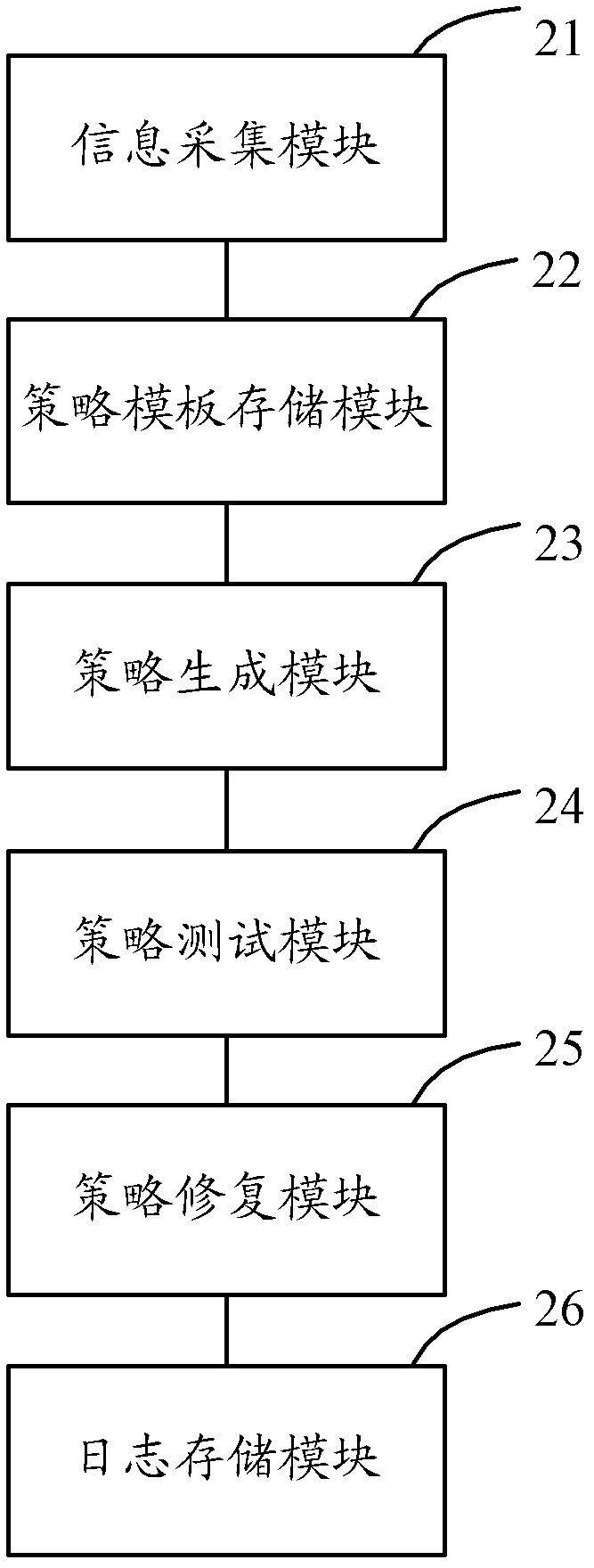
[0091] figure 2 It is a schematic structural diagram of the policy adaptation system based on the SELinux security subsystem according to the second embodiment of the present invention, and each component module of the embodiment is described in detail below.
[0092] The present embodiment comprises information collection module 21, strategy template storage module 22, strategy generation module 23, strategy test module 24, strategy repair module 25 and log storage module 26, and information collection module 21 is connected with strategy template storage module 22, and strategy template storage The module 22 is connected to the policy generating module 23, the policy generating module 23 is connected to the policy testing module 24, the policy testing module 24 is connected to the policy repairing module 25, and the policy repairing module 25 is connected to the log storage module 26. Next, the functions of each module will be described in detail.
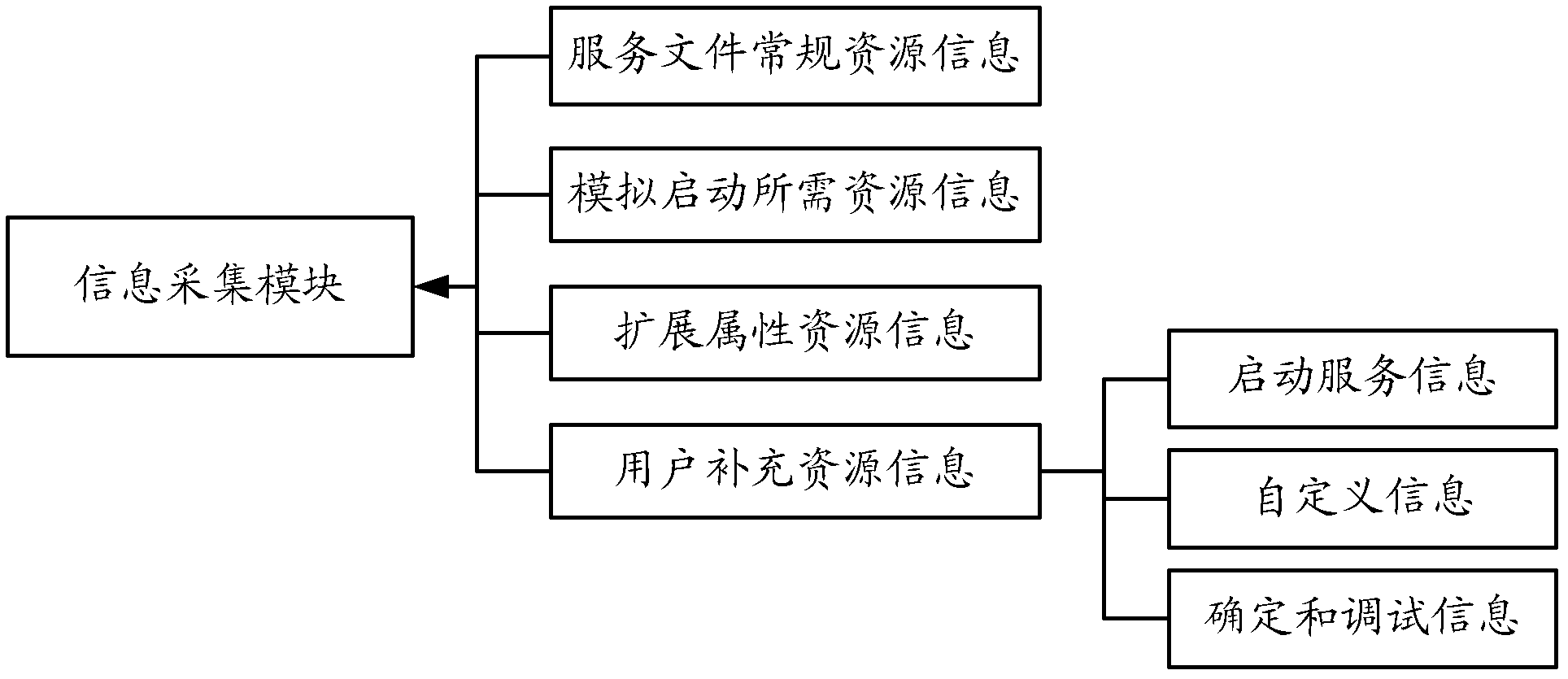
[0093] The information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com